According to a recent analysis by Checkpoint, devices with older versions are primarily affected by this. Gooligan uses two well-known and well-documented vulnerabilities to gain root access on an infected device. Following infection the device then downloads and installs more apps. This is meant to boost the downloaded apps' download count and therefore its ranking.
If this sounds familiar, you are right: Earlier this year the HummingBad malware gained some notoriety for employing the same technique.
What are the risks?
Since Gooligan, just as HummingBad, roots devices an attacker in theory has full access to all data stored on the device. While there have been no reports so far about user data being actively accessed, the technical possibility exists.
To download additional apps Gooligan steals the access token of the account the user is currently logged on with. If the attacker has access to this token he can access all the Google services the token is authorized for. The Google servers then verify the token, find it to be valid and then grant access. This also renders measures to secure an account ineffective, such as multifactor authentication.
Access tokens
You could compare an access token to an ID card that you get when working in a large office building. Whoever has this ID card can move around freely on the premises without being further challenged. Should someone steal this ID card, he can move just as freely and also has the same access permissions as the actual holder of the ID.
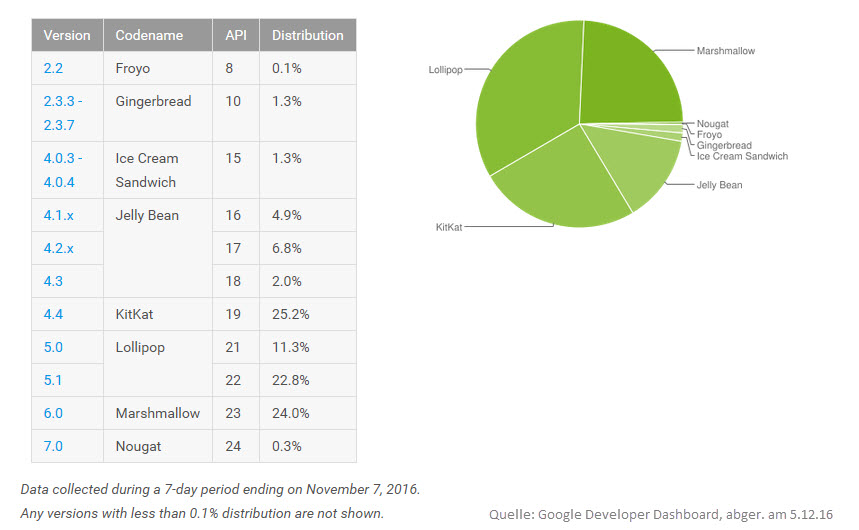
How many devices are affected?
Potentially all smartphones and tablets are affected which have Android 4 or Android 5 installed and which download their apps from an unofficial source. Devices with a current version of Android and with the latest security patches are not affected. However, there are still many devices out there for which a new version of the Android operating system is not (yet) available. The "Kit Kat" and "Lollipop" versions of Android alone account for almost 60 per cent of all active android installations.
So far there are no indications that Gooligan is being deployed in a targeted manner against single individuals or organizations.
What action does Google take?
As of now, Google has gotten in touch with affected users. Any stolen access tokens were revoked. Users need to re-authenticate after taking care of the malware infection. Unfortunately, the only reliable method of removing Gooligan from an infected devices is performing a factory reset. This also removes the illegitimate root access and ensures that the offending app is not present on the device anymore. Any apps which were boosted in their ranking as a result of Gooligan's actions have already been pulled from Google Play.
Additionally, a list of apps known to be infected with Gooligan has been compiled by Checkpoint.
How can I protect myself?
The most effective protection is the use of a version of Android which does not have the security flaws exploited by Gooligan. Since this is not always possible, great caution should be exercised when using unofficial app sources. As G DATA researchers have found out, up to one in four applications from certain unofficial sources is laden with malware.
Extra caution is advised if a smartphone or tablet is used in a business environment and if it belongs to the risk group mentioned above. Depending on the nature of the data stored and processed on such devices the data might be accessible to unauthorized parties.
Installing an effective malware protection on mobile devices is therefore not just a commodity. This holds true for both home users as well as business environments.