The first wave was observed between 17 December 2013 and 20 December 2013. The second wave began on 6 January 2014 and is still active, interrupted only by the recent weekend – it seems as if the attackers are conducting their business like normal workers.
From the start of this week alone (13 January), G Data has recorded more than 1,100 new websites allocated to the four campaigns. There are currently six different URL schemes that are used – two with respect to the Telekom, two matching Volksbank and one each for the remaining two companies.
The G Data SecurityLabs statistics show a concentration on the Telekom campaign in the last few days – a bit more than 49% of the mentioned infected URLs belonged to this. Malicious websites in Volksbank bait-mail represented slightly more than 28% and rank three is taken by NTTCable with almost 12%.
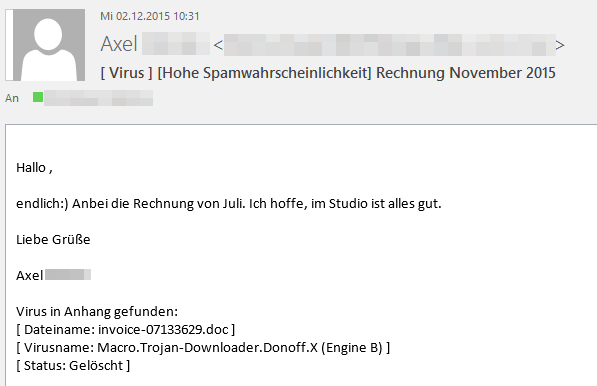
All four companies are well-known, and many email recipients initially regard the emails as trustworthy. However, a link to a malicious website is embedded in the well-designed fake invoices and notification emails:>

Alphabetically-arranged examples of email subjects, including typos and spelling mistakes made by the attackers include:
- Information on: transaction/transfer #[18 digits]
[German: Information zu: Überweisung/Umbuchung #[18 Ziffern]] - More information on Volksbank transaction: [12 digits]
[German: Weitere Informationen zum Transaktions Volksbank: [12 Ziffern]] - NTTCable telephone invoice
[German: Telefonrechnung NTTCable] - NTTCable telephone invoice for January
[German: Telefonrechnung NTTCable Januar] - NTTCable telephone invoice for January 2014
[German: Telefonrechnung NTTCable Januar 2014] - System update
[German: System-Aktualisierung] - Update your software
[German: Aktualisierung Ihrer Software] - Your account may not be compromised
[German: Die Zuverlassigkeit Ihres Kontos ist nicht im Gefahr] - Your online banking access details will soon expire
[German: Ihr Online-Banking-Zugang bald ablauft] - Your invoice dated 14 January 2014 is ready as a PDF: [18 digits].
[German: Ihre Rechnung vom 14.01.2014 steht als PDF bereit: [18 Ziffern].] - Your invoice dated 15 January 2014 is ready as a PDF: no. [18 digits].
[Ihre Rechnung vom 15.01.2014 steht als PDF bereit: Nr[18 Ziffern].] - Your Telekom online mobile phone invoice for business customer [18 digits] on [date] for customer account [12 digits].
[German: Ihre Telekom Mobilfunk RechnungOnline für Geschäftskunden [18 Ziffern] vom [Datum] des Kundenkontos [12 Ziffern].]
If the user clicks on the link, a .zip file is first automatically loaded onto his computer. The attackers have deposited malware from the Cridex family in this archive as an executable file. As soon as the user opens the .exe file, the banking Trojan infects the PC.
Malware in this family is known for functions such as:
- Man-in-the-browser functionality, in which all data traffic relating to online banking websites is manipulated. Attackers use this to fraudulently make money from transactions.
- Embedding itself in the system (registry entries and copies of the malware file).
- Recording keyboard entries (keyloggers), mainly on online banking websites.
- Sending information it has acquired over the Internet to servers.
- Downloading additional malware files and installing them on the infected computer.
According to the latest information, the malicious files are stored on servers in Romania, Russia, Britain and the USA. The attackers keep storing new variants of the malware, to prevent extensive detection by AV products as far as possible.
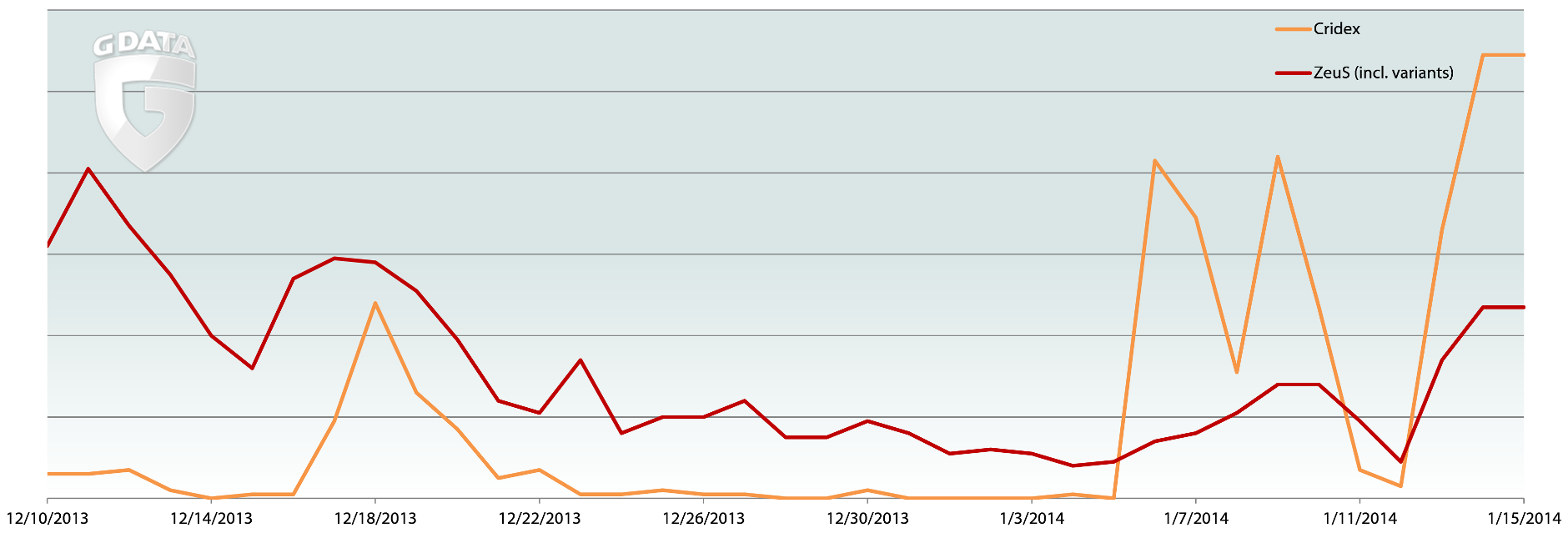
However, the various G Data protection technologies hold the malware in check – foremost among these is of course the G Data BankGuard technology, which can be found in the current end user products, for example. BankGuard detections of Cridex have reached a new high in recent weeks. The Trojan was first detected in 2011, but has only been exhibiting significant levels of activity since April 2013 (see G Data Malware Report H1 2013). However, in the recent past it has been causing more of a furore even than the established banking Trojan ZeuS and all its clones, such as Citadel and Gameover:
In this latest example, it is clear that sending spam as an initial attack vector is still far from unfashionable. The attackers have gone to great pains to generate different versions of the fraudulent emails and make them look deceptively realistic. Only a few errors betray the fact that these are fakes.
With a sophisticated payload such as Cridex, cyber attackers are able to plunder on various levels – for example intercepting transactions, stealing personal data and selling it on, installing new malware, sending spam and more.
Tips on handling emails:
- An up-to-date comprehensive security solution with a malware scanner, firewall, web and real-time protection is an absolute must. A spam filter that protects you from unwanted spam emails also makes sense.
- Email from unknown senders should be treated with caution. If an email looks very strange, here's what to do: ignore it, delete it, but under no circumstances open attachments or click on URLs.
- Opening file attachments, especially from unknown senders, harbours risks. Attachments should first be scanned with an antivirus program and, if necessary, deleted without being opened.
- Links in emails should never be clicked on without thinking. Check the URL. Many email programs permit the actual target of the link to be seen by hovering the mouse over the visible link without actually clicking on it – the so-called mouse-over function.
- Spam email should never be responded to either. All a response does is indicate to the fraudsters that the address they wrote to is actually valid.
- Never disclose any personal information and/or bank data – either via email or on dubious websites.
- Never transfer money to an unknown person.
- Never thoughtlessly publish your own primary email address online, e.g. in forums and guest books, as it can be accessed by fraudsters there. It is useful to enter a secondary address for these purposes.