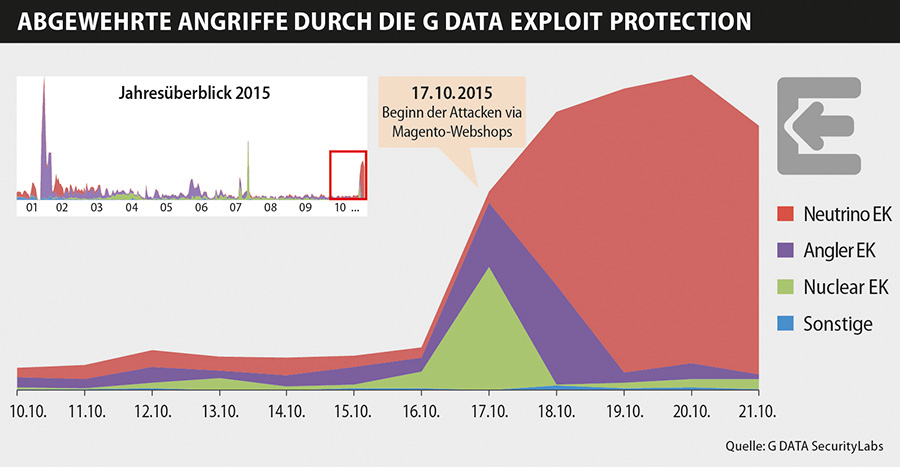
Legacy Security Holes
As outlined in part #1 of the series, attackers will only put in the required amount of effort to mount an attack and to compromise their target. Attacks such as the one by Stuxnet which use multiple zero-day vulnerabilities are not something that researches see on a daily basis. In fact, the opposite is true. Due to budget considerations - zero-days are an expensive commodity - they re not used very frequently and only when required. Given their nature, researchers also have a hard time identifying and categorizing them in a statistically relevant way. This does not mean, however, that the danger is not real - the likelihood of being hit with a zero-day exploit are lower than often perceived. To add some numbers to it: among the 326 cases Marschalek and Vinot have examined, the lead position in terms of exploits was based on a vulnerability which was discovered in 2012. Therefore, the risk of facing an attack which uses an old exploit is significantly higher. As a result, the mantra-like argument by security experts to install updates still holds true. By installing current updates and plugging known security holes organizations potentially increase the cost for a successful attack against their infrastructure.
Curiosities: Stealing a 0day & Learning from Hashes
One particular exploit has only made it into the tool boxes of several APT groups because the Italian offensive security firm HackingTeam had fallen victim to a hack themselves. After that particular vulnerability was disclosed in this fashion it ended up being used in several campaigns, among which there is an attack on the Ukranian power grid in late 2015. This attack resulted in power outages which lasted several hours.
Hashes are a vital part in every malware researcher's tool box. Specifically, analysts use so called 'fuzzy hashes' which can be used to identify unique portions of a file. They enable analysts to determine whether source code from other files has been reused in other places. This again allows conclusions as to how and what attackers have learned over time. After all, attackers are only human, and humans make mistakes which they try to correct at some point.
If you are interested in more information, head to the blog of G DATA Advanced Analytics to learn more.