The vulnerabilities known as Meltdown and Spectre are not related to flaws in the operating system or software in general. This time the core of a computer is affected - the CPU. Its main task is to process instructions, while making sure that each process can only access its own data. This is achieved by implementing a concept called "memory isolation". It was given high significance in the design of CPUs. Modern CPUs are profoundly optimized to fulfil their main purpose efficiently and quickly. As a consequence, instructions are not processed in their "natural" order. Instead, they are processed "out-of-order", rather than in a fixed one-by-one queue. Processing commands in the order they come in is inefficient, because that leads to pauses, especially if the program logic branches. This translates to slower overall processing speeds, during which the CPU has to wait for one command to finish or wait for the output of one program routine which is required to continue the task in hand. A special buffer (called Reorder Buffer, ROB) is filled with the next set of instructions. In order to keep it filled, some instructions are executed speculatively. In simplified terms, the processor guesses what might come next and starts processing. This data is discarded later on if it is not needed after all. This data is usually only available in the processor's internal cache. Thus it is not visible to the rest of the system. With some clever trickery based on side-channel-attacks it now became possible to make this concealed content available to the active memory without any special privileges. See here for a more detailed description.
This quick overview shows the complexity of this topic and it becomes evident that this is not the main track of IT security research. Nevertheless Anders Fogh has been investigating this fascinating area for quite some time. Anders is one of the few people on this planet who has been deeply involved into the discovery of Spectre and Meltdown.
How did you come across the flaw?
Together with researchers from TU Graz I have done research about the relationship between privilege rules and their enforcement in the CPU. We presented this work at Black Hat USA 2016. I then researched another part of the CPU for problems related to so-called covert channels. In January 2017 I was able to link up these two research topics, which lead into the core problem with Spectre and Meltdown. Read the full story here.
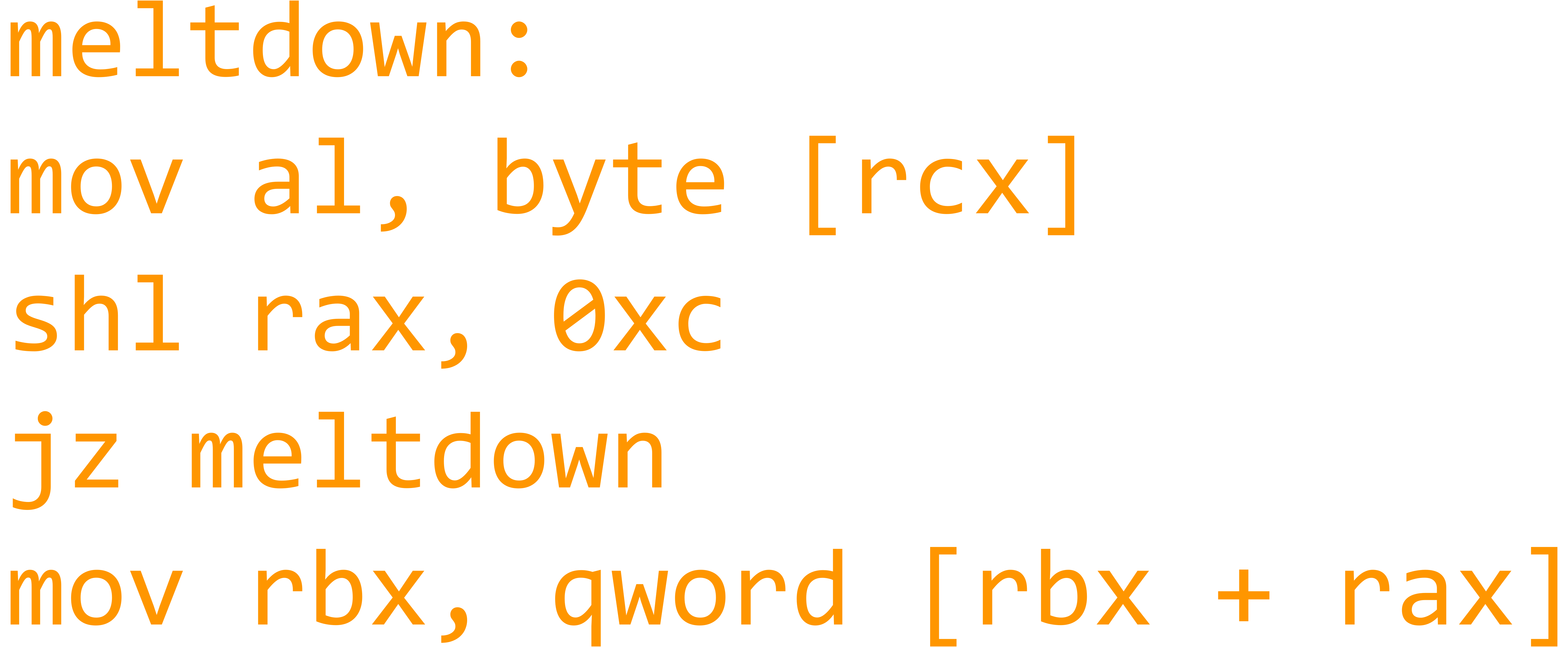
We have seen many vulnerabilities throughout the last decades, some with a huge potential. But despite their potential we have never seen them exploited by malware. The wide coverage of vulnerable systems is something that attracts malware writers. But sometimes it is not so easy to create effective exploits.
How likely is it, that we will see malware exploiting Meltdown and Spectre in the near future?
We are likely to see malware implementing Meltdown. There is already source code for proof-of-concept and exploits circulating on the internet. It is therefore vitally important to update your operating system. Spectre is a lot harder to exploit, which makes it likely to take a bit longer for this to make it into widely distributed malware.
Meltdown and Spectre deal with hardware. Software developers usually don't have to care about hardware peculiarities, because operating systems and hardware abstraction layers take away this pain. This does not apply in this case.
How does the malware code scale in terms of hardware and OS?
In terms of CPU-hardware each vendor has a wide variety of products and models, which differ in system architecture and other specifications. It is unlikely that there is a universal attack code which runs on all vulnerable CPU platforms. The devil is in the detail. It might take substantial effort to create effective exploit code that runs on various CPUs. In addition to this, the differences between operating systems need to be handled differently to exploit the vulnerabilities.

The attack potential of Meltdown and Spectre is information leakage. There are evident threat potentials in server environments and on desktop PCs, notebooks and smartphones.There might be less obvious attack scenarios that security folks should care about.
What kind of attack scenarios can we expect?
High-performance CPUs are used in many devices in both entertainment and industrial settings. The more powerful a CPU is, the more likely it is to be affected. On the other hand attackers think economically. Meltdown & Spectre enable information leakage attacks. But it’s not profitable for attackers to run a full information leakage attack against all affected devices, simply because many of these devices don’t hold data that is valuable enough to justify the necessary effort. This might be different in cases like hardware routers and firewalls.
Taking the view of an attacker. The information that is available in the kernel memory might be abused for more severe attacks.
What can attackers achieve when they use Meltdown in malware?
Usually, malware on modern operating systems is limited to the user and the security level it first had during infection. This is particularly important for shared machines like in business or generally server environments. Meltdown allows malware to effectively read any information from the operating system kernel. There is plenty of information in the kernel that will make it easier for malware to achieve “privilege escalation”, allowing the malware to fully take over the infected machine, regardless of the user or security level.
Security flaws like Meltdown and Spectre often have a life-cycle. When a threat is newly discovered, there are often just a few experts who know about it. Once the information is going public, there is abundant press coverage and public attention. As the vulnerability matures, exploit code is developed and eventually used by malware. By the time this happens, public attention has usually waned and is either at or very near zero already.
Which long-term effects are you expecting?
The underlying issues relate heavily to trade-offs inherent in CPU design and manufacturing. Thus we are likely to see issues of this kind going forward. Most issues, however, are likely to have a less dramatic impact than Spectre and Meltdown.
The discussion about Meltdown and Spectre is ongoing and covers many aspects. Sometimes certain aspects are overrated or neglected.
What is most important from your point of view?
Computer security is a long term project and Spectre and Meltdown needs to be seen as a step on this journey. It puts a new emphasis on the CPU’s role in computer security that will hopefully spur interest in how we can design secure computers.
Looking for flaws in CPUs has not been the mainstream of security research. Encouraged by the findings that now lead to Meltdown and Spectre, the expectation could grow, that there are other areas in the realm of CPUs, that have similar effects.
What’s next? Do you expect other hardware based flaws?
CPUs are remarkably complex devices. The number of transistors in some modern CPUs exceeds 3.000.000.000 (three billion). For comparison, this is about 1000 times as many parts as the Saturn V rocket, which took men to the moon - and it’s all in your computer. With that kind of complexity, it is likely that we’ll be able to find other issues.
Image credits
The "Meltdown Code" illustration and the "Spectre"-Logo were designed by Natascha Eibl and are licensed under the CreativeCommons Public Domain Dedication license


