Analysis by Lovely Antonio, Louis Sorita, Jr. and Ricardo Pineda, Jr.
SocGholish, also known as FakeUpdates, has been active since 2017. It is a downloader written in JavaScript that communicates via HTTP. It employs drive-by downloads, typically involving websites with injected JavaScript code. This method delivers a payload that masquerades as a fake browser update, allowing malicious software to be installed on a user's computer without their knowledge. It has been utilized by known threat actors such as the Russian operated Evil Corp (Manatee Tempest) and Initial Access Broker TA569 (Mustard Tempest).
As every attacker does, threat actors utilizing SocGholish always evolve their infection methods to evade detections, adapt to new security measures and increase the chance of successful attack. This blog will show the recent changes in the tactics, techniques, and procedures of threat actors utilizing this malware.
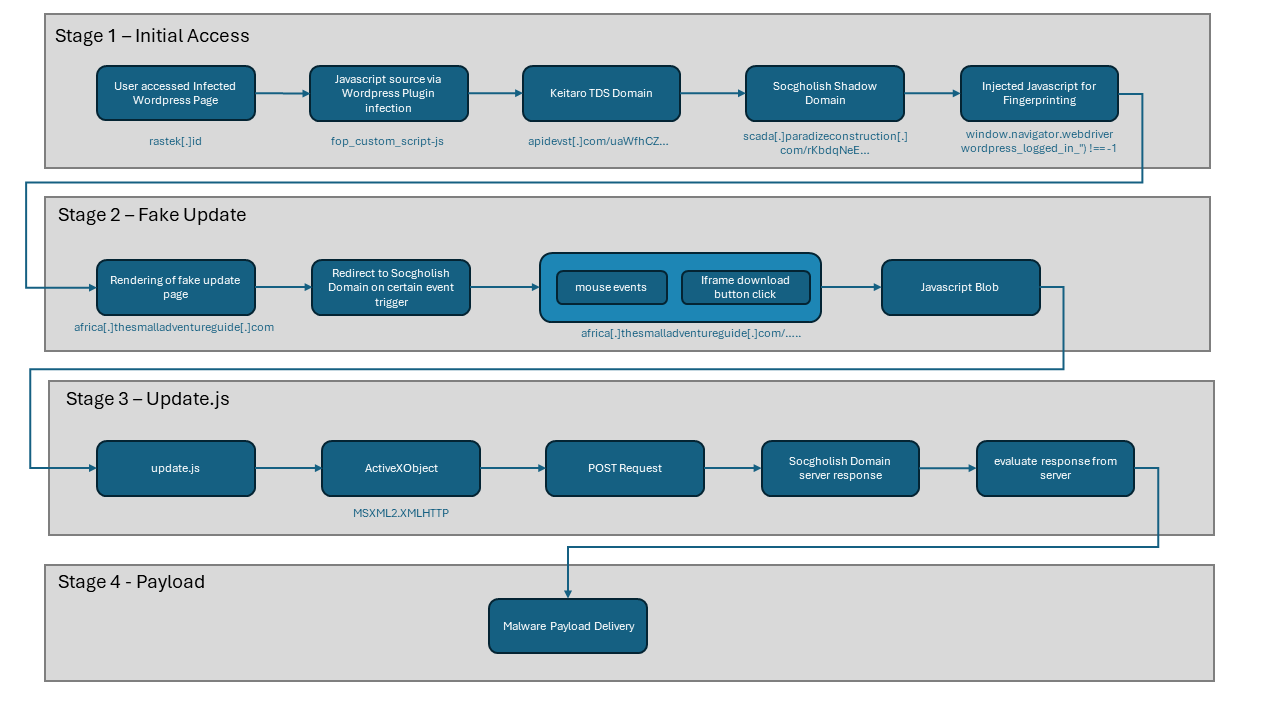
Stage 1: Initial Access
SocGholish uses drive-by downloads that normally consists of websites with injected JavaScript code. We have observed three different compromised sites that were exploited with vulnerable WordPress plugins and utilize the method of injection via the Keitaro traffic distribution system (TDS). Keitaro’s TDS is a self-hosted tool that can be used to manage and track advertising campaigns[1], but recently it has been abused by cybercriminals to redirect users to exploit kits.
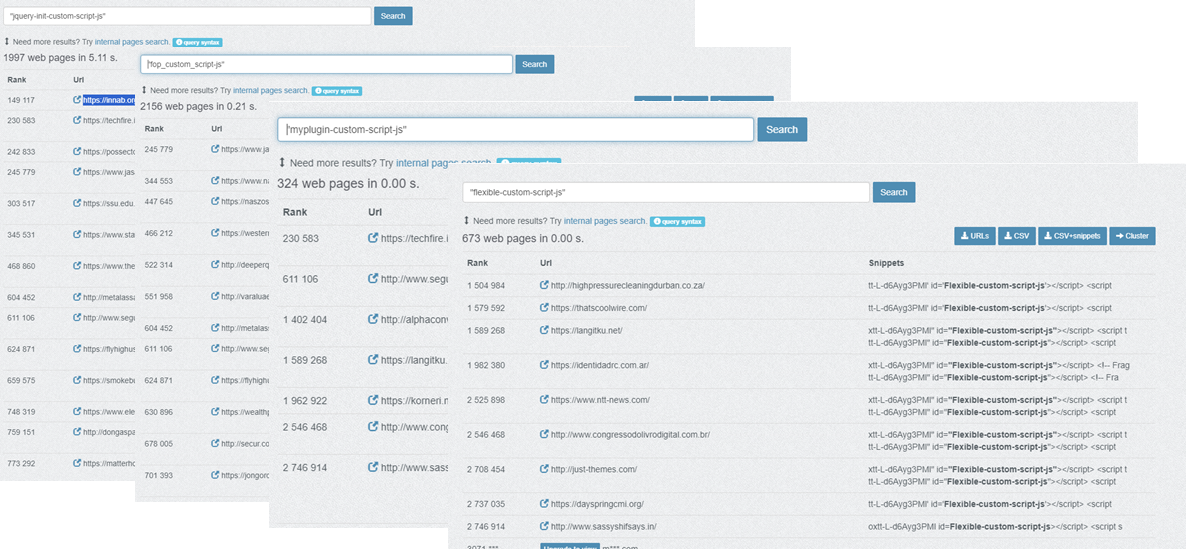
We were able to identify infected WordPress plugins from three websites --- see Infected WordPress Domains in IOC section --- then cross-checked the websites to PublicWWW --- a search engine for finding specific code snippets within website source codes, and found out that there are thousands of other webpages that are compromised.
| WordPress Plugin keyword | # of infected Sites (based on publicwww records) | WordPress Plugin (outdated, 3rd party plugins) |
| id="jquery-init-custom-script-js" | 1,997 webpages | Flexible SSL for CloudFlare |
| id="fop_custom_script-js" | 2,156 webpages | undetermined |
| id=" myplugin-custom-script-js" | 324 webpages | Performance Lab |
| id="flexible-custom-script-js" | 673 webpages | Flexible SSL for CloudFlare |
Figure 2. Infected WordPress Plugins and Infected WordPress Sites
Looking under the hood, we can see in Figure 4 that there is unusual script tag that we can see --- dns-prefetch href='apieventmitter(.)com', dns-prefetch href='apidevwa(.)com' and dns-prefetch href='apidevst(.)com' DNS-Prefetch is a tool for web performance optimization, allowing browsers to resolve domain names early, thus speeding up the retrieval of external resources.
We then proceeded to gather data about the domains linked in dns-prefetch, by using URLScan.io ---- a service that analyzes and reports on website content and structure, so we will have details for the gathered Keitaro TDS. All the TDS are pointing to one IP address: 158[.]160[.]11[.]208, which is identified to be hosted in Moscow, Russia. This IP address had links or may have been used from other campaigns by Evil Corp.
Following where Keitaro TDS will lead us, we landed on the following page that has a commonality in structure as well as the visible URL. All that remains for us to do is to still follow the redirection and go to the URL scada[.]paradizeconstruction[.]com, and this is the SocGholish Domain.
Unfortunately, the site was not accessible at the time of the analysis. Good thing that there are tools that can help us further the analysis. We used another tool which is The Wayback Machine's Internet archive that has a feature that allows users to search for and view archived versions of web pages from different points in time. Fortunately, it has archived the specific SocGholish page.
This retrieved source code from the archived page indicates fingerprinting of certain user profiles; the webdriver of the navigator interface indicates whether the user agent is controlled by automation, certain dimensions of height and width and on certain mouse event such as mouse move.
Stage 2: Fake Update
The injected script in the compromised sites leads to FakeUpdates page. SocGholish is known for using the FakeUpdates theme as a façade to install another malicious payload.
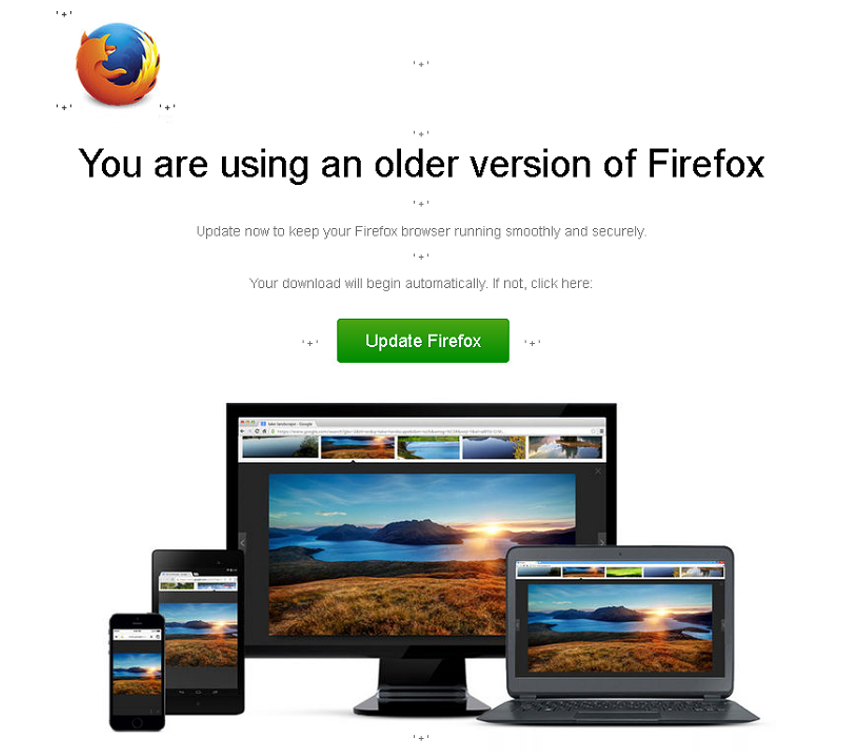
The fake update sites are constructed around luring users into clicking on the message because they are lead to believe that their browsers are outdated. The browsers being affected are the common browsers used (Chrome, Firefox, IE and Opera). As we can see in Figure 10, it used a fake Firefox Update.
Taking a look under the surface of the page, we can see in Figure 11 that it now monitors certain action of the user and will perform action based on the triggered mouse actions (movement, click and hover).
Once triggered via button click on the "Update Firefox" button, the hidden link will lead user to another SocGholish landing page africa[.]thesmalladventureguide[.]com/7nwh~.
A piece of obfuscated JavaScript code is downloaded which utilizes ActiveXObject("MSXML2.XMLHTTP") to create an XMLHttpRequest object, allowing the script to send a POST request to SocGholish Domain Server.Upon receiving a response, it will then proceed to using eval to execute the response. This approach poses a significant security risk because it can execute arbitrary code, and other things such as downloading another payload when an attacker controls the server or network.

Stage 4: Payload
We stopped our analysis at this point since the domain server it connects to is already down. Recent research by our colleagues suggests that the backdoor named BadSpace[1] might have been delivered using the same method as SocGholish, due to many similarities in their delivery techniques.
We also researched some of the other known payloads for malware families that have been linked to using SocGholish for the initial infection.
- Cobalt Strike [2]: A popular penetration testing tool that has been known to be abused by attackers for malicious purposes like remote access and lateral movement within a network.[1]
- Zloader [3]: Primarily designed to steal credentials and sensitive data, but also has backdoor capabilities and can act as a loader for other malware.
- Information Stealers [4]: Malware like RedLine Stealer and Lumma Stealer can be deployed through SocGholish to steal financial information, login credentials, and other sensitive data.
- Remote Access Trojans (RATs) [4]: These allow attackers to take control of infected devices. NetSupport RAT is a common payload seen with SocGholish.
- Ransomware [2]: Various ransomware families, including destructive ones like Ryuk and Egregor.
As of this writing, we have observed new SocGholish Infections from our telemetry, that it uses PowerShell, based in the part of the infection chain that persists the malware on the user’s system.
Prevention and Mitigation
To prevent and mitigate SocGholish infecting your system, a combination of technical and personal security measures must be observed. Here are some practices to follow:
- Regular Updates - Ensure that all WordPress files, themes, and plugins are regularly updated to patch known vulnerabilities.
- Plugins Usage - Use only trusted and secured plugins when creating/developing a website
- Security Plugins - Use Wordfence to protect against the likes of SocGholish Malware
- Security Awareness - Educate users about the dangers of fake update prompts and phishing emails
- Regular Backups - Maintain regular backups of important website data
MITRE ATT&CK Tactics, Techniques and Procedure
- Resource Development
- Compromise Infrastructure (T1584)
- Domains
- Compromise Infrastructure (T1584)
- Initial Access
- Drive-by Compromise (T1189)
- Execution
- Command and Scripting Interpreter (T1059)
- JavaScript
- Command and Scripting Interpreter (T1059)
- Defense Evasion
- Obfuscated Files or Information (T1027)
- Encrypted/Encoded File
- Obfuscated Files or Information (T1027)
- Discovery
- Domain Trust Discovery (T1482)
- Software Discovery (T1518)
- System Network Configuration Discovery (T1016)
- Command and Control
- Ingress Tool Transfer (T1105)
Indicators of Compromise
- Infected WordPress Domains
- tropicalforestproducts[.]com
- supremeceilings[.]co[.]za
- rastek[.]id
- Keitaro TDS
- apidevst[.]com
- ET CURRENT_EVENTS TA569 Keitaro TDS Domain in DNS Lookup (apidevst .com)
- apidevwa[.]com
- ET CURRENT_EVENTS TA569 Keitaro TDS Domain in DNS Lookup (apidevwa .com)
- apieventemitter[.]com
- ET CURRENT_EVENTS TA569 Keitaro TDS Domain in DNS Lookup (apieventemitter .com)
- gitbrancher[.]com
- ET CURRENT_EVENTS TA569 Keitaro TDS Domain in DNS Lookup (gitbrancher .com)
- asyncawaitapi[.]com
- ET CURRENT_EVENTS TA569 Middleware Domain in DNS Lookup (asyncawaitapi .com)
- apidevst[.]com
- Socgholish Domain
- scada[.]paradizeconstruction[.]com
- africa[.]thesmalladventureguide[.]com
- sticky[.]oystergardening[.]name
- JScript
- 78ddcf7ce945cfa92e640c53462174b21601506b39dec9731212d7d4ef8aa74d - Update.js
- Fake update page
- f0fbc29c86cd84ac18aeeee38de05c32fee95d6fa49425021ce0e3d3b13d2d05