Imagine you run a marketing agency. One day you discover that not only is your business account on Facebook blocked, but a significant amount of money has been charged to your company credit card. This is exactly what has happened to some marketing agencies. We would like to take a closer look at one such case here.
Social Media = Advertising
By now, everyone knows that Facebook and other social media platforms are financed by advertising. Companies can display ads on these platforms to promote their products and services. The more money you invest in an advertising campaign, the more often it is shown and the more people see it. So here, money is directly synonymous with reach.
Criminals also know this and try to profit from it. But instead of creating accounts themselves and risking a block on their own accounts, they hijack other people's business accounts for their own purposes. If these are blocked, the perpetrators are not bothered, and they look for their next victim.
Baited
In order to contact their future victims, the direct messaging function of the respective platform is used, among other things. In one case known to us, the perpetrators appear as representatives of a well-known and reputable company that is looking for advertising partners and marketing expertise. In this example, they are primarily targeting marketing agencies with this scam. Such requests are not uncommon in this industry. This initial contact has taken place on July 13.
The language is largely free of errors and sometimes very high budgets are promised. Detailed information is listed in a document, which the addressees are supposed to download. Thefile was downloaded on July 19.The link leads to a ZIP file stored in the cloud storage service Microsoft OneDrive. This page is harmless in itself and is also used for legitimate purposes. The downloaded file is protected with a password, which is also mentioned in the direct message. The perfidious thing about it is that a password-protected file cannot be scanned by malware protection.
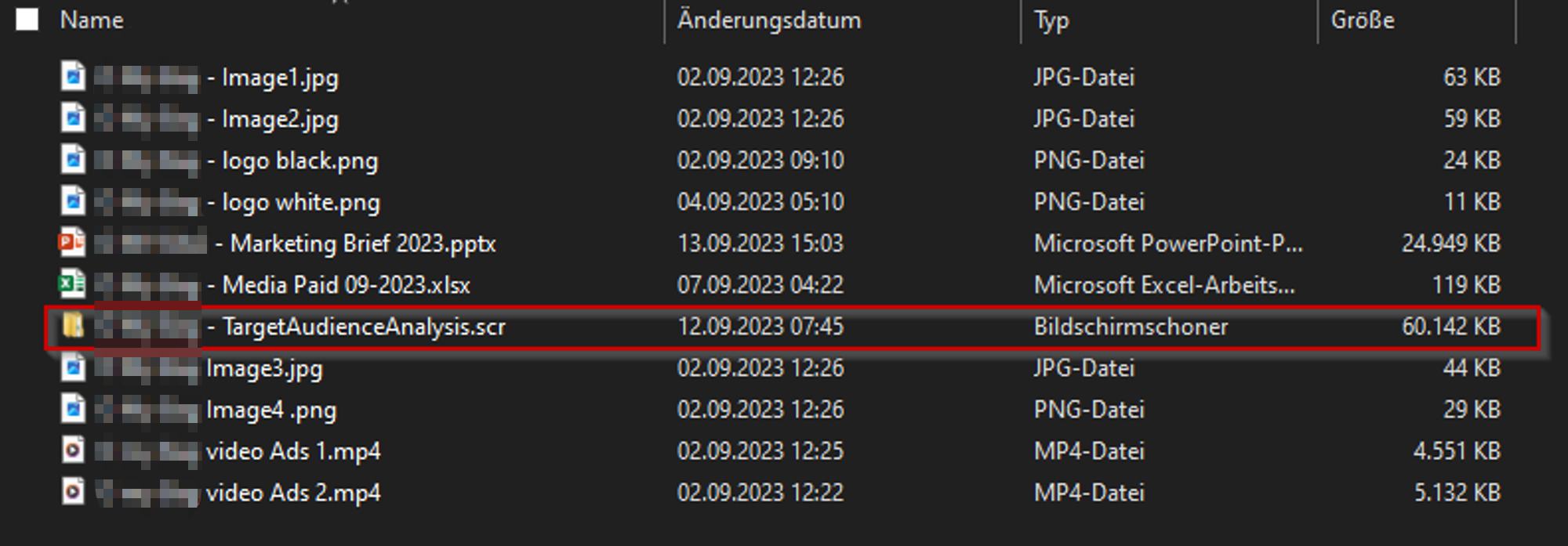
After opening and unzipping the archive, there are several files to be seen - including several graphics and some Office files. These can be opened safely as well - they appear to be genuine, or at least give the impression that they are legitimate marketing materials. These files did not contain any malicious code. However, there is a single file among the total eleven files that actually contains malicious code. The sneaky thing about it is that the icon of the file makes it look like the user is double-clicking on it to open a file folder.
Hooked
Anyone who opens the file practically serves the criminals access on a silver platter.
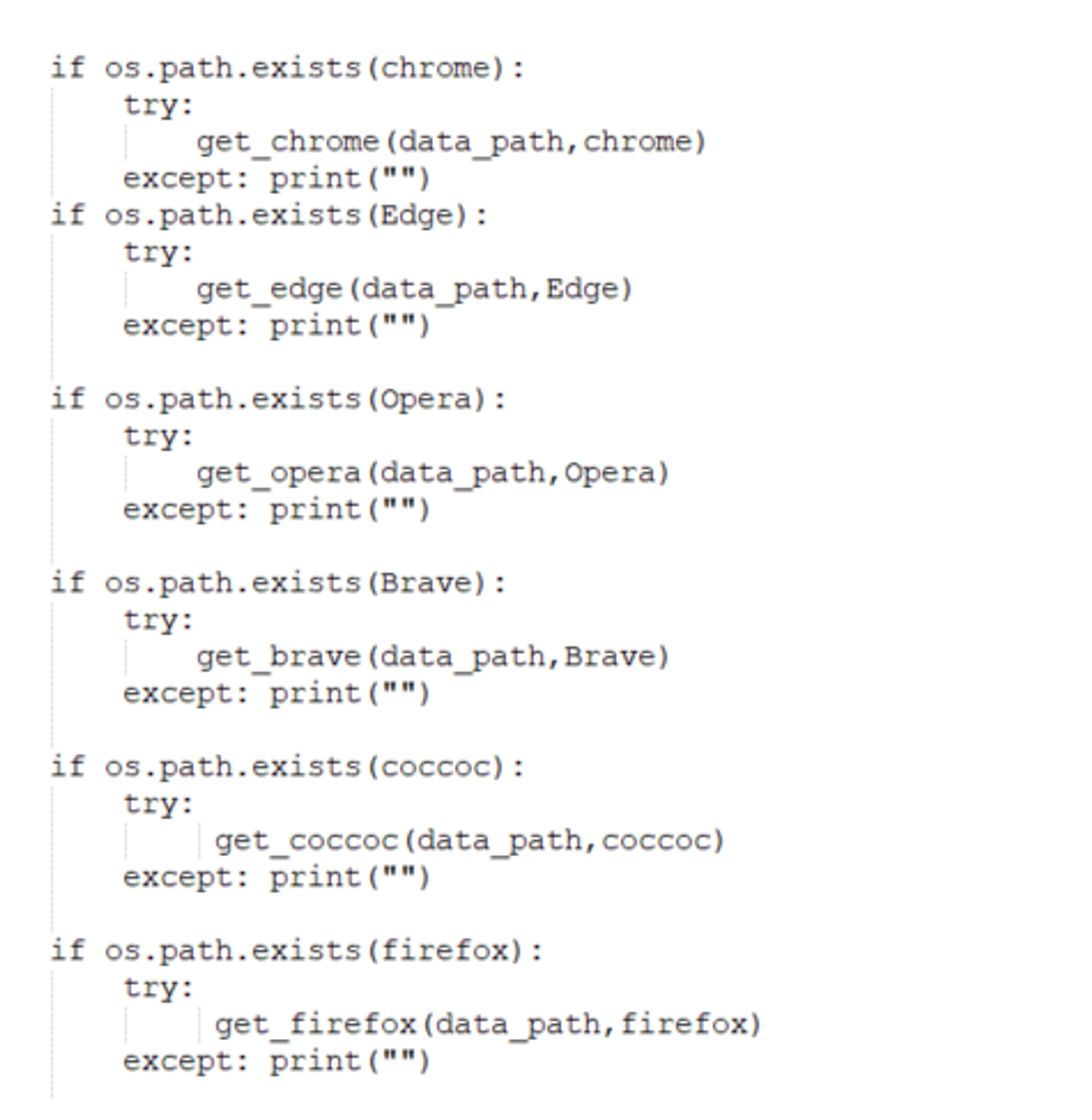
The downloaded and unzipped document ensures that a multi-file script is downloaded and executed unnoticed by the user. This script specifically steals the so-called session cookie for the Facebook account s from the browser. Access data stored in the browser via the "remember password" function and screenshots of the browser window are also leaked. In doing so, the malware is flexible and also reads the password and token stores in Chrome, Edge, Opera, Firefox, Brave and a browser called Cốc Cốc that is primarily used in Vietnam.
The stolen data is sent to a Telegram bot that is under the attackers' control.
At the same time, the malware creates a batch file with a randomly chosen name under C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ so that the spy is started with every system startup. Experts refer to this as "establishing persistence".
Session Token
A session token is basically the browser's "ID card" that is requested by a website such as Facebook. If the token is valid, the website assumes that the browser - and by extension, the user in front of the computer - is authorized to access the content. Unfortunately, these tokens can also be copied and used from another computer. This is what the criminals are counting on. Whoever has the token has unrestricted access to the respective account.
Users on other platforms have also lost access to their own accounts in this way - even though some of the accounts were protected with multi-factor authentication and a strong password. In other words, the attackers do not even have to steal passwords or trick multifactor authentication.
Fleeced
Once such an account has been taken over, the attackers in our case exploit several things for themselves in order to distribute their own content - for example, fake stores or malware downloads - unsuspecting users: on the one hand, they use the awareness of the taken-over account. On the other hand, they start booking their own advertising campaigns with payment information stored in the account. These can be controlled in a very targeted manner. Advertisers can target a very narrow audience, which can also be narrowed down geographically - for example, "men between 18 and 35 from the Munich region."
The ads placed can contain many things, from fraudulent bait-and-switch offers where customers order and pay for goods that are either never delivered (or customers receive goods of inferior quality), to phishing pages, to hidden malware downloads.
The affected parties are often left to bear the costs. In this case, the agency in question was lucky and the debited amount of almost 1,000 euros was almost fully refunded. However, one should not rely on this always being the case. The damage has been done, however: Unwanted content was spread, seen and potentially clicked on in the name of the attacked company with a large number of users. And depending on the content of the unauthorized ads, other people lost money as a result. But that's not all: the account is completely in the hands of the perpetrators for the time being and the actual account owners are locked out. The lockout took place on September 28.
The criminals potentially had had access to the Facebook acount for about 40 days at this point. This is also not too uncommon, because if the account is taken over right when opening the malicious file, this might raise suspicion. So anyone affected by this might at that point not even remember having received the malicious files.

Collateral Damage
In the case described here, there is an additional factor:
The perpetrators pretended to act on behalf of a specific brand. The brand, a handbag manufacturer, actually exists in this case. When asked, an employee of the company confirmed that the message received was not authentic and that they are currently making efforts to have the accounts used by the scammers deleted. They also point out that they themselves only send messages from a specific address/domain.
Strictly speaking, therefore, there are at least two directly injured parties here: on the one hand, the company whose account was taken over, and on the other hand, the company whose name was misused to commit the crime.
Effective protection - with a catch
Protecting yourself from this type of attack is easy and difficult at the same time. Perpetrator groups are very good at choosing a suitable form of address that is normal for the respective target person and does not arouse any suspicion. On the other hand, they use OneDrive for their malware, a service that is also used hundreds of thousands of times for completely legitimate purposes. The links containing the prepared archives are still online several days after our analysis and are most likely still actively used.
However, they also take advantage of the fact that many users are very comfortable. In most cases, not only private users, but also people who manage business accounts are permanently logged into the site in the browser. Those who are permanently logged in have a session token stored, which theoretically has no expiration date. This means that you don't have to log in and re-enter your password every time you visit the site. The option that activates a permanent login is called, for example, "Remember this browser" or "Stay logged in" and can be turned on by checking a box when logging in. The session token then remains valid until the user clicks the "log out" button" - or it only becomes invalid after a longer period of time, for example after 30 days.
Four things are crucial to prevent hostile takeover of an account:
- Not being permanently logged in
If you log out completely after using the access, you do not risk the theft of a valid session token. Even if someone were to steal one, it immediately loses its validity when you log out. But be careful: criminals can also lock out the actual owner of the account. If, as in this case, the perpetrators have changed the password and the stored e-mail address, the account is lost for good. - Use multi-factor authentication
If you use this type of protection, you automatically increase your own security level and protect your account even if, for example, a password is stolen from the browser memory. - Permanent skepticism about direct messages and unsolicited links
No surprise really: no one should click on unsolicited links. This applies to companies just as much as to private users. - Use a password manager instead of the browser's "remember password" feature.
Information for fellow researchers
1ec988853602184ff683af474cc32d3ef9179abcf2b19224a02b062f9b806d16 (Win64.Trojan-Stealer.Agent.BPF)
1c9013f729c66ce1e9a604dd400e754095502253eabb1965025396b7357718ea (MSIL.Trojan-Stealer.Agent.BPE)
9ac0cb55dddb28d82632d2aee0834daf6300b5a15aee437fdb5868845e3bdfeb (BAT.Trojan-Downloader.Agent.BPJ)
8e5f47908ebb772e9a6f225c1b0b1ada656d029b4084f8dda6bb42f90fa730e6 (Python.Trojan-Stealer.PSW.A)
784b7d8e5abc2da2db1c920aba56cacf9ee7ab0e59dea09d942cd05cb09a1af4 (PowerShell.Trojan.Agent.BPK)
92547dcf0d0a298efb2c218a53093c9adba225d00455bd348942a9ec2d9572db (BAT.Trojan.Starter.G)
I would like to credit an old friend of mine who relayed this case to me in great detail - not all information could be shown here for privacy reasons. They preferred to remain unnamed here.
A tip of the hat also goes to Banu Ramakrishnan and Anna Lvova, who analyzed the malware.