Brute-forcing login credentials is a tried and true method for criminals. The more computing power a criminal has at his disposal, the quicker the designated tool can find a valid login. But then, not every criminal has the means or motivation to set up a dedicated password cracking rig. To this end, criminal actors can make unauthorized use of other people's computers. This is where SilentBruter enters the stage. This malware covertly makes an infected machine guess passwords on different online platforms. In the example below you can see that in this particular case the target are php-based websites and discussion boards.
Since this is a very widely used platform, harvesting credentials in bulk can have severe consequences for the operators of an affected website or discussion board. It puts the attacker in a position to disrupting activities on a website or to place malicious content there in order to infect any visitors who access the page. With administrator credentials, it is also possible to completely destroy the contents of a website.
This is the first-hand account from our analyst:
"I’ve stumbled upon this unique malware[1] while browsing the analysis platform "Any Run". This particular submission caught my eye because the HTTP request tab from the submission looks very suspicious. I therefore started investigating this malware, which was submitted with the filename “readme.exe” .
Obviously, the file name in combination with the *.exe file extension is already a dead giveaway that something dodgy is going on, but no matter - here is what I found:
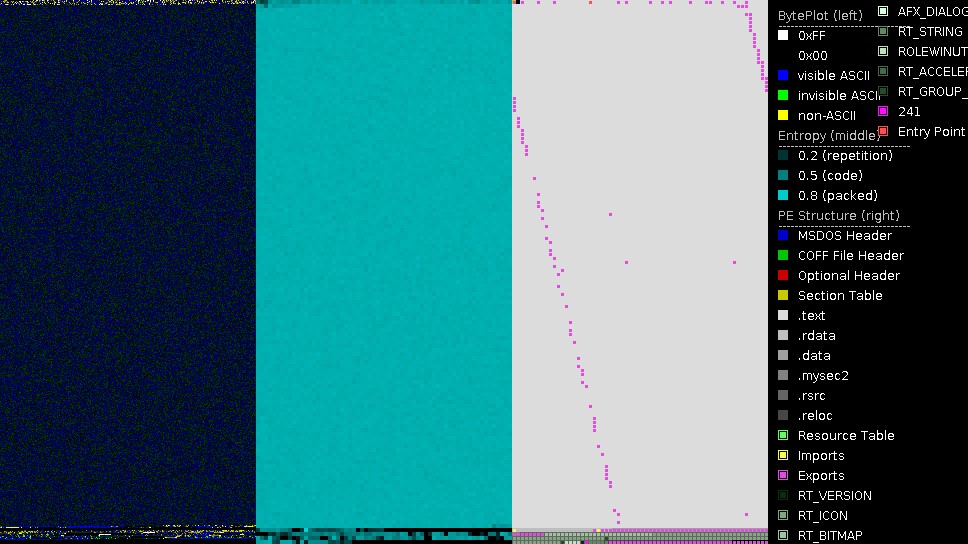
Initial layers of Silentbruter
The file uses a UPX packer. After unpacking the sample, the PortExAnalyzer presents the structure as shown below. The exports, represented by the pink squares, are fragmented and strewn across the entire file, whichin and of itself is very unusual for an executable. The high number of export symbols and invalid exports cause some debuggers to crash, for example older versions of x64dbg. Whether or not this is intentional on the part of the author is anyone's guess, but maybe it is a crude method of analysis evasion. As the entropy is high, the sample is likely not fully unpacked yet. The mostly turquoise color in the mid section is indicative of this.
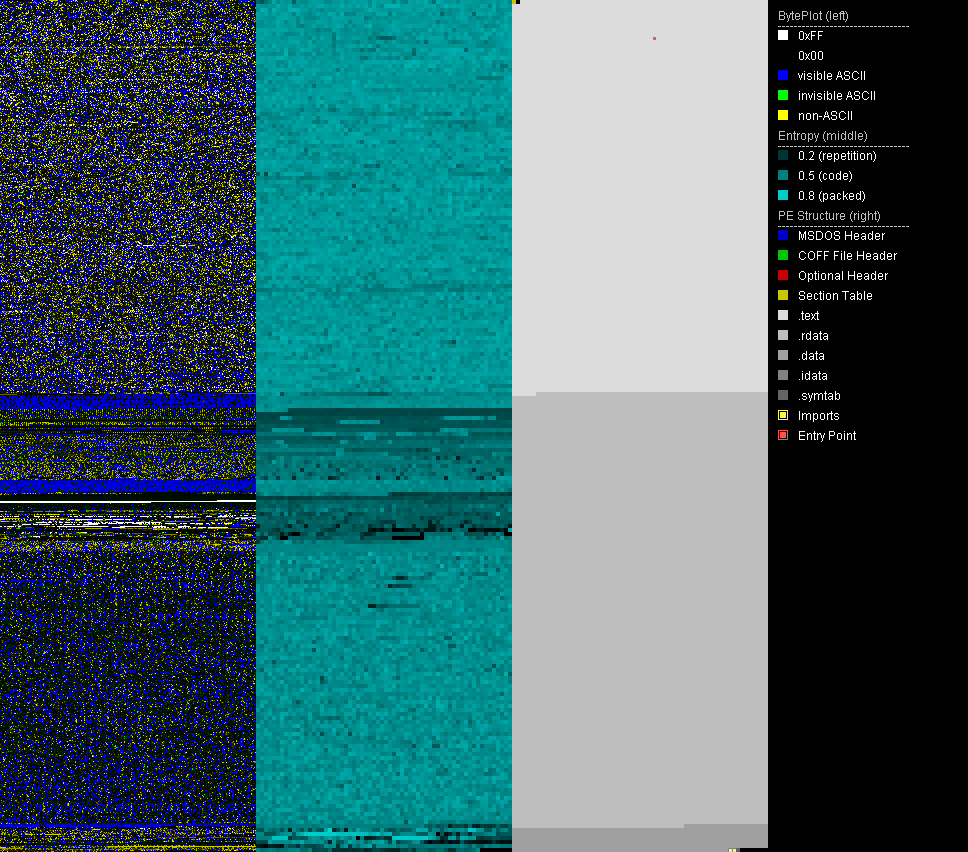
Final layer of Silentbruter
After unpacking, we're presented with the last layer - the unpacked sample[2]. This is visualized by the darker turquoise entropy section in the middle. The strings of the unpacked sample reveal typical strings for the GoLang programming language, e.g. GitHub packages, functions and datatypes. Therefore we can conclude that the malware is written in GoLang.
C2 communication
First connection request: In the picture below you can see that the trojan connects to the c2, exposing the current OS(Windows) that the infected machine is running.
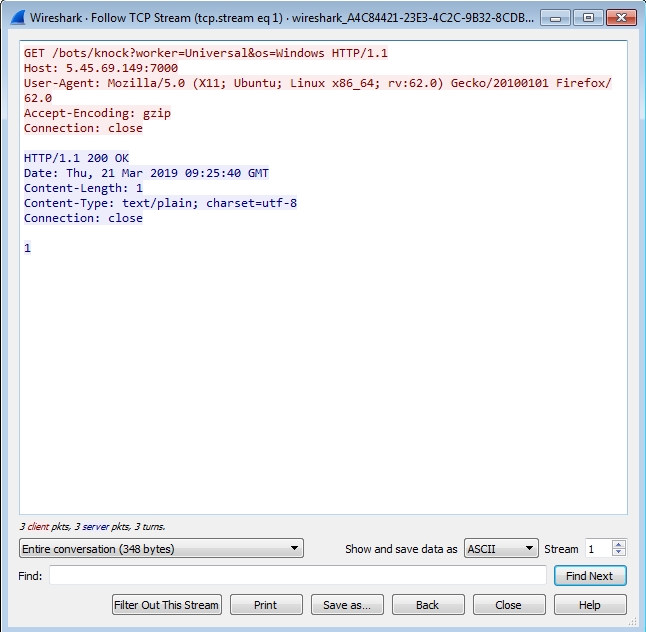
Second connection request: The HTTP request below shows that the trojan connects to the c2, which returns a list of service types the infected machine should perform brute force attempts on.

Third connection request: Below, you can see that the trojan connects to the c2 with the GET parameter “worker” and the value “php_b”. In response, a JSON object is returned. It contains a host, a login, a password and a worker field. Those fields are the configuration file for the brute force functionality in the trojan.
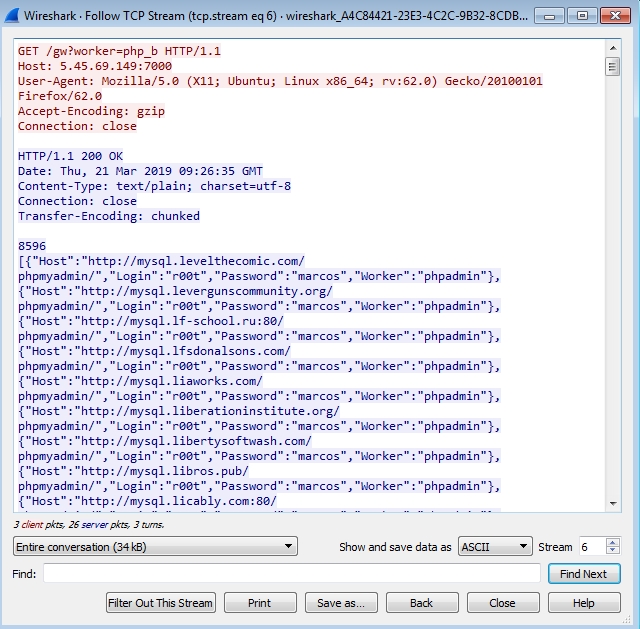
Fourth connection request (Brute force): Once the configuration file is retrieved, the trojan will log in to every host in the JSON object provided.
The login panel
The astute reader will have noticed the IP in the Wireshark window above. Visiting the page hxxp://5.45.69.149:7000 redirects to hxxp://5.45.69.149:7000/login.
This appears to be the c2 server, protected by a username and password.

Folder structure
With the tool DirBuster it’s possible to brute-force directory and file structures from a webserver. If you will, this tool brute forces the brute forcer.
hxxp://5.45.69.149:7000/static/img
This folder contains a file geekslabs.png, which is the domain of the web design company geekslabs.com. This indicates that the author uses a theme from that company, so some thought was given to the look and feel of the backend. Whether or not the c2 operator has actually purchased a theme there or pirated one is not clear.
hxxp://5.45.69.149:7000/static/assets
This folder reveals used software for the c2 backend, such as chart-master, chkeditor and more. The README.md file from the chkeditor subdirectory states that the server is running chkeditor v4, which is known to be vulnerable for exploits (Exploit-DB, Packetstormsecurity). I guess this goes to show that criminals are just as likely to use outdated software that is prone to vulnerabilities as the average user.

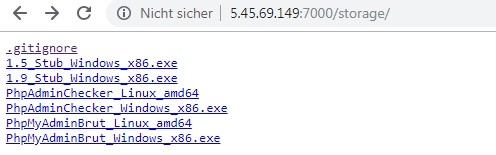
hxxp://5.45.69.149:7000/storage
This folder contains Windows and Linux binary versions of the trojan. The Windows files are detected by most popular Anti-Virus solutions, whereas the Linux files are marked as clean. A similarity search on VirusTotal for the Linux binaries only reveal unrelated results. Based on this, we can assume that the author has the intention to include Linux systems in his target group as well at some point, but for some reason has not started with it yet.
A similarity check for Windows binaries revealed the submitted filename search.exe, which was submitted on January 13, 2019. From this information we can conclude, that the author has been running brute-force attacks for some months ago already. It is safe to assume that the attacks are still underway as of this writing and also likely to go on in the future, in case the attack proves to be successful.
The picture below shows the files inside that directory.
Referenced Samples
| Description | Detection Name | SHA256 |
|---|---|---|
| [1] Packed SilentBruter | Win32.Trojan.SilentBruter.A | 46fd1e8d08d06cdb9d91e2fe19a1173821dffa051315626162e9d4b38223bd4a |
| [2]Unpacked SilentBruter | Win32.Trojan.SilentBruter.B | 05073af551fd4064cced8a8b13a4491125b3cd1f08defe3d3970b8211c46e6b2 |
If you want to stay updated about malware, be sure to follow these accounts:
RansomBleed - My personal twitter account about the latest malware reports.
GDataSoftwareAG – G DATAs twitter company account."

