Code signing basics
Digitally signing a software - also referred to as “code signing” - is intended to certify a software’s authenticity. It is a method that provides a sense of assurance to the users that the software they are using is untampered with and true to its original design. Each digital signature is vouched for by an entity called “signers”. Like our personal handwritten signature, each digital signature is unique for each signer. It is also the signer’s duty to keep the signature secure so that no one else can use it without their consent.
Other than software applications, digitally signing is also applicable to various file types such as MS Office documents (.doc/x, .ppt/x, .xls/x), images ( .bmp, .gif, .jpg, .png ), and other digital documents like PDF and e-mails.
By design, modifying a digitally signed file will cause the signature to become invalid. Even a slightest change should invalidate its digital signature. Windows has also placed features such as Microsoft Defender SmartScreen and User Access Control (UAC) to warn users when running an application from an unknown publisher.
Tampered, but not broken
In January 2019, Virustotal[1], together with Microsoft, disclosed a vulnerability involving digitally signed Microsoft Installer files(.MSI). Researchers had found out that the validity of a digitally signed MSI file will remain intact even after appending additional content to the end of the file. This poses a risk because it defeats the purpose of digitally signing applications. With its signature remaining valid even after tampering, this can be exploited by threat actors. By using a signed MSI file as a vector,malicious code can be planted on a system with little effort.
With “.msi” as its extension, the patched MSI file will still function as intended, ignoring the appended code. But a fitting dangerous use-case may happen if a Java Archive (JAR) file is appended on the digitally signed MSI file and was renamed as “.jar”. By default, files with the extension of “.jar” will be directly executed by Java thus allowing the appended code to run despite it being natively an MSI file. This is because Java is designed to execute from “bottom to top”, which enables the Java-based code appended at the bottom of the MSI file to be executed.
Old frenemies
During the first quarter of 2020, we have seen several activities exploiting this known flaw for malicious activity. Targeting Windows users, the technique was seen to be used and abused on signed installers of Microsoft Silverlight to carry various types of JAVA-based malware. Silverlight is a framework for writing and running mobile and web-based applications, like Adobe Flash. It was developed by Microsoft and has been deprecated since its last release on January 15, 2019. Though it was tagged as deprecated, it is still available on their official page and is still used by some web services that uses it for streaming multimedia contents. It was used by Amazon and Netflix prior to moving to HTML5. Silverlight is packaged in a digitally signed MSI file, which makes it a suitable candidate for this kind of trickery.
This has been the case for multiple modified Silverlight installer we have seen in the wild. Hosted in various compromised websites, we have seen patched MSI files being distributed with “.jar” as extension. These patched installers were not distributed and labelled as an actual Silverlight installer, but rather as a phishing component.
Each carry a variant of JAVA-based malware that are mostly encrypted with JAVA obfuscators like Allatori[2]. Based on our telemetry, most of the threat using this exploit are RATs (Remote Access Trojans). RATs are notorious malware that can grant threat actors access to the victim’s computer which may result to data theft and a gateway for other threats to enter an infected system.
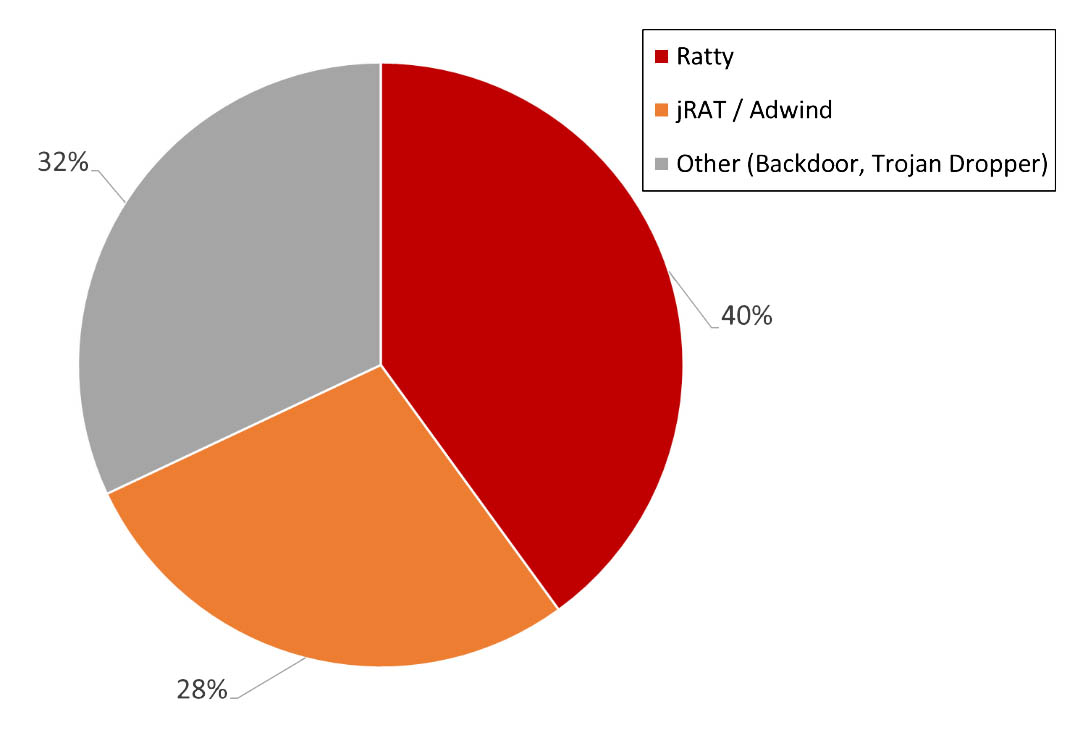
RATs everywhere
Covering 40% of the tampered MSI with malicious java that we have found, Ratty is an open-source Java-based RAT that was widely available via GitHub before the author removed it in 2016.
jRAT also jumped on the bandwagon, using this technique as a vehicle for its campaign. Also known as Jacksbot, jRAT is a known Java-based RAT that can be ported to run in multiple platforms such as Windows, Mac, and Linux. It can increase its odds for successful evasion through encryption and is capable of surveillance through webcam monitoring and keylogging.
These malware campaigns are not new, some have been around since 2013. And the addition of this exploit could increase its chance of evasion. We have also observed that there is consistency in the language used for the filename of the malicious sample to the TLD (Top Level Domain) of the compromised site. As an example, a french filename “Portail e-Impots FACTURE.zip”(Invoice e-Tax Portal.zip) was used on the compromised French(“.fr”) website. A keen attention to such detail makes the social engineering component of this malicious campaign more effective.
Samples of Signed MSI file with Malicious Java seen on Q1 2020
| URL/File | Appended Java Malware | Phishing |
|---|---|---|
| http[:]//prohost[.]sa/InformedUSPS[.]jar | jRAT / Adwind | As a USPS related invoice |
| https[://18655[.]aqq[.]ru/Dr0pb0x/files/overdue_Invoices_statement_pdf[.]jar | Java VBS Dropper | As a financial obligation invoice hosted on a fake Dropbox |
| http[:]//americanrange[.]com/HomeFedEx[.]jar | QRat | As a FedEx invoice |
| https[:]//margopassadorestylist[.]com/AT&T/AT&T%20payment%20confirmation.pdf.jar | jRAT / Adwind | As an AT&T related payment invoice |
| http[:]//coolshape[.]net/new~order[.]jar | Ratty | As a shipping order invoice |
| https[:]//hotlancer[.]com/ScannedEpsondoc03-18-20[.]jar | jRAT / Adwind | As a scanned business document |
| http[:]//getupandthriveitforward[.]com/Tracking-label[.]jar | Ratty | As a logistics document |
| https[:]//info-update[.]fr/Portail e-Impots FACTURE[.]zip | jRAT / Adwind | As an archive containing tax-related invoice |
Conclusion
The vulnerability is still currently unpatched which poses a risk to all of us. With Java-based malware currently exploiting this flaw, it is only a matter of time before other campaign make an attempt to capitalize on this technique by using a legitimately signed MSI file as their “free pass” in entering our systems.
This shows us that we cannot fully rely on a single prevention technique and expect it as a fool-proof system in preventing infection. We must be extra careful in opening e-mail from unknown or untrusted senders, especially when it asks us to open an attachment, click a link, or divulge personal information. Also, always choose to source your software and application needs directly from legitimate and official channels.
Threat actors will try any means possible to infiltrate our system and extract valuable information from our organizations. That is why it is essential to have a security solution that protects from different vantage points. Protection from e-mail, to downloaded file, and even on running software through behavioral monitoring and detection.
G DATA Detections
| File | SHA256 | Detection |
|---|---|---|
| InformedUSPS.jar | 53376470B9AC56FA09975E3A46D87A9C451E32EEC2925C8656138BFE18B92ADE | Java.Trojan.GenericGB.28665 |
| overdue_Invoices_statement_pdf.jar | DFF5D7BD253814F21C3356F6E2FB458CFDFF6908A11A73B36A1B248F1F28CC34 | Java.Trojan.GenericGB.28533 |
| HomeFedEx.jar | B50E6CAF79F86896D693E2088D3C53E3E3AE5D52E2F0B919E9B168AD1E52AC43 | Script.Trojan.QRat.H |
| AT&T payment confirmation.pdf.jar | 1EE285449A1255F9B4EE58835621700C9680B69D4A8E846F6C6F0C59CBA4DF15 | Java.Backdoor.JRat.B |
| new~order.jar | FFBB522721EB4C518FE199D0CD60DA52875933A5171B3D0FF0E1F855834B02F9 | Java.Trojan.Ratty.B |
| ScannedEpsondoc03-18-20.jar | F2A973A39B830D327C915E9A194DE5CD62C1571556959787637F4050BF169C9F | Exploit.AppendedJar.2.Gen |
| Tracking-label.jar | F41313345680EDBD1BF0666E8233BA0436A13ECF6C3AB98606580099748B415B | Java.Trojan.Ratty.B |
| COMMUNIQUE1.pdf.jar | CC2B3CA612209339161CBB3018AE823919BE0F15D633771C94ACD66E0BD96091 | Java.Trojan.Agent.ASE |
| Packing List.jar | 5EA6C0E741C01253428BC81C993EBD3A38DD0054BD1D2928047469F128E2709B | Exploit.AppendedJar.2.Gen |
| InformedUSPS.jar | 53376470B9AC56FA09975E3A46D87A9C451E32EEC2925C8656138BFE18B92ADE | Java.Trojan.GenericGB.28665 |