"That's strange..."
Many important discoveries do not start with a shouting of „Eureka” anymore, as they did in the days of old. Instead, the most intriguing bits of modern research will at some point contain the phrase “That’s strange…”, followed by more prodding and poking and – hopefully – a lightbulb moment. This series that we call "Strange Bits" contains many findings that struck our analysts as odd, either because they do not seem to make any sense at the time or because a malicious program exhibits behaviors that none of us have seen before. Maybe these findings will spark ideas in other fellow researchers – maybe those findings are just what it says on the tin: Strange….
Skulls and Crossbones
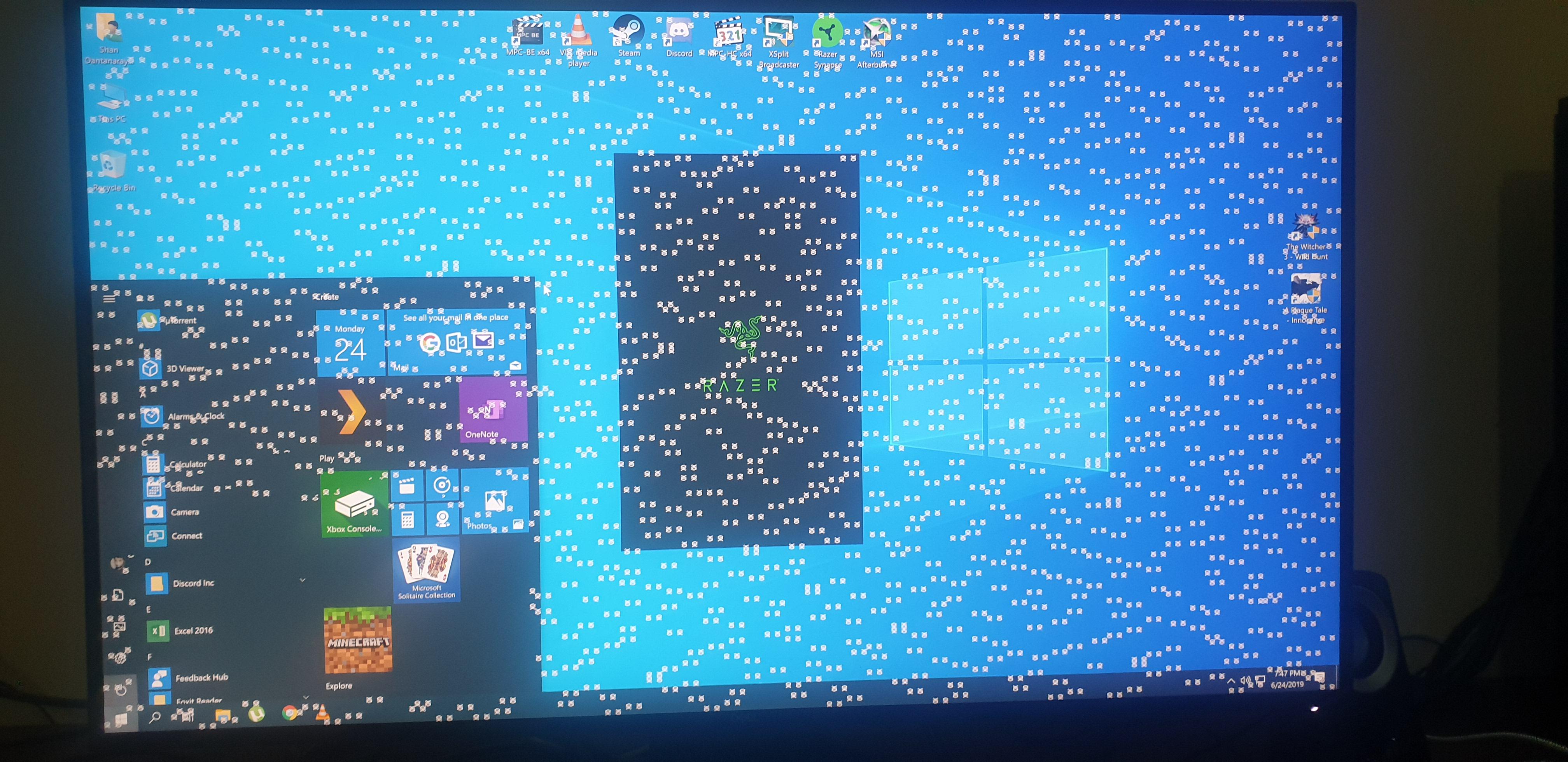
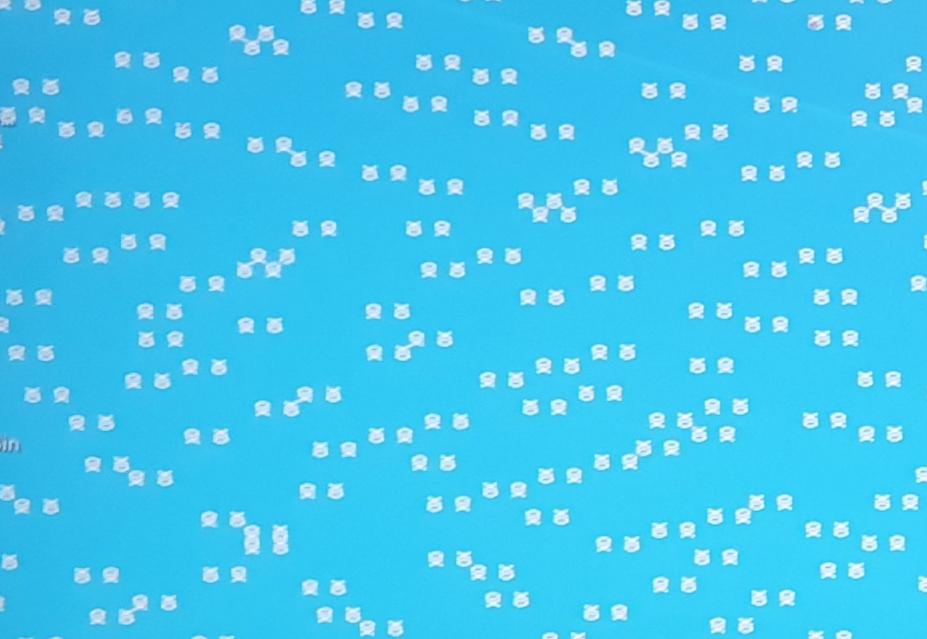
In the antivirus subreddit a user sought help because their computer was supposedly infected by a skulls and crossbones malware. Being a symbol that is associated with pirate flags, threat actors often use this to frighten computer users after infection. E.g., Petya ransomware is known for its skull and crossbones ASCII art, and stock photos that are used to illustrate malware-related articles often contain similar symbols.
What seems like a clear case of a joke malware or botched ransomware infection is actually a faulty graphics card. As a Reddit commenter pointed out, artifacts of Nvidia RTX GPU look this way. The original poster also complains that their system is stuck and their screen frozen. A working malware would probably rather show animations than freezing the screen. This system needs repaving or a new graphics card.
Bloated Malware
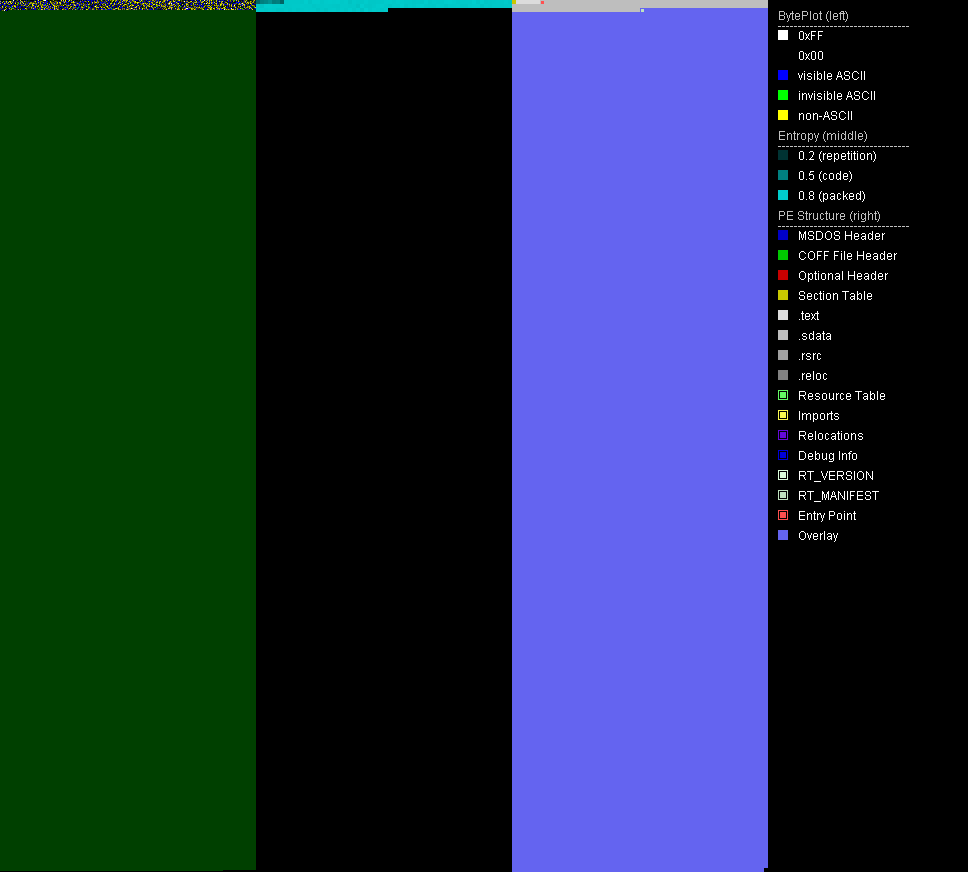
Some malware samples are big in size because they have been bloated artifically. This happens usually by appending zero bytes to the file. The most common Windows malware executable format, the Portable Executable Format, does not care about appended data. It will not be mapped to memory and is called overlay in this context. Malware may also bloat the last section or other areas of the file but overlay seems to be the most common. The bloat is well visible in file visualizations. The sample[1] below has been bloated with space characters in overlay.
This approach has some advantages for threat actors. Systems that allow file uploads, usually have file size limits. That means Virustotal or other automatic scanning or analysis systems may not be available for anyone who wants to check a file's maliciousness. The threat actors may hope that those files aren't distributed that fast to AV vendors, thus hoping to increase the time frame that their malware stays under the radar.
Threat actors use so called file pumpers to increase the size of their files and reduce the overall entropy which may indicate a packed file for some scanners. Some malware arrives in a non-bloated form and modifies its own copy on the system by adding appended data before deleting its original file.
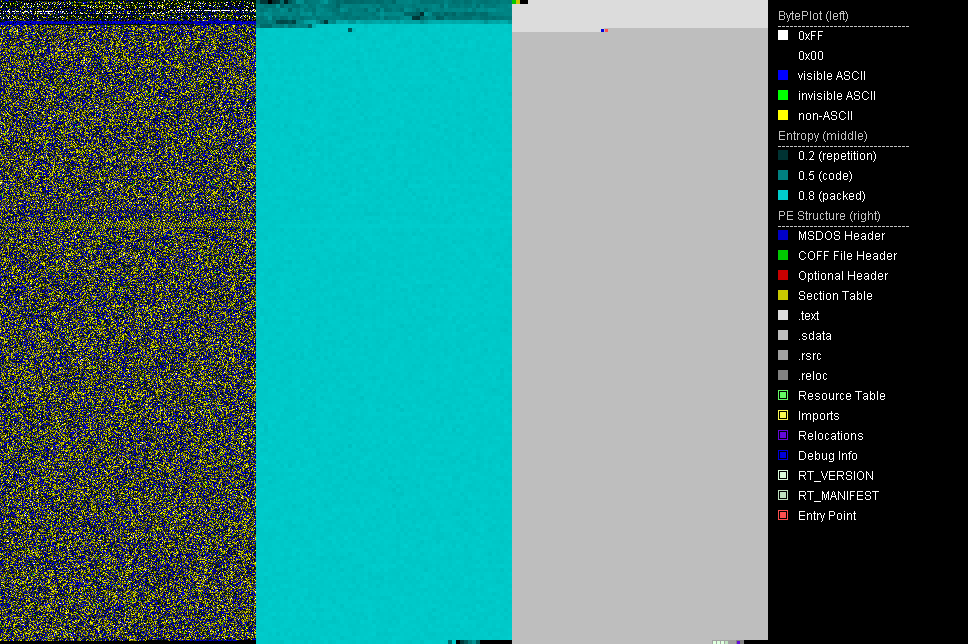
The solution may be to create a compressed archive. This will reduce the size tremendously because the bloat usually consists of uniform data, making the compression very effective. But this does not allow any analysis systems to execute the malware. Removing the bloated portion from the file by deleting its overlay is probably the best way to deal with it.
All-In-One Solution for Ransomware
The Ransomware subreddit is a place where users frequently ask for assistance after their systems got infected by ransomware. One poster promised a solution for everyone by advertising a free "Ransomware Removal Tool"[3]. They provided a mediafire download link to a password protected archive that contains the tool. The advert claims the tool will remove all common ransomware infections from the system and the entire network, except for the latest ones.
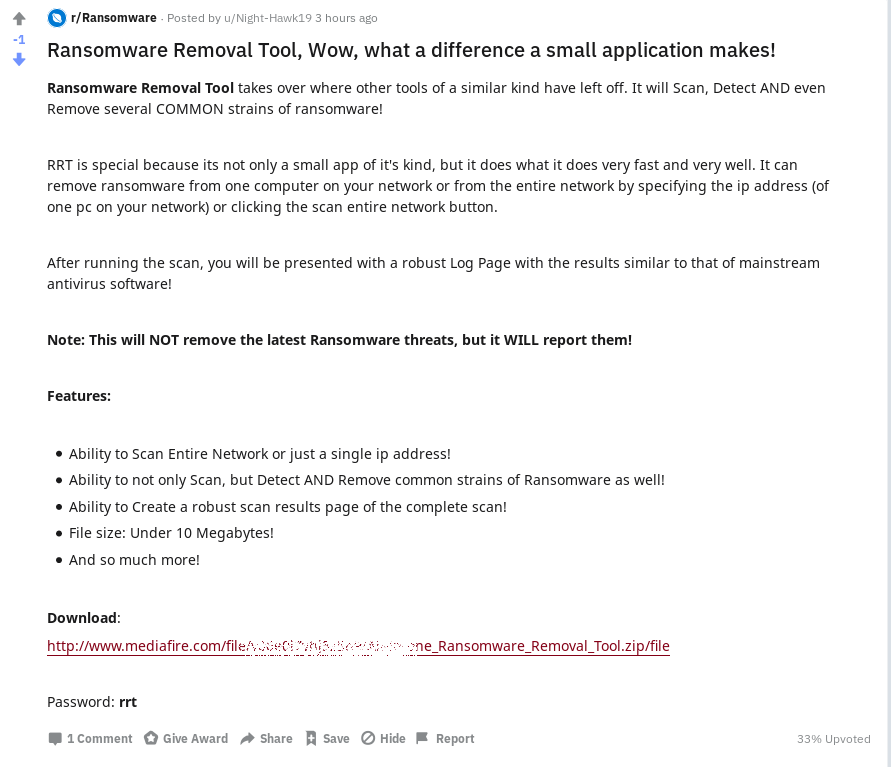
The archive contains the application named "All-in-one Ransomware Removal Tool.exe" and an "info.txt" file. Detect it Easy identifies the application as an AutoPlay Media Studio file. After using a static AutoPlay Media Studio unpacker we find the main code in "All-in-one Ransomware Removal Tool.exe_unpacked\_extracted_cdd\_proj.dat". There are also lua51 dynamic link libraries among the unpacked files, which indicate that the code is written in LUA.
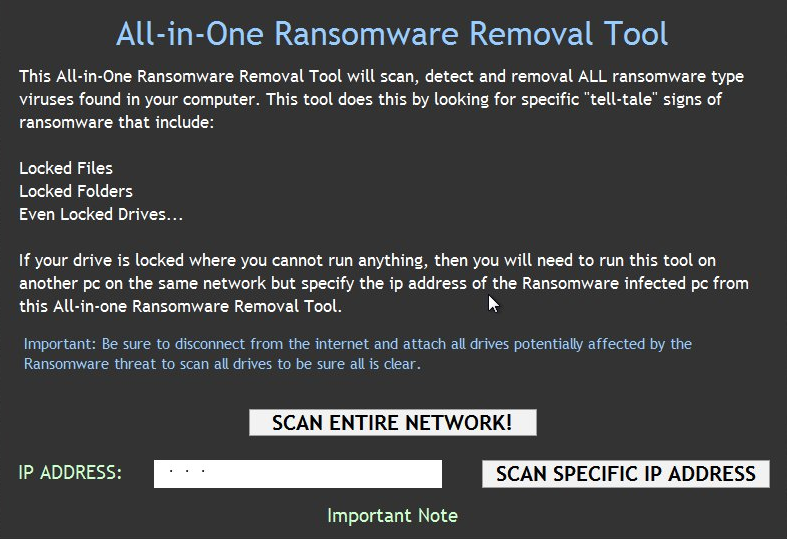
The main code in _proj.dat imitates two system scans. Each scan calls "testing.bat" 100 times, each time it updates the progress bar for one percentage point.
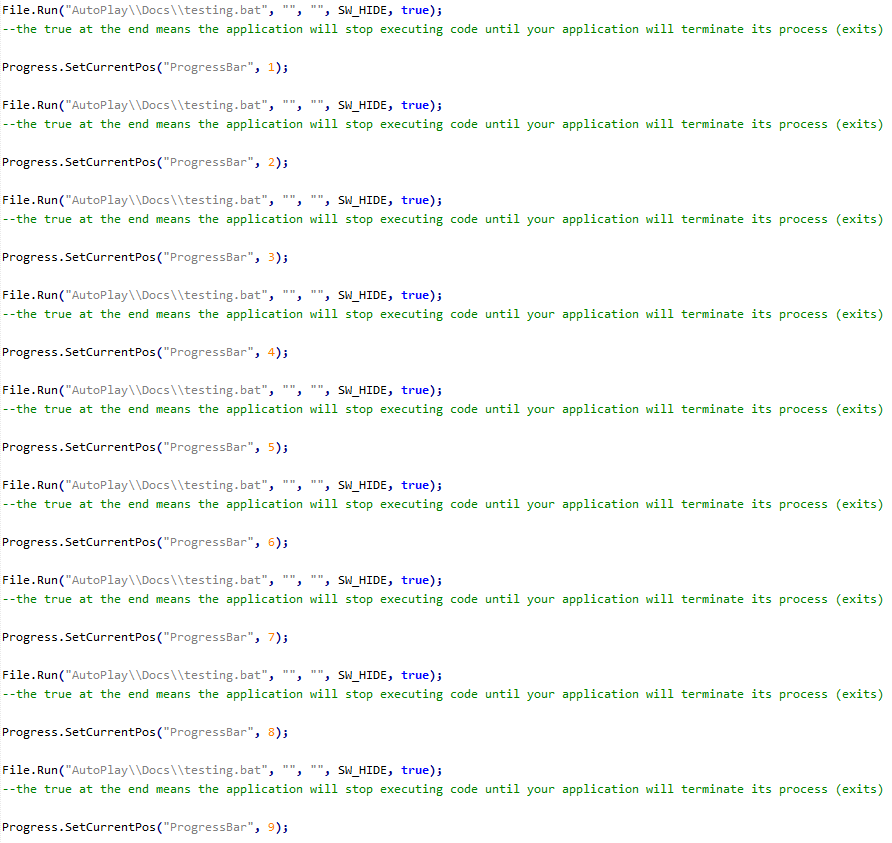
The "testing.bat" checks every drive letter and replaces existing files on those drives with "nul", which means it replaces these files with empty files. Since the batch file is called 100 times per scan and the application performs at least two scans, it will replace all files on the system at least 200 times.
We conclude that this "All-in-One Ransomware Removal Tool" is a dilettante wiper which keeps the advertised promises - it deletes the ransomware from the system. Alongside all other files.
Referenced Samples
| Description | Detection name | SHA256 |
|---|---|---|
| [1] Bloated malware | Win32.Backdoor.Bladabindi.HVE1JT | 9c5ab94ba1231ea2caf36dba53aecff09b7f9af9df5ae2557a691e0abd9184ff |
| [2] Malware sample in [1] after removing the bloat | Gen:Heur.MSIL.Bladabindi.1 | 0a8564c151f216eeaba363cba83b9b097b09fccc4bac7f9413ccc2d1cf905061 |
| [3] All-in-One Ransomware Removal tool | Win32.Malware.Wiper.4NJ0XF | 6e559865aa7243e1146c5edf18e52c77eecc1fc6d12c89e4bb9816d6f3f557f2 |