DeepRay alarm: attacks on German customers
At noon on 13. April 2020 our monitoring system created an alert because DeepRay reported more hits than usual for one particular detection on PowerShell downloaders. The alarm system is there to see early if something goes wrong. However, this alarm went off because of a spam campaign hitting our German customers. The detections were all legitimately preventing the malware downloader from doing it's job.
We investigated the threat and also found BEAST-related entries which showed that the culprit were Excel documents delivered by email. While we do not receive the Excel or email documents themselves, we do see infection chains reported by BEAST for those customers that agreed to the Malware Information Initiative (Mii).
Infection vector: Delivery email with Excel attachment
The malicious email claims to be from DHL, a courier, parcel and express mail service in Germany. It says that the delivery address of a recent order cannot be found and that the recepient should add information to an attached document. A screenshot of an email is shown in this German article that warns about malicious Macros, which we found to be describing the same threat because of the IOCs.
A lot of people are currently getting deliveries due to Corona related lockdowns of shops, which is probably why the threat actors chose this way to deceive the user.
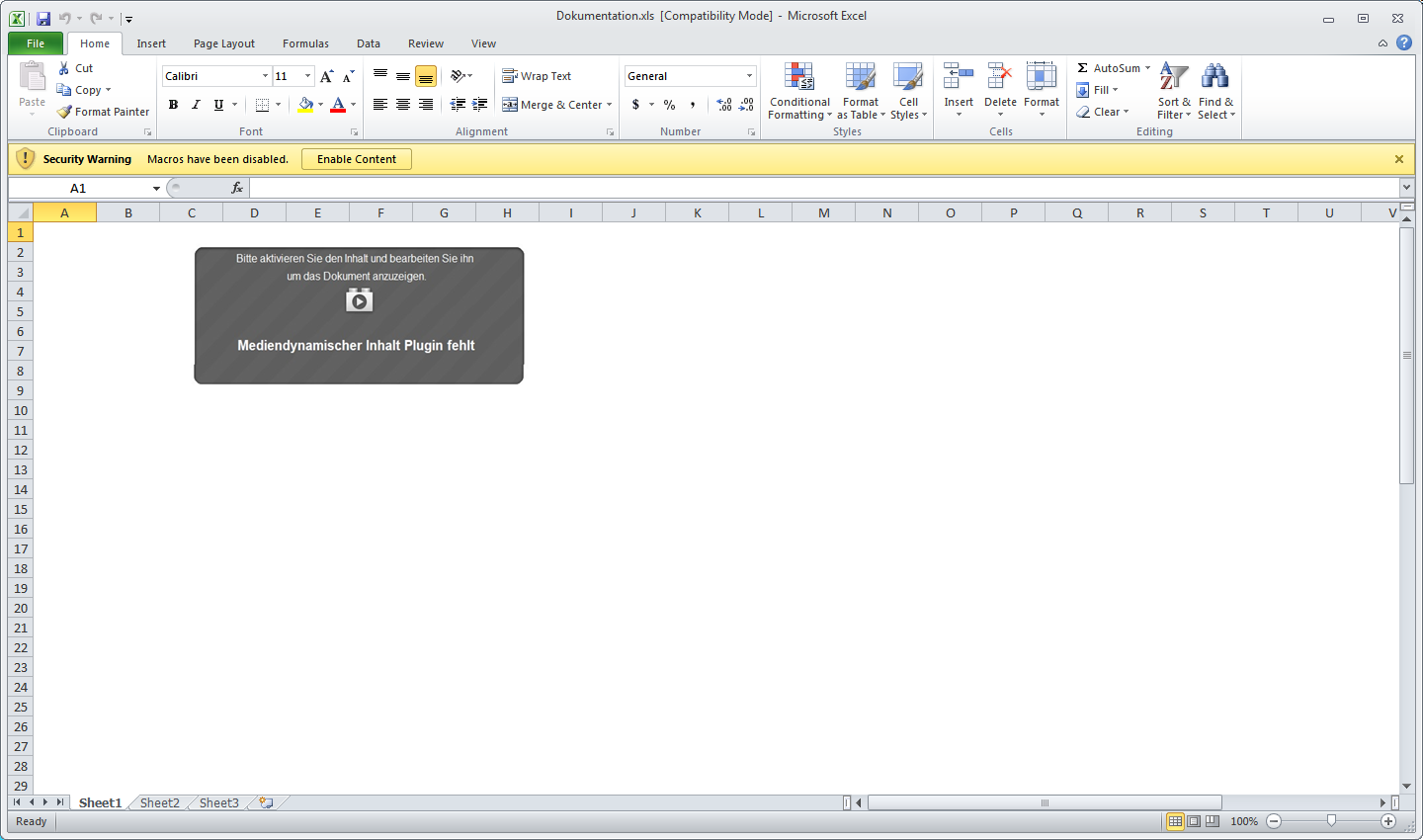
The document has the name Dokumentation.xls[1]. After searching for threats via Google, we found a sample on Virustotal that fits to the ongoing campaign. If opened it shows an image that requests the user to activate Macros in order to show the contents.
One of those text files[4] is seen on the left hand side below. Here the characters '@@' will be replaced by '44' and '!' by '78'.
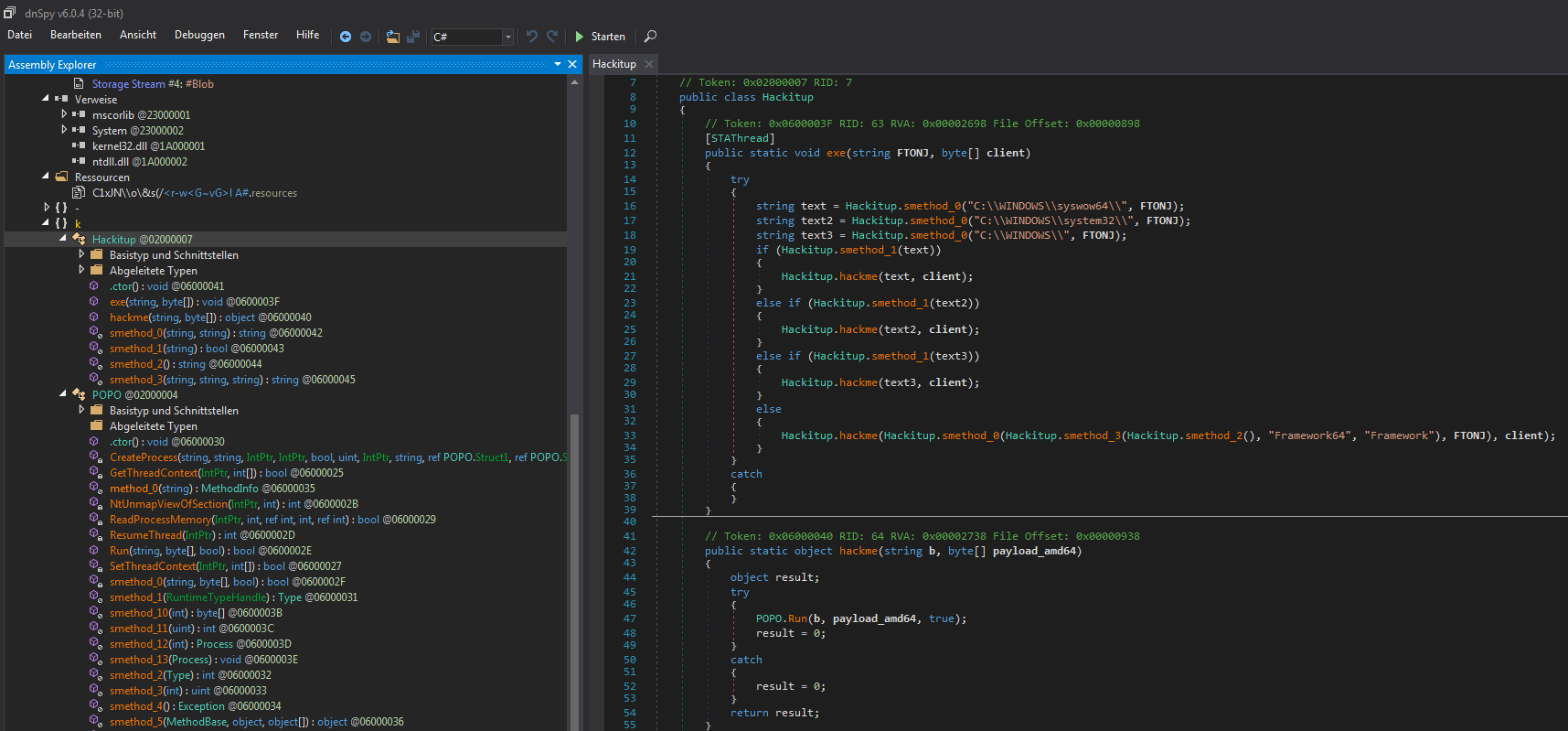
After character replacement and converting the integers to bytes, a second obfuscation layer[5] becomes visible (image on the right side). This layer only has 'N' prepended to all byte values. Decoding it reveals the last layer, which is a .NET DLL called Hackitup[2].
Hagga delivers NetWire RAT
The other file downloaded from paste.ee is an obfuscated but non-packed NetWire[3] sample. Netwire is a wide-spread remote access malware.
The aforementioned .NET DLL Hackitup[2] performs process injection for a given file. The PowerShell command calls this DLL to inject NetWire[3] into MSBuild.exe.
This kind of PowerShell downloader is typical for Hagga aka Aggah campaigns as described in this Azorult article.
Takedown of paste.ee pastes stopped the campaign
After I had tweeted about the ongoing campaign, researcher @JayTHL requested the paste.ee sites and reported them. They were taken down a few minutes later, effectively stopping payload delivery.
Indicators of Compromise
| Description | Filename | SHA256 | Detection |
|---|---|---|---|
[1] Excel attachment | Dokumentation.xls | 67fd76d01ab06d4e9890b8a18625436fa92a6d0779a3fe111ca13fcd1fe68cb2 | Trojan.Agent.EQQI |
| [2] .NET Injection DLL | Hackitup | bb37f30311a0ade4a807a5de7f078efd6b3af815aa4305a4bcc17f6d4b5ee9e6 | MSIL.Trojan.Injector.OX MSIL.Trojan.Injector.OY |
| [3] NetWire | MSBuild.exe | cdd2e26792bd7ee81a6297d13dd514836778620c9bd96e79ae6ee26239c546b1 e8edf64d02ed7f0456b8f1601026ce37f9120d3a1d1e9ba7fdc8d9bc8bf10d10 | Win32.Trojan.Netwire.C |
| [4] Obfuscated Hackitup Layer 1 (raw paste.ee download) | f3764f7cd5b1f27e1d921b4f7eb229482652a317a27193824207da051943a2c8 | ||
[5] Obfuscated Hackitup Layer 2 | f92db2c4401d5da1e1f68a4ec1fb159c34fc7f020e4fbacca3e4682db0a5bbe2 |
| URLs |
|---|
| paste .ee/r/e49u0 |
| paste .ee/r/dlOMz |
| paste .ee/r/gTYWf |
| paste .ee/r/rHoL5 |