Following Arstechnica’s story about malicious Github repositories, we wrote a threat hunting tool to identify abused repositories. What caught our attention weren’t forks of existing repositories as described by Arstechnica, but newly created repos that lead to the same download link.
Github repositories
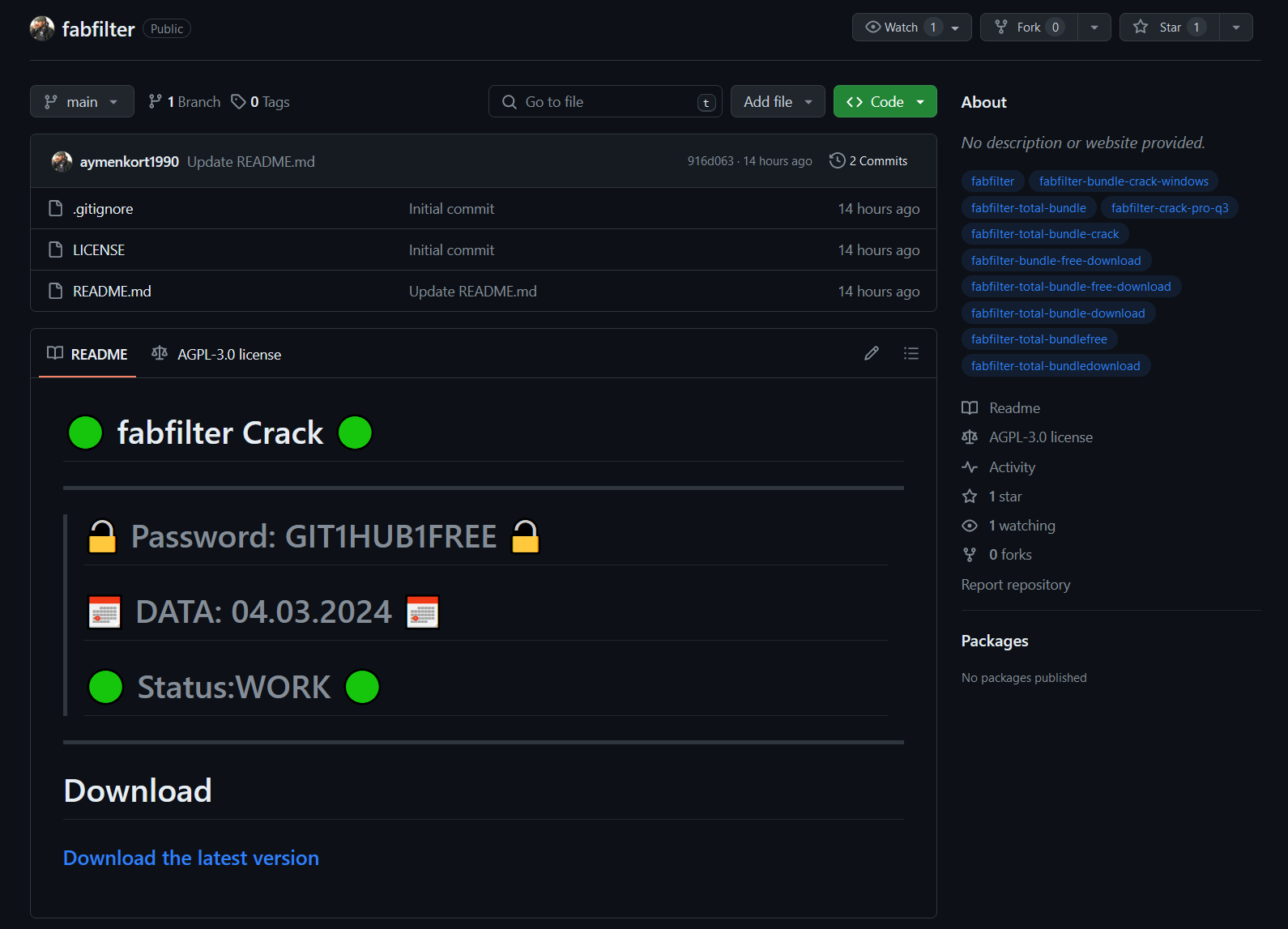
We identified at least 13 such repositories belonging to a RisePro stealer campaign that was named “gitgub” by the threat actors. The repositories look similar, featuring a README.md file with the promise of free cracked software. Green and red circles are commonly used on Github to display the status of automatic builds. Gitgub threat actors added four green Unicode circles to their README.md that pretend to display a status alongside a current date and provide a sense of legitimacy and recency.
The following repositories belong(ed) to the gitgub campaign:
andreastanaj/AVAST
andreastanaj/Sound-Booster
aymenkort1990/fabfilter
BenWebsite/-IObit-Smart-Defrag-Crack
Faharnaqvi/VueScan-Crack
javisolis123/Voicemod
lolusuary/AOMEI-Backupper
lolusuary/Daemon-Tools
lolusuary/EaseUS-Partition-Master
lolusuary/SOOTHE-2
mostofakamaljoy/ccleaner
rik0v/ManyCam
Roccinhu/Tenorshare-Reiboot
Roccinhu/Tenorshare-iCareFone
True-Oblivion/AOMEI-Partition-Assistant
vaibhavshiledar/droidkit
vaibhavshiledar/TOON-BOOM-HARMONY
The download link is the same for all repositories, namely:
hxxps://digitalxnetwork[.]com/INSTALLER%20PA$$WORD%20GIT1HUB1FREE.rar
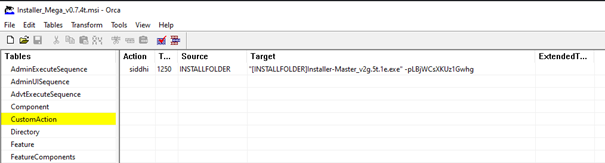
The unsuspecting user must unpack several layers of archives using the password "GIT1HUB1FREE" before they reach the first executable file named Installer_Mega_v0.7.4t.msi[2].
Orca.exe shows that this MSI unpacks the next stage by applying the password "LBjWCsXKUz1Gwhg". The resulting file is named Installer-Ultimate_v4.3e.9b.exe[3].
Installer-Ultimate_v4.3e.9b.exe
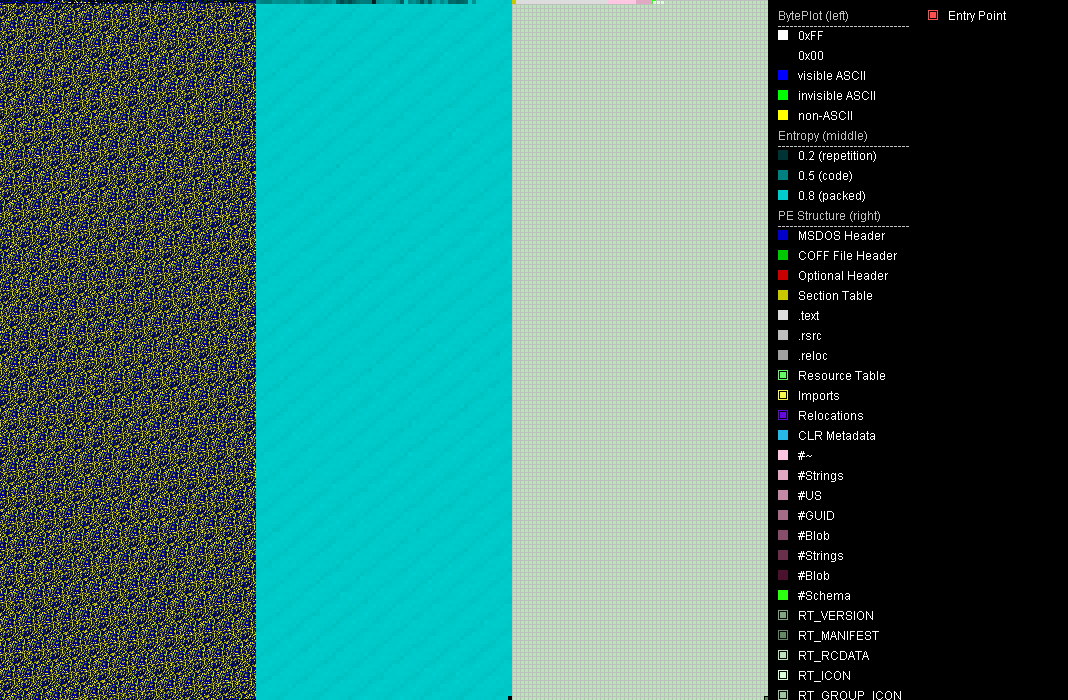
To complicate analysis, this file[3] is bloated to 699 MB, which causes IDA and ResourceHacker to crash. The visualization of the sample by PortexAnalyzer shows that the bloat is non-trivial. While many bloated files feature appended zero bytes, this file has high entropy and no overlay.
Knowing that the self-extracting archive from which we unpacked the sample compressed this file to 70 MB, we suspected a repeating pattern. Additionally, the visualization of PortexAnalyzer (see image above) shows a ripple in the high entropy area, which suggests the same.
After inspecting the area, we identified a repeating block of 0x1C0 bytes, followed by a unique byte block of size 0x2d. This repeating byte block allows the file to be compressed when archived while keeping the entropy of the unpacked, bloated file high.
17 53 18 2F 9F FC 12 BD 1A E9 7B 4A EB 53 CC 6A D3 05 E6 B3 9A FE 7C AF 05 52 05 73 2E 1D EB 14
56 12 84 56 BD DA E8 46 6A 7C 60 8C B3 8F 70 DE E8 70 F1 C2 71 C3 53 6E C8 F0 EB B0 12 32 86 00
88 5F D7 B2 66 F4 F4 80 22 28 45 12 62 08 D3 CB BE 49 CE CD 60 12 BA 6F 17 A0 0F B4 C2 2C D5 08
DF 3F F9 2E BA A0 C9 64 E3 AF 69 99 1D 5C E6 20 4D 1A 77 01 03 08 94 43 28 F3 F7 47 8D F7 55 FD
4E A7 65 99 D4 10 66 F9 8A D7 29 D2 76 24 F1 BA 60 3B BA 4F C5 8B 06 AB ED 3E C4 94 A7 FE 96 59
9B 6E 33 A1 EE 6D 47 66 F6 E2 F4 8C 41 89 1A 34 AD 0C 10 64 0C BA 27 AC 91 77 F4 08 B7 FF 5D AE
C5 D1 1A 8B 7B 12 93 64 B4 05 C0 2F 6F 49 F1 11 19 13 83 E1 0D D0 64 75 75 D6 5A E8 AA 42 C9 BE
A6 CD 16 27 2E 08 01 9E 3B 69 6F 27 D9 9B C1 62 A4 14 58 6F 45 00 44 5D 22 2A 29 1A DE 7E 1E 18
4A 95 AB 1F 26 97 07 97 2B 16 6E 54 E2 50 AB F2 24 99 6D 80 93 2C 9F DC 3A F5 08 37 BE C4 7B 4A
E1 BC 49 47 79 16 53 C5 9E 44 F1 7B AD 21 ED 7F 4E AF 17 2F 4C 6B 4C 5B 37 B2 74 80 0B 41 F8 F7
69 94 F0 E5 CE D8 01 DF B0 75 CB 39 84 50 7F E5 B5 87 3E E8 D6 DD F3 AB 3F B8 C9 0E 47 61 81 C8
1C 72 92 4F DE 19 00 96 AB FB 4C EA 51 47 9B 31 3F 42 1C 2A DF 90 DC CC 96 69 37 D5 BE B8 80 1C
F4 CA FC D0 8D 98 E2 81 16 D1 46 B7 C1 C4 36 AA C2 23 8E 08 9A 06 18 37 16 6E A2 D4 09 E9 DF D0
F2 8F 39 BA EC BB A2 77 20 C2 C6 16 2C 49 19 21 95 E5 1A 59 78 D8 61 64 9F 3E 11 76 CF 37 14 64
(the hexadecimal values of the repeating block)
The bloat data resides in an RC_DATA PE resource named MICROSOFTVISUALSTUDIODEBUGGERI, which has a size of 0x2b85418f bytes. By removing this resource with CFF Explorer we successfully slimmed the file from 699 MB down to 3.43 MB.
Detect-it-Easy identifies an InnoSetup signature in this file, however, this signature turns out to be fake. The file is a .NET assembly.
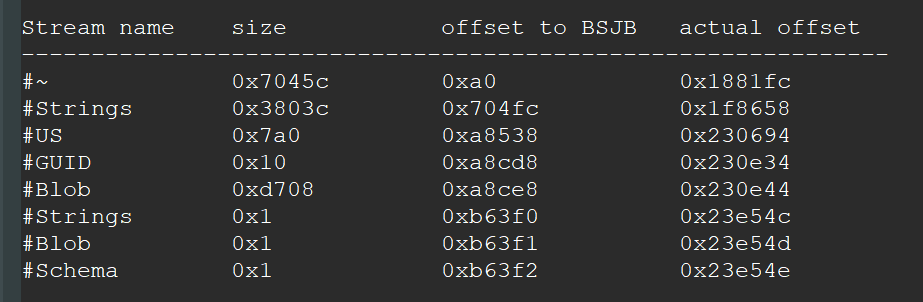
The .NET streams are unusual: Firstly, there are two #Blob and #Strings streams even though there can only be one according to the Common Language Infrastructure (CLI) specification (see II.24.2.2, page 272). Secondly, there is a #Schema stream, which is not part of the CLI (see II.24.2.2, page 272). The three faulty streams have an invalid size of one byte and point to the same offset. This is likely an attempt to break or confuse .NET parsers.
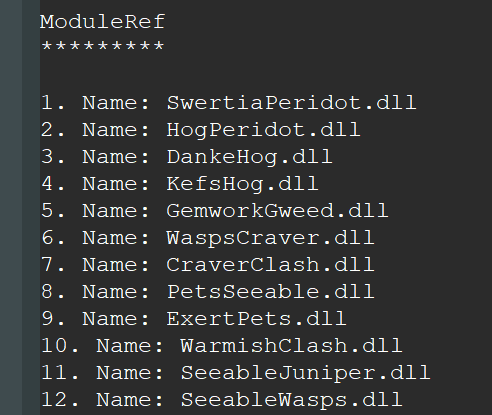
The ModuleRef table references 727 DLL files (see image on the right) which all seem to consist of two arbitrary dictionary words appended to each other, except for the last entry, which is kernel32.
The file is obfuscated with a version of .NET Reactor 6 and has virtualization enabled, which means deobfuscation of the loader’s code requires to write a disassembler for the virtualized instructions.
During execution, the loader connects to hxxp://176.113.115(dot)227:56385/31522 and injects its payload[4] into either AppLaunch.exe or RegAsm.exe.
Injected RisePro payload
We identified the payload[4] as RisePro stealer version 1.6. The version number stems from the stealer’s logs. We assume that this is the latest version of RisePro, as within the malware authors' publicly accessible Telegram channel, the most recent server updates are referred to as version 1.6.
The sample resolves its imports dynamically using import hashing with Fowler–Noll–Vo hash 1A.
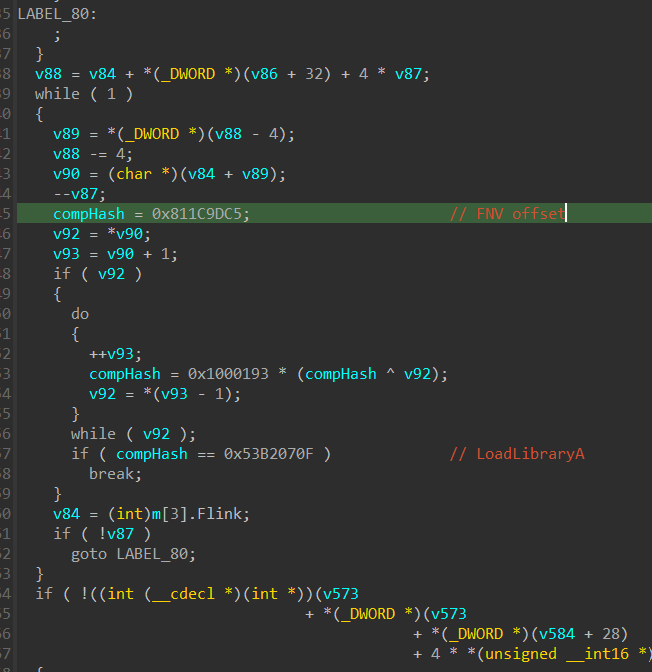
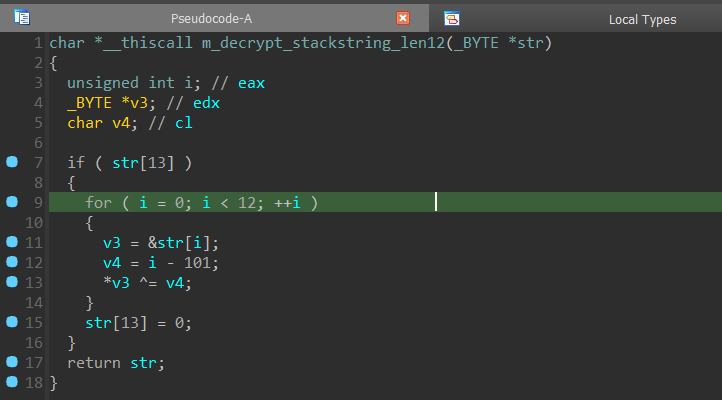
RisePro uses XOR obfuscated stack strings. A previous RisePro report by OALabs states that xorstr library has been used for RisePro's string obfuscation in the past, but it seems the encryption scheme has been changed in the meantime.
The library xorstr features "heavily vectorized compile time string encryption" and uses vpxor/pxor instructions to perform the XOR operations. A yara rule in the aforementioned OALabs report searches for pxor patterns in the binary. RisePro developers may have reacted to that public rule.
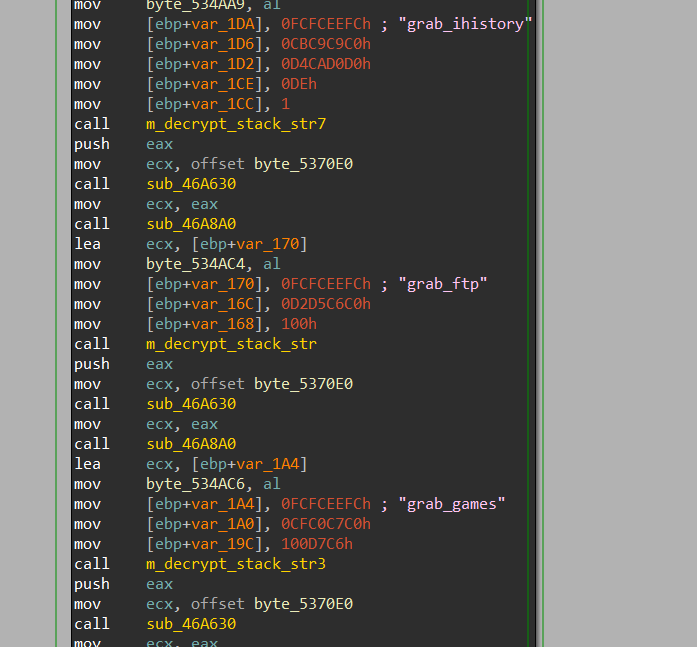
The new stack string decryption scheme uses one hardcoded decryption function for every string length that the stealer needs. All of these functions use the same underlying decryption algorithm but the length is hardcoded in the decryption loop.
We decrypted the strings with a Binary Refinery snippet, which prints the decrypted strings and their offsets in a format usable for Python dictionaries.
emit sample |
rex "\xC7(\x85|\x45).{4,8}\xC7(\x85|\x45).{50}" [|
put o offset |
rex "\xC7(\x85....|\x45.)(.{4})" {2} [|
nop ]|
alu -s "0-101" --inc "B^S" |
carve -n 4 printable |
resub \\ \\ |
resub \" \\\" |
cfmt {o} : \"{}\", ]]
The snippet's regular expression matches a few unintended values, but it is not detrimental to set these as comments in the IDA database. We added the the output to the following IDAPython script.
import idc
decrypted_strings_dict = { ... }
for k, v in decrypted_strings_dict.items():
base = 0x400000
addr = k + base
comment = '"' + v + '"'
idc.set_cmt(addr, comment, 0)
print("comment", comment, "set at", addr)
Address translation is not necessary here because the file offset and virtual addresses in the .text section are the same.
Network communication and configuration
The sample communicates with a C2 server in a manner similar to what was discovered in November 2023 by the Any.Run team.
We used a Python script that was developed by an Any.Run researcher to decrypt network data. The threat actors have not changed their approach and are still using primarily TCP port 50500.
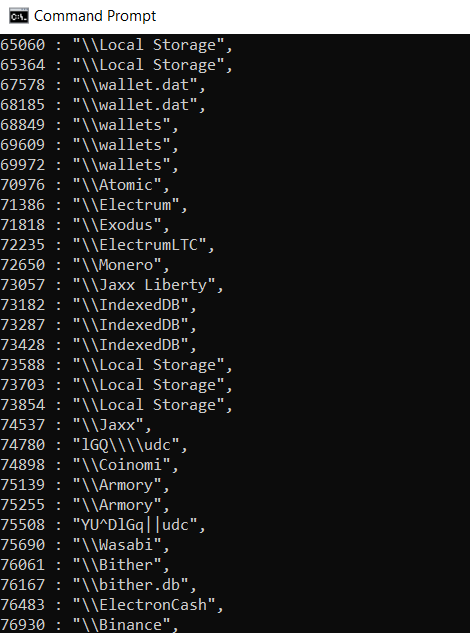
The configuration packet was especially interesting, as it contains information about grabber components, Telegram bot API token, and a Telegram message template.
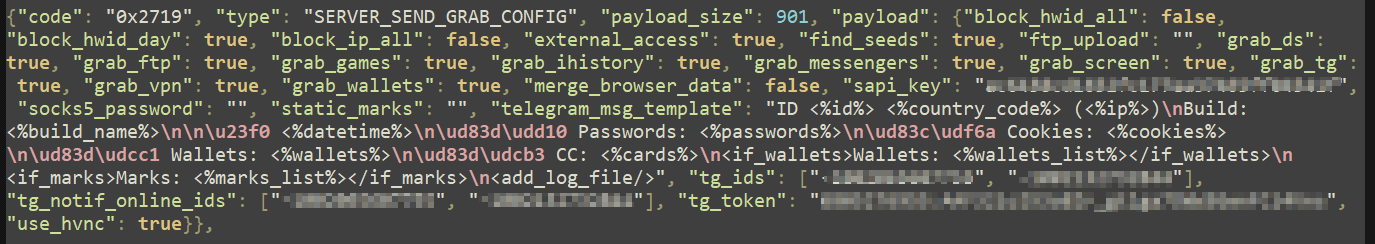
Another packet contained base64 encoded data that after decoding turned out to be a .zip archive with information from our analysis machine.
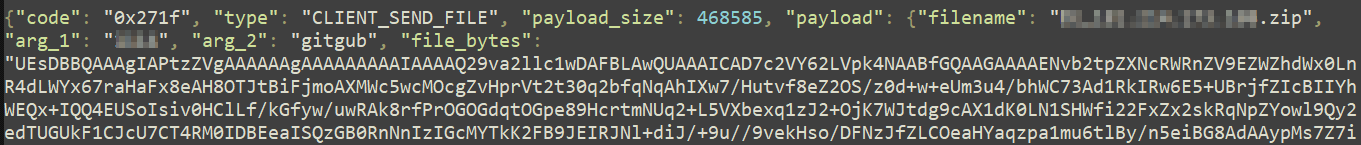
The data is exfiltrated to two Telegram channels. At the time of writing, both contained more than 700 messages with zip archives of stolen data. The combination of Telegram channel names and C2 IP addresses indicates a Russia-based operation.
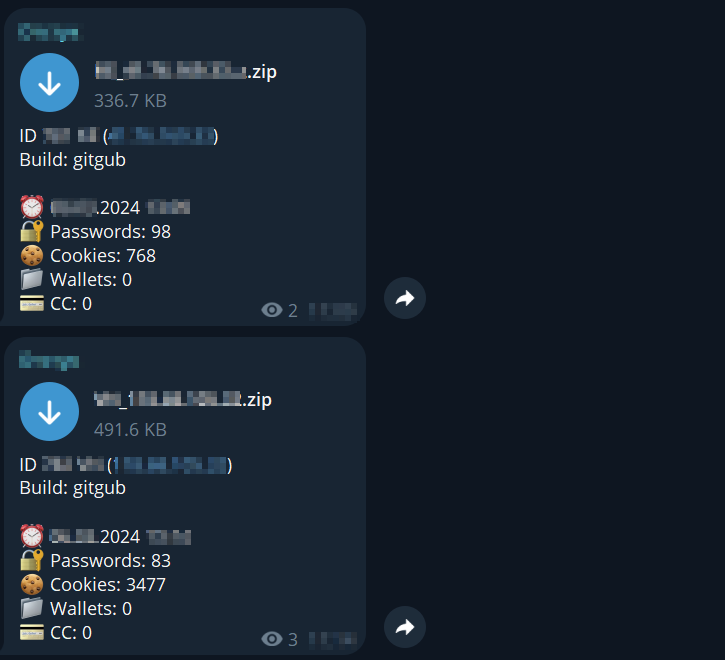
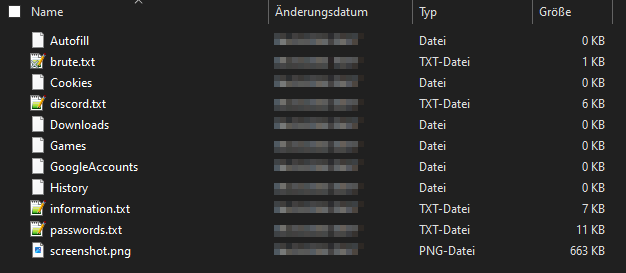
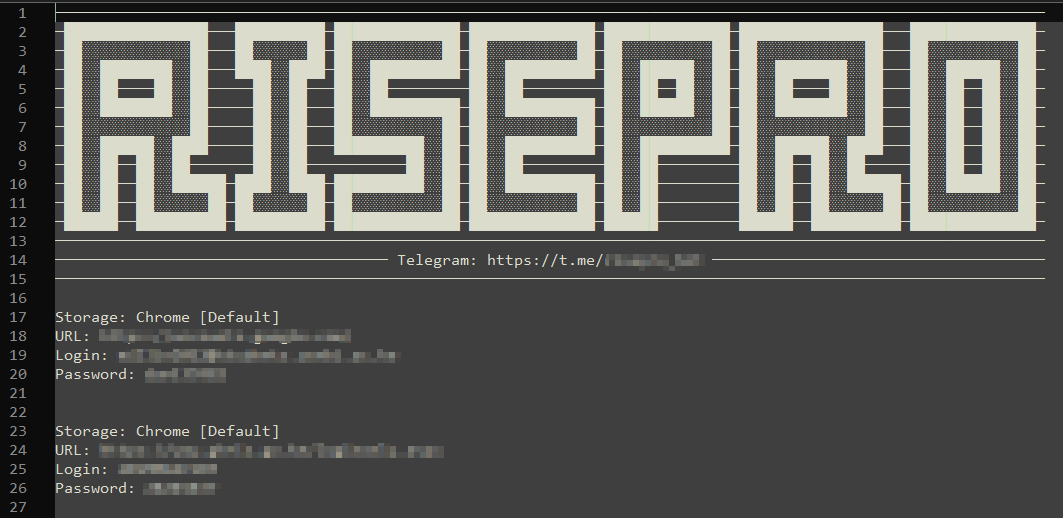
The malware collects a variety of valuable information. All unique passwords are stored in a file named “brute.txt”. In the file “password.txt” we discovered a big RISEPRO banner and the link to the public Telegram channel.
Indicators of compromise
| Description | File name | SHA-256 / IP / URL |
|---|---|---|
| [1] original RAR archive | INSTALLER PA$$WORD GIT1HUB1FREE.rar | f52ba7d8a820d32c502c4aaef4bf9690fc0ca97b97c683b43057d82c06294257 |
| [2] MSI unpacked from [1] | Installer_Mega_v0.7.4t.msi | 0ff1e4724b5b02a034789e328531f04a660fd1bade2ad9e73c8b748e5f3e0753 |
| [3] bloated file unpacked from [2] | Installer-Ultimate_v4.3e.9b.exe | 492a71bf56d2e89d0b9c5d70ed6c37acea89c8134fa5ba623bce74b3f0fb189e |
| [4] RisePro payload injected to RegAsm.exe or AppLaunch.exe | memory only | b0e194ed54bafa753bda5761c1264b67a5c438ee7a9ed624a83be913f037dcbb |
| [5] manually debloated from [3] | Installer-Ultimate_v4.3e.9b.exe | 059067376a6271fdead553b471ec899dec3662ec09bd5c3833911c87ea062e92 |
| [6] contacted IP | 176[.]113[.]115[.]227 | |
| [7] contacted IP | 193[.]233[.]132[.]32 | |
| [8] download link of RAR archive [1] | hxxps://digitalxnetwork[.]com/INSTALLER%20PA$$WORD%20GIT1HUB1FREE.rar |