Ransomware payments are just the tip of the iceberg when it comes to talking about the costs in damage that ransomware causes. In fact, the amount of ransoms paid is dwarved by other factors. The real damages inflicted by ransomware includes losses and costs on the following:
- Data loss
- Operation Downtime
- Resetting and replacing infrastructure
- Productivity
- Forensics
- Reputation
- Life - in the case of healthcare industries such as hospitals or other medical organizations
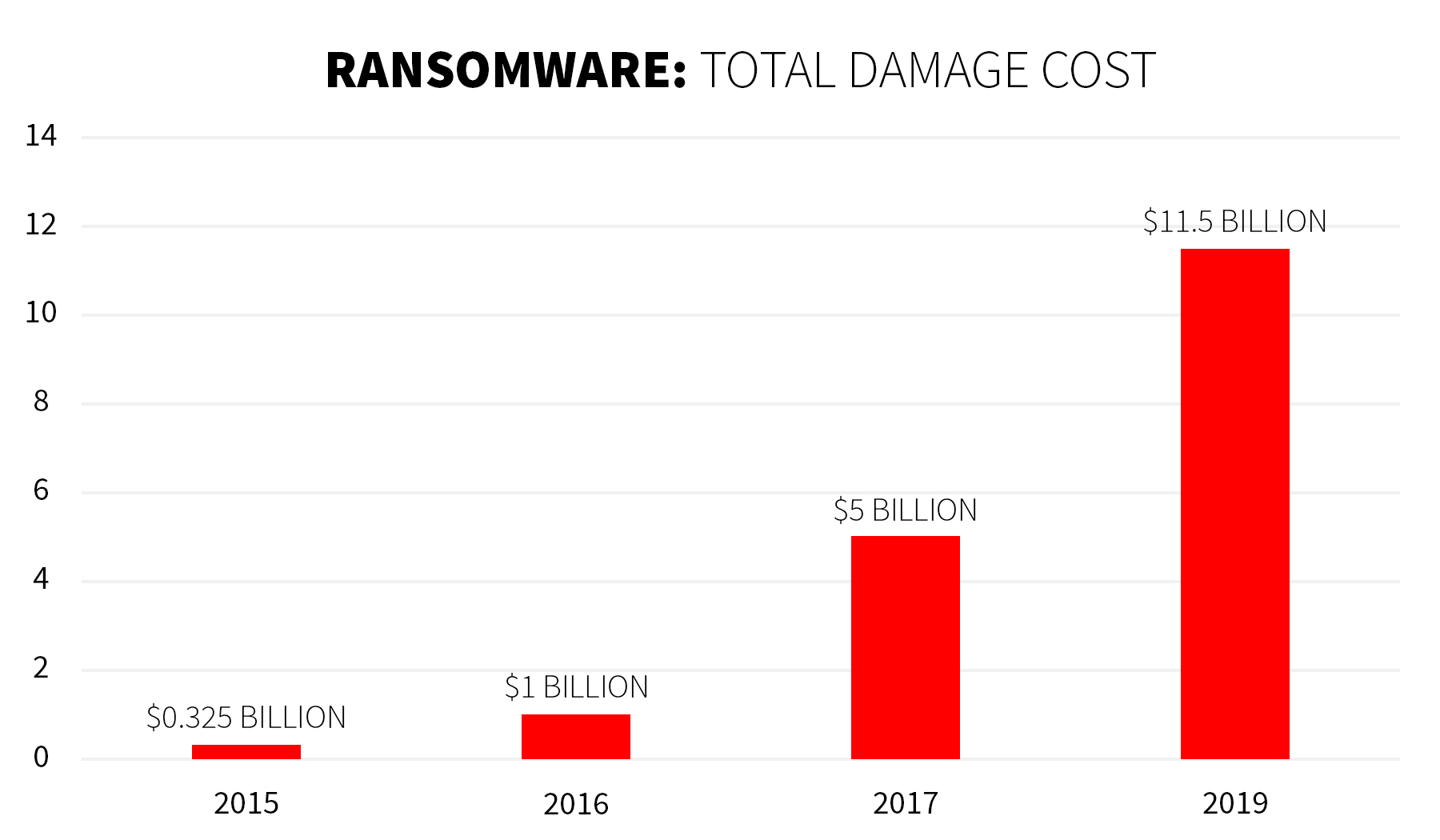
According to CyberSecurity Ventures, one of the world’s leading research and publishing firms that cover the global cyber economy, ransomware damage cost worldwide might reach or even exceed to a whopping $5 billion by the end of 2017. That would constitute a 5-fold increase from 2016 and is estimated to increase another 15-fold in just 2 years. Global ransomware damage cost is predicted to exceed $11.5 billion annually by 2019.
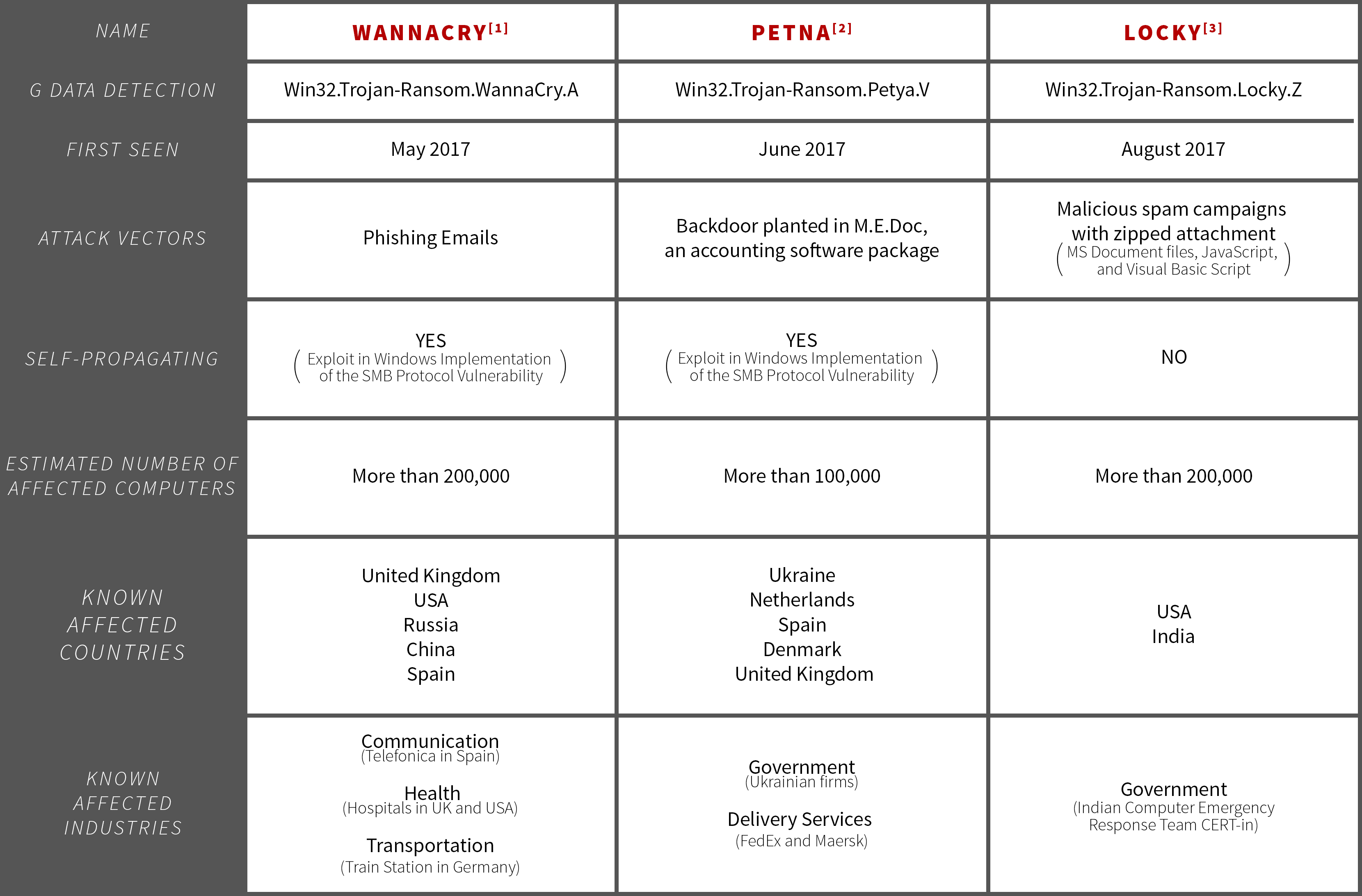
Let’s have a look on this year’s most prolific exponents of ransomware and the way in which they managed to inflict this amount of damage. Based on the table on the right, a pattern seems to emerge, according to which malware authors focus on industries where securing critical client information is a vital part of everyday business. This strategy proved successful in forcing victims to pay their ransom and some even suffer negative impact on their reputation. Petna, however, is different as it was never designed with profit in mind. Instead, its objective was to disrupt operations in affected organizations.
eXploit FACTOR
Most of the well-established ransomwares have been using two highly effective attack vectors: spam emails and exploit kits, as shown on Figure 3. There’s nothing new about these - spam emails are still peddled by botnets and malvertsing has seen extensive use in tricking a user into executing agents of ransomware. Some attacks use exploit kits in order to deliver the ransomware, but they often still require user interaction. The act of ransom is still the same. Most ransomware families continue to use AES and RSA encryption algorithms. Oftentimes, the files cannot be decrypted or recovered for free, unless the cryptographic components have been implemented incorrectly or a decryption key is found. Payment transactions are mostly performed using cryptocurrencies and TOR (The Onion Router), which makes it difficult to track malware authors down. Several ransomwares, such as CryptXXX have been using additional tools for credential stealing. This is to make sure malware authors never leave the field empty-handed, even in case a victim refuses to pay. This approach has been adopted by Petya, Bad Rabbit, and new variants of Spora. So, what has changed?
One of the more notable changes in this year’s ransomware is the incorporation of exploits that attack vulnerabilities in network protocols. The exploit in question enables the ransomware to display worm-like characteristics which enable it to spread laterally without requiring any user interaction. This is popularly recognized as a “Ransomworm”.
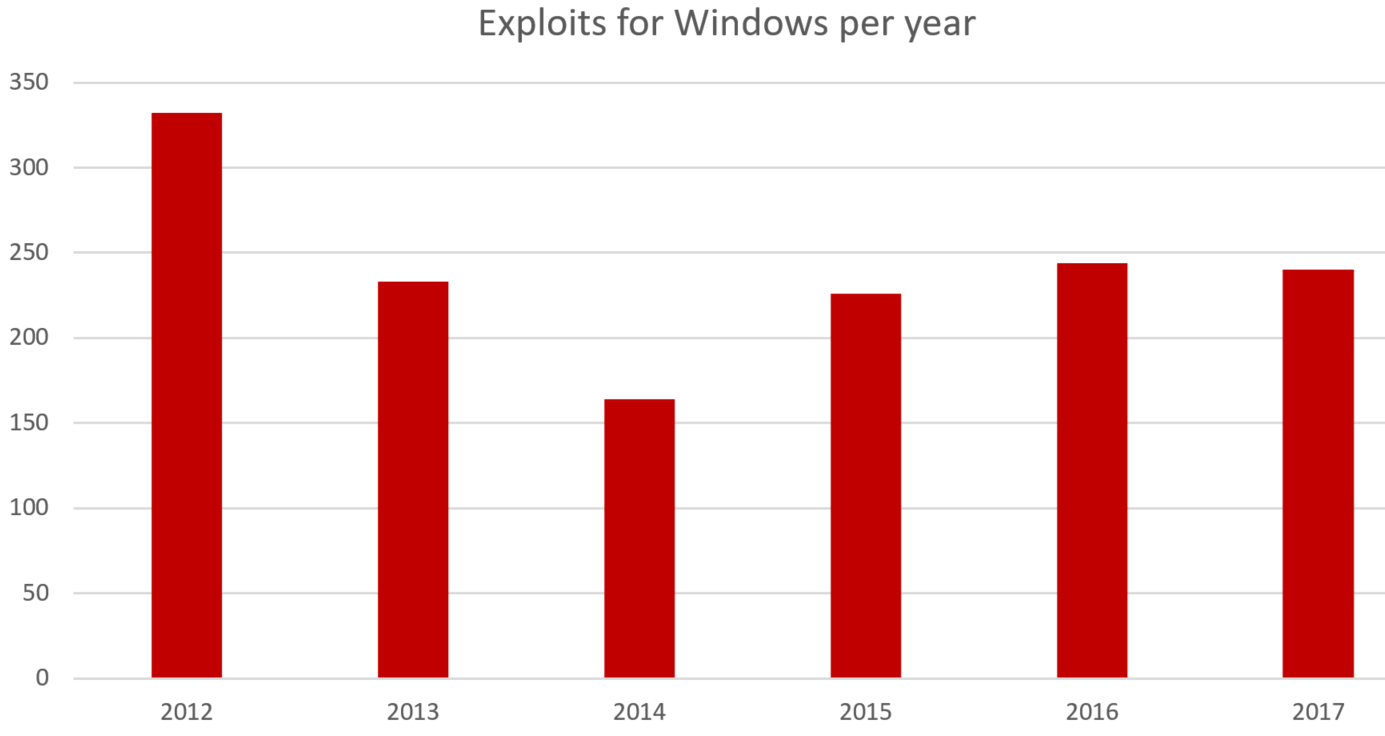
Let's focus on WannaCry, the ransomware that broke new ground in 2017. The total damage from this ransomworm was estimated at around $4 billion and infected more than 200,000 computers. WannaCry was able to further spread its infection through the “Eternal Blue", a leaked exploit project of the National Security Agency (NSA). It takes advantage of a Microsoft Windows vulnerability in the Server Message Block (SMB) protocol, which is used for network file sharing that is enabled by default. It is important to note that this Windows vulnerability had been patched already in March 2017 (patch MS17-010), two months before the outbreak of WannaCry in May 2017. This indicates that the infected machines were either not updated in time or the operating system was too old to receive the patch, which is likely on Windows XP and older Windows OS versions. Just by looking at the staggering number of vulnerabilites shown below, it is possible that malware authors will take advantage of these existing vulnerabilities and specially crafted exploits for their malicious intent.
The numbers are scary and daunting, but let’s look at the bright side (yes, there is one). As mentioned previously, the patch of the vulnerability exploited by WannaCry was released before the outbreak occurred. All it takes are properly updated machine within the network to contain the ransomware infection to just one machine. This data shows that updating software and upgrading to the latest OS is the best way to go.
Don’t Be a Victim, Secure Yourself
Though it sounds cliche, “Prevention is better than cure”, it is true for all the ransomware attacks this year. There are simple ways that you can practice to prevent you from falling victim. So here are some practical tips:
• Always back-up important files. It is recommended to save it in another device like external storage away from your local network. Another option for backing up your files is through the in-the-cloud system
Keep your backups disconnected (unless you run the backup).
• Keep operating systems and software up-to-date, including security updates
• Implement end-user and network policy to mitigate risk of being attacked from external and internal sources
• Don’t click the links and download file attachments from malicious website and suspicious e-mails respectively
• Disable auto-execution of scripts such as macros, javascript
Because of the success of the ransomware campaign in 2017, expect that there’s more to come. Let’s pick up what we’ve learned to help us arm ourselves for the years to come.
Information for fellow researcher: Notable hashes
"09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa" [Win32.Trojan-Ransom.WannaCry.A]
“eae9771e2eeb7ea3c6059485da39e77b8c0c369232f01334954fbac1c186c998” [Win32.Trojan-Ransom.Petya.LZFBDH]
“2eecbe4d4267f00eb925089939f52ebacc228c720e3c8e81afe479dc014dff9e” [Win32.Trojan-Ransom.Locky.EF]