Last year, we blogged about the Rozena malware and how this backdoor incorporated PowerShell to execute its shellcode. However, malware authors are not sticking to the same script, constantly modifying and updating their attack methods. This time we’ve observed a new malware that used server-side polymorphism to hide its payload, which is a backdoor that is fully written in PowerShell.
Initial Attack Vector
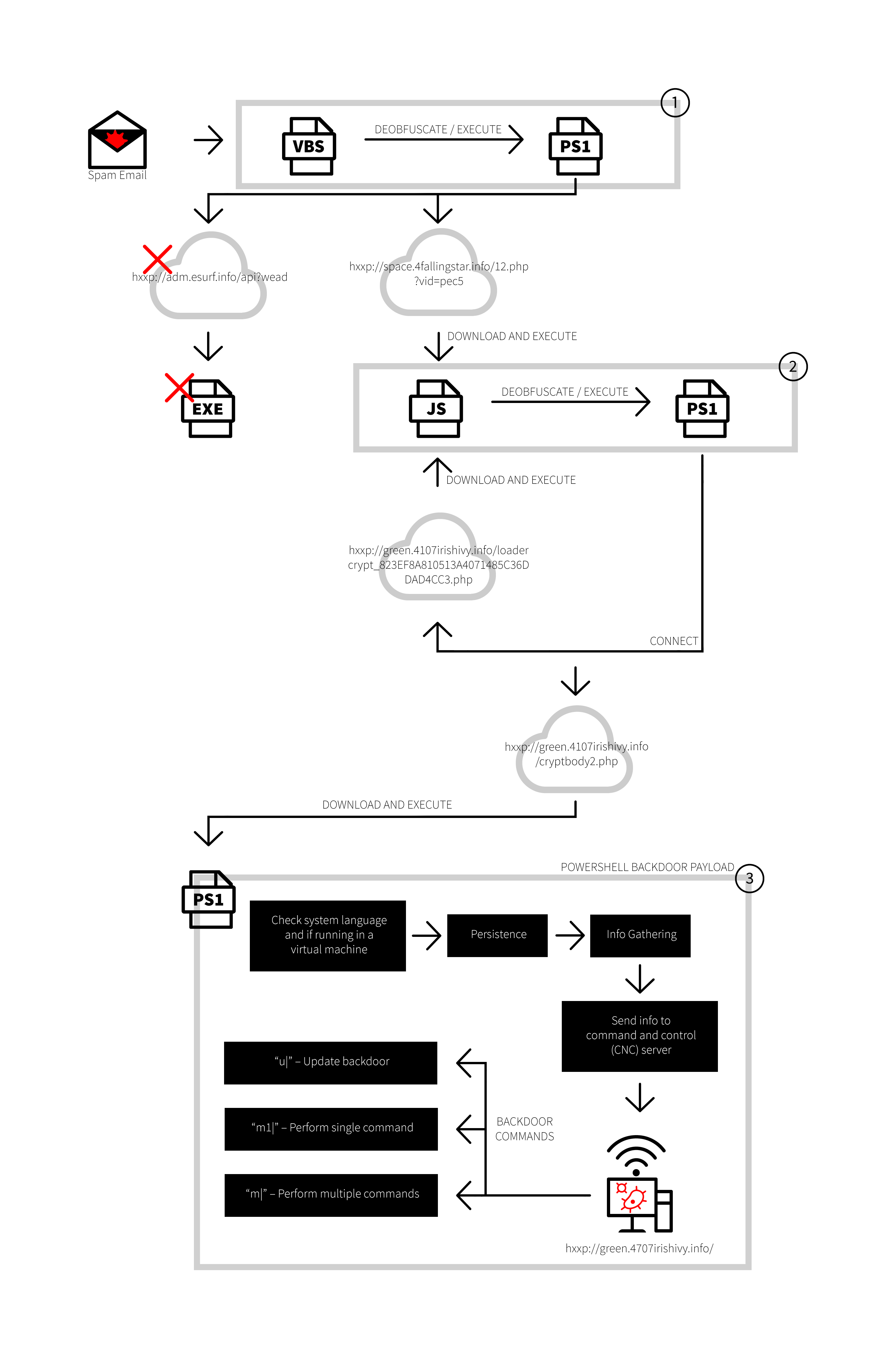
The sample was obtained as a malicious Visual Basic Script (VBS) attachment from an email, with the file named as “INAIL_Comunica_133113944054522074634191697732.vbs”. By the looks of its filename, it claims to be a notice from an Italian organization for workplace safety insurance called the Istituto Nazionale Assicurazione Infortuni sul Lavoro (INAIL).
Upon execution, this malicious VBS will invoke a downloader written in PowerShell that downloads two files from its command and control (CNC) servers:
hxxp://adm.esurf.info/api?wead (SkypeApp64.exe)
hxxp://space.4fallingstar.info/12.php?vid=pec5 (SearchI32.js)
While the URL of the file SkypeApp64.exe was already down as of analysis, the sample remains malicious even without the executable. The CNC server that hosts the file SearchI32.js has server-side polymorphism, in which the hosted JavaScript (JS) files are modified each time they are accessed, making static detection difficult.
The file SearchI32.js is an obfuscated JS that invokes another PowerShell downloader that will again download two files, which are both saved in the default Windows temporary folder %temp%:
hxxp://green.4107irishivy.info/cryptbody2.php (SearchI32.txt)
hxxp://green.4107irishivy.info/loadercrypt_823EF8A810513A4071485C36DDAD4CC3.php (SearchI32.js)
Backdoor Downloads
SearchI32.js downloads and executes a new version of itself as a form of persistence. At first glance, the file SearchI32.txt looks like junk. However, it is decrypted and executed by the JS file, and is the main PowerShell backdoor.To skip several deobfuscation stages for unveiling the backdoor, we used the PowerShell Extractor Analyzer (PEA), a publicly-available tool developed within G DATA to analyze SearchI32.js.
The first part of the code consists of evasion techniques. The backdoor will first try to check if the infected system’s language is Russian, Ukrainian, Belarusian, or Chinese, and if the system is running under VirtualBox or VMWare (suggensting it is analyzed in a virtual environment - a technique often employed by malware analysts), terminating the execution if either check is matched:

As part of its persistence, it also adds a shortcut file on the startup folder. The shortcut links to the downloaded SearchI32.js, with a description of “Windows Indexing Service” to throw off the user from its malicious behavior. The command-line script host cscript.exe is then used to execute the Searchi32.js.

The backdoor will then create a System.Net.CredentialCache object to store the obtained information from the user. This object will be used as for downloading commands from the CNC server and at the same time posting the victim’s information. The collected information is comprised of:
- $bot_id– Created ID for the victim that contains the computer name, computer model, and disk drive signatures
- $bot_os– Operating system build version
- $ver– Backdoor version
- $psver– PowerShell version
The backdoor will use the DownloadString method to obtain the body of the CNC server site, parsing the content for its backdoor commands. The CNC server site body is expected to contain the commands in this form:
[command]|[URL for the malicious PowerShell script]
The backdoor will repeatedly access its CNC server and wait for one of the following the commands:
- m1 – Single command execution. Downloads a single string of URL from the CNC and executes it.
- m – Multiple command execution. Downloads multiple strings of URL from the CNC and executes each string.
- u – Downloads and executes an updated version of SearchI32.js and SearchI32.txt from the CNC server.
For the m1 and m commands, the URL being downloaded will contain the PowerShell script to be executed for its malicious activity.
We encountered the backdoor updating several times through its commands, like
u| hxxp://green.4107irishivy.info/cryptbody2.php|hxxp://green.4107irishivy.info/l2.php
and
m1| hxxp://red.340airport.com/u2
The latter of which was the latest URL as of writing, where the JS decryptor/loader and PowerShell backdoor scripts were completely updated. The CNC server domains were updated during analysis (e.g. hxxp://green.4107irishivy.info/ to hxxp://green.4107irishivy.info/), making this campaign difficult to detect.
The updated version of the backdoor is still similar on how it receives its commands from the CNC server, but had some several updates in its script:
- Adds the updated JS file to the scheduled tasks using the Windows task scheduler (schtasks.exe), for persistence.
- Dropping location of downloaded files has been changed from %temp% to %appdata%\Roaming\Microsoft
- Usage of a domain generation algorithm (DGA) when it fails to connect to the main CNC server.

Defense is easy
Since this malware uses email attachments as the initial attack vector like many other types of malware, it always pays to be safe by validating the source of any emails sent to you that contains attachments or links to downloads. Never open attachments or links from unvalidated email addresses. Always keep your anti-virus and operating systems up to date, to ensure your systems are protected against these new types of malware.
If you are interested to know more of the in-depth analysis of this backdoor campaign, you may visit the following link:
Indicators of Compromise
- URL that attempts to download the executable:
- hxxp://adm.esurf.info/api?wead
- JS script:
- Sample hashes:
- d3089f023d0715058773ea0cec037f92a5ce52958fdfe56b53ab291b343cee4f (Initial download of SearchI32.js)
- 20317970e11e1dbdc3142b1c4fdf7258ec2d6cb29ac7d2a5ec21ef8eff38ebcc (Succeeding download of SearchI32.js)
- URLs:
- hxxp://space.4fallingstar.info/l2.php
- hxxp://green.4107irishivy.info/loadercrypt_823EF8A810513A4071485C36DDAD4CC3.php
- hxxp://red.1407cty13pec.com/l2.php
- hxxp://sad.childrensliving.com/l2.php
- Sample hashes:
- Obfuscated PS1 backdoor:
- Sample hash:
- 1c9d3bcea90d3ac24cef4302fa081d8f6e50a580a74d204923ee9491f0008c6e (SearchI32.txt)
- URLs
- hxxp://space.4fallingstar.info/cryptbody.php
- hxxp://green.4107irishivy.info/cryptbody2.php
- hxxp://red.1407cty13pec.com/cryptbody.php
- hxxp://sad.childrensliving.com/cryptbody2.php
- Sample hash:
- Other URLs that were used by the malware:
- hxxp://stats.emeraldsurfwatermanagement.com
- hxxp://green.dddownhole.com
- hxxp://green.nogel.tech
- hxxp://red.340airport.com
- hxxp://wws.rheovesthr.com
- hxxp://red.1407cty13pec.com