An Analysis by Lovely Antonio, Louis Sorita, Jr. and Arvin Lauren Tan
Vidar Stealer, an infamous information-stealing malware, first appeared in 2018 and has since been used by cybercriminals to harvest sensitive data via browser cookies, stored credentials, financial information, and the like. Over time, its distribution methods have evolved (originating from the previous Arkei Trojan), adapting to different attack vectors such as malicious email attachments or malvertising campaigns. This information stealer functions as Malware-as-a-Service (MaaS) and can be directly purchased from the dark web.
One recent example is PirateFi, a free-to-play game released on Steam on February 6, 2025. Marketed as a beta version, it concealed Vidar Stealer within its files, infecting unsuspecting players upon installation. This incident highlights how threat actors are increasingly targeting gaming platforms to spread malware.
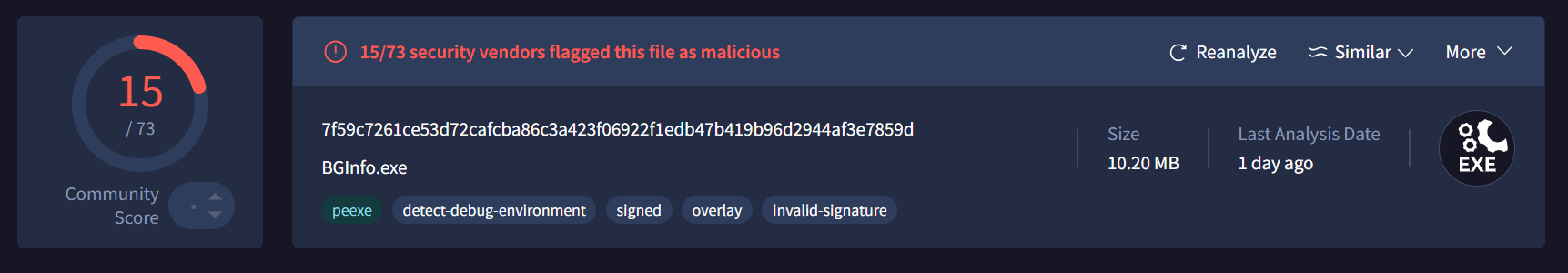
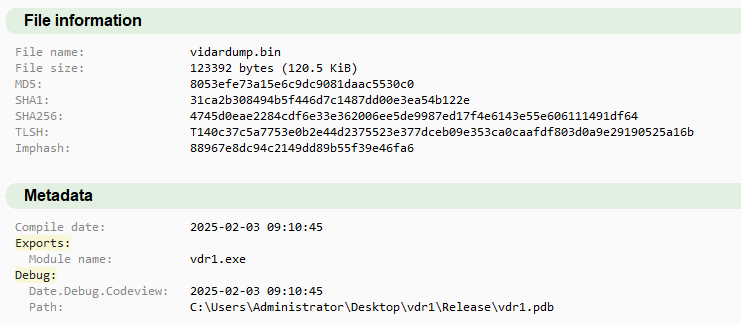
While hunting for Vidar Stealer variants, we encountered an unusual sample with only five detections on VirusTotal as of March 9, 2025. The low detection rate suggested possible obfuscation or a new variant. Interestingly, G Data flagged the file as VidarStealer, raising interest to further deep dive in investigation.
Upon reviewing the metadata in VirusTotal, a concerning detail stood out:
Filename: BGInfo.exe (a legitimate Microsoft Sysinternals tool)
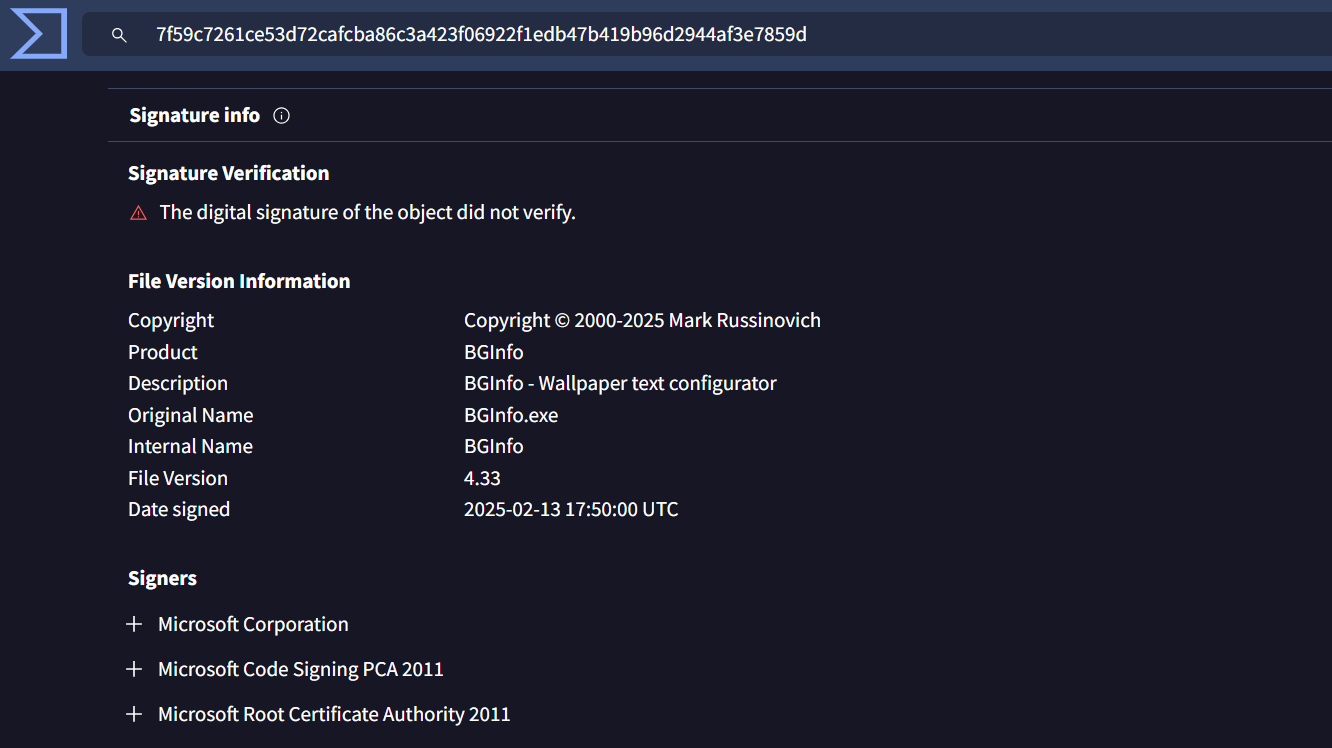
Signature: Microsoft Signature Expired
This was an immediate red flag. Sysinternals tools are widely trusted, so any irregularity such as an expired signature indicates that the file is no longer covered by a valid certificate, raising concerns about potential tampering or unauthorized modifications. Threat actors often take advantage of expired signatures to pass off malicious files as legitimate, knowing that some security mechanisms may still recognize them as signed executables.
What is BGInfo and Why is it in here?
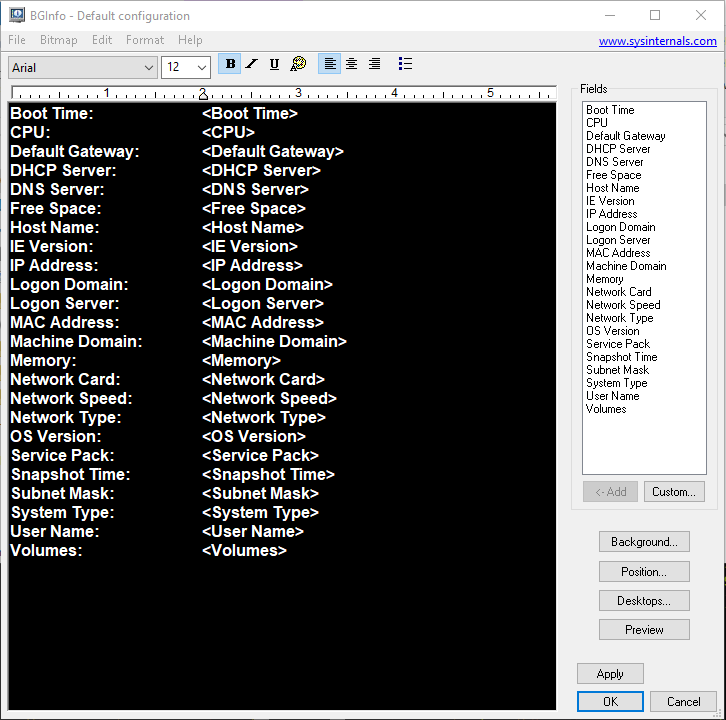
BGInfo is a system information tool developed by Microsoft, widely used by IT professionals and cybersecurity analysts to display key system details—such as IP addresses, domain names, and system uptime—, directly on the desktop background. This allows security teams to quickly assess system configurations without manually checking system properties, making it a valuable tool for managing and monitoring enterprise environments.
On February 25, a malware sample was observed in the wild, mimicking the legitimate binary’s creation time (February 13, 2025) to avoid suspicion. Attackers often exploit software updates to distribute malicious versions, knowing that users are more likely to trust and install an update when it is expected. By leveraging this timing, threat actors increase the chances of their malicious payload being downloaded and executed.
Spotting the Differences: Legitimate vs. Malicious BGInfo
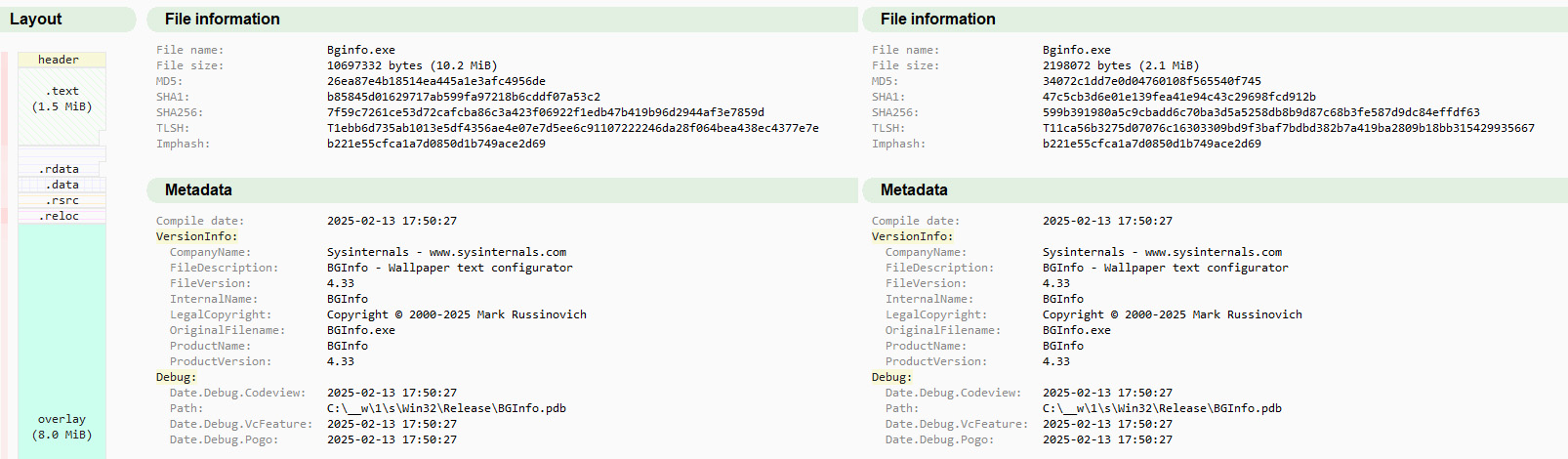
To determine whether a BGInfo update is compromised, a direct comparison with the official version is crucial. Since BGInfo.exe is part of Microsoft’s Sysinternals Suite, any significant deviation from the known characteristics of the original file could indicate a compromise.
Key red flags include:
- File Size: Official 2.1 MB vs. Malicious 10.2 MB (larger due to extra hidden code/binary padding)
- File Hashes: The official and suspicious versions have different cryptographic hashes
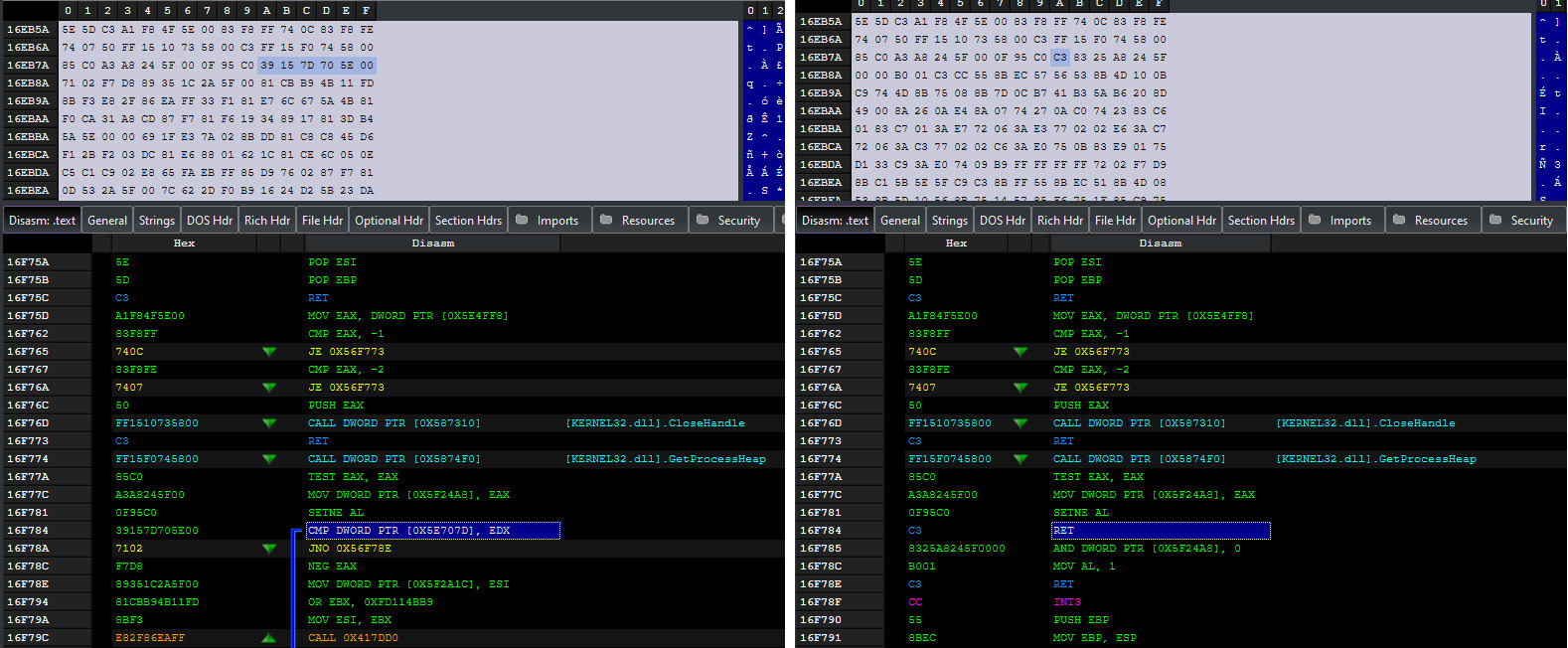
The malware author also modifies the initialization routine of BGInfo.exe particularly on handling the process heap for future memory allocations and point it to the malicious function, ensuring the file runs the malicious code instead of the expected BGInfo function. One clear sign of compromise is that the infected version does not update the desktop wallpaper which is a key feature of BGInfo indicating that there is something wrong.
Investigating Vidar Stealer
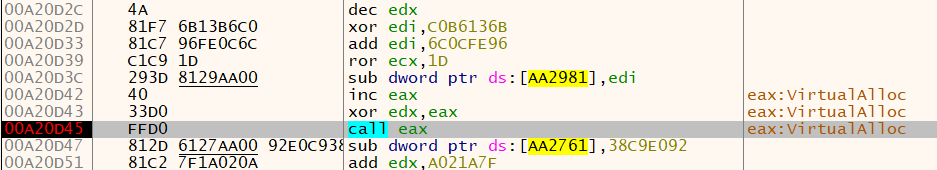
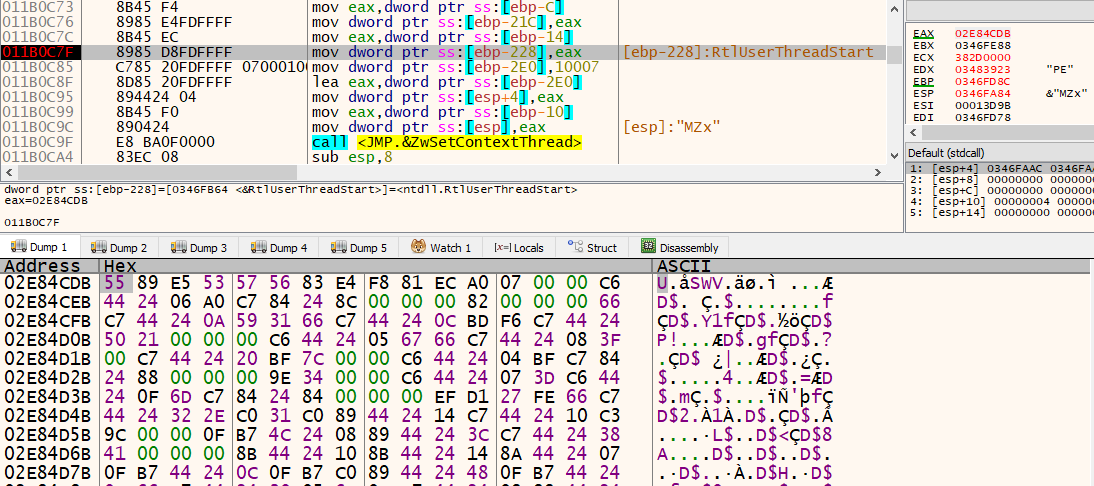
Tracing through the modified function, there will be an encounter to a call to VirtualAlloc that creates a virtual memory to allocate space for the next stage of the malware code as seen in the figure below. Upon loading the code on the allocated memory space, a jump to the memory address is expected which leads to the next stage of the malware.
Interestingly, Vidar Stealer is executed by modifyingthe pointer to the address of RtlUserThreadStart from the stack, a key function responsible for starting a thread in user mode. Instead of allowing normal execution, the malware redirects RtlUserThreadStart to the entry point of Vidar Stealer’s binary, effectively hijacking the execution flow.
Key Capabilities of Vidar Stealer
Our analysis of this variant has not identified any novel behaviors or deviations from previously observed versions. Its functionality, attack patterns, and execution flow remain consistent with earlier samples, indicating no significant modifications or new tactics employed by this iteration. Its main payload behaviors are as follows:
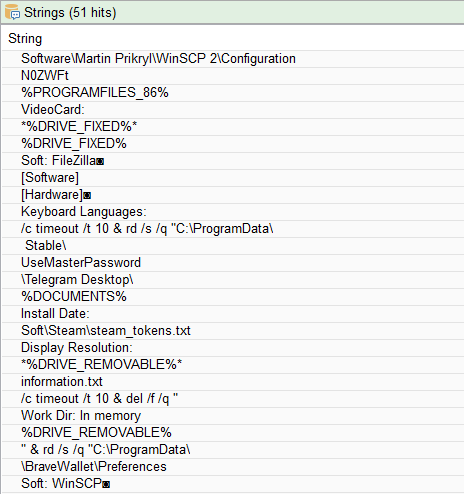
- Credential Theft – Checks for important directories from the user’s system. Extracts saved usernames and passwords from browsers and applications.
- Cryptocurrency Wallet Theft – Targets wallets such as Monero, BraveWallet, etc.
- Session Hijacking – Steals session tokens, allowing attackers to bypass authentication from known popular applications such as Steam, Telegram, Discord, etc.
- Cloud and Storage Data Theft – Extracts stored credentials from Azure, AWS, WinScp, FileZilla, and other services.
Conclusion
Vidar Stealer continues to evolve, using new distribution methods and evasion techniques to remain a persistent threat. The recent abuse of BGInfo.exe highlights how attackers disguise malware within trusted tools to bypass security measures.
This reinforces the need for continuous threat hunting, proactive monitoring, and in-depth analysis of seemingly benign binaries. Identifying subtle anomalies such as expired signatures, unexpected file size discrepancies, and unusual memory behavior, can be crucial in uncovering sophisticated malware campaigns.
MITRE TTP
Masquerading: Invalid Code Signature - T1036.001
Masquerading: Match Legitimate Name or Location - T1036.005
Obfuscated Files or Information: Binary Padding - T1027.001
Data from Local System - T1005
Unsecured Credentials: Credentials In Files - T1552.001
Credentials from Password Stores: Credentials from Web Browsers - T1555.003
Web Protocols - T1071.001
Exfiltration Over C2 Channel - T1041
Process Injection: Thread Execution Hijacking - T1055.003
IOCs
7f59c7261ce53d72cafcba86c3a423f06922f1edb47b419b96d2944af3e7859d – Win32.Trojan-Stealer.VidarStealer. FO2EFU