How banking Trojans work
One of the key ingredients of Banking Trojans are called web injects. In short, a web inject adds HTML code into the network traffic of a browser.
Web injects usually consist of multiple stages. In this particular case, Stage 1 is a pretty generic inject responsible for downloading further target specific code. This second stage then manipulates the contents of a website to display all manner of fabricated data. This fabricated data may consist of messages about ‘accidental’ transactions the user is expected to ‘refund’, which blend in very well with the look&feel of the targeted banking site, as well as manipulations of their behavior. Stage 1 usually consists of obfuscated JavaScript. The current example is no exception to this. When run, it queries a number of parameters such as the browser version to leverage support for all major browsers. At that point, an infected PC is assigned a botID and an inject URL. The former identifies each affected client in the administration panel which is controlled by the attacker. The latter points the malware to specific URLs where the actual payload is downloaded. This payload is target specific, i.e. it is designed to work in connection with a specific banking website.
Striking features
The first thing that stands out is the size of the stage 2 sample, which at 91.8 kb is quite large for a script of this type. While file size alone is not usually a reliable indicator for the number of features, it became evident that the range of features in ZeuS Panda is pretty extensive.Some of the features include generic data stealing mechanisms (form grabber), which work on any website, other functions are target-specific.
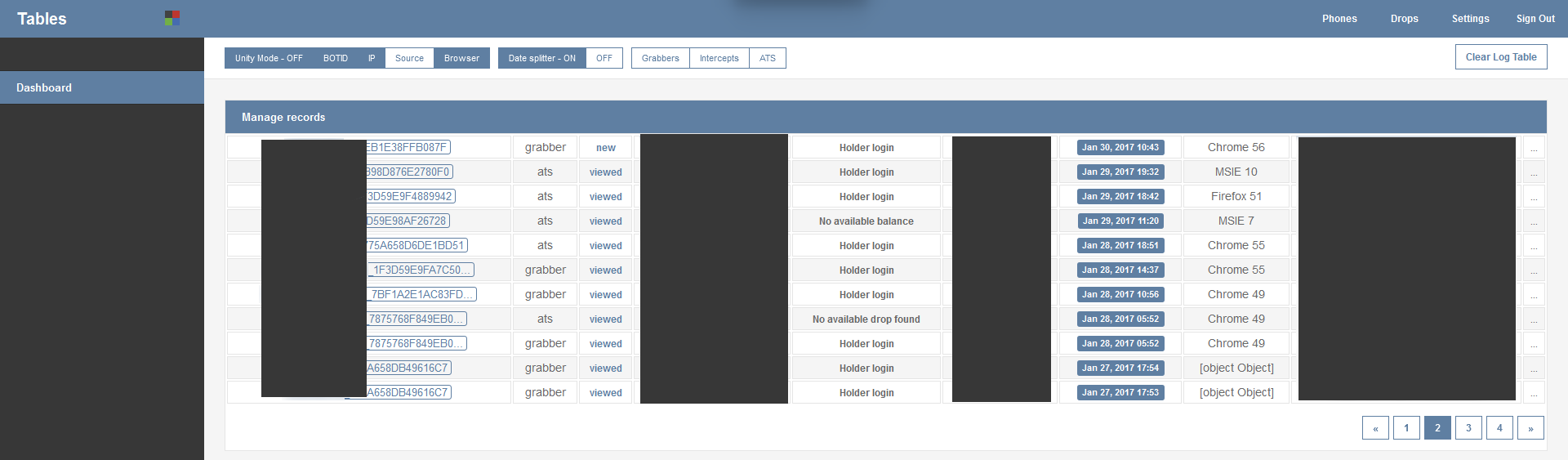
For a length of time, our researchers also have had access to the control panel of ZeuS Panda. We were able to locate the URL of one of the control panels (see screen shot) which are usually only accessible for the attackers. The stolen data consists of the botID, stolen login data, browser version and a couple of other data points.
More information
The analysis is ongoing and we will post further results as they become available. For technical details, please head over to the blog of G DATA Advanced Analytics.
All G DATA customers are protected from the ZeuS Panda malware by a combination of G DATA’s BankGuard and other protective technologies.