Infection Vector
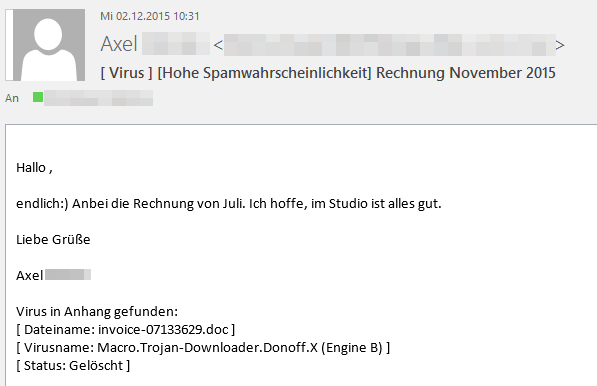
Similar to other Locky variants, it usually arrives through unsolicited e-mails:
• E-mail with office document attachment (e.g. .docx, .xlsx)
• E-mail with script-compressed archive attachment (e.g. .js, .wsf)
It is difficult to locate ‘patient zero’ or the origin of the first infected email, but rumors have it that there is a connection between the group responsible for the Dridex banking Trojan and the actors behind Locky. In 2015, speculations emerged that the two come from the same group of actors as there are many similarities in the way Dridex and Locky are distributed (both were spread through the Nuclear Exploit Kit which is used on infected websites) and in the way they go about infecting their victims.
Infection Chain

Infection Details
In most cases, malicious attachments employ sophisticated string obfuscation as part of its Antivirus evasion technique. An obfuscated file is not readable at first glance which makes its analysis somewhat more difficult. One should not make the assumption, though, that every obfuscated file is per definition ‘bad’.
There are also legitimate uses for this technique. In any case, files which were treated in this way (mostly VBA or scripting languages) enjoy a higher success rate in performing their malicious routine. High degrees of obfuscation also make it difficult for security companies to detect and analyze the scripts. When executed, the script contacts a predetermined compromised site to download the encrypted Locky DLL file. Downloading an encrypted binary file (as opposed to delivering it directly with, say, an email) is an important step in every ransomware infection. For one, it allows the actors to make changes to the binary 'on the fly'. This again boosts the chances of evading detection by security software. After downloading the DLL file, the script decrypts and executes the downloaded DLL using a legitimate Windows program (RUNDLL32.EXE) using the following command line (note that the routine will not performed unless an entry point for the DLL file is specified in the command):
Rundll32.exe %TEMP%\[dll_name].dll,qwertyAs soon as the Locky DLL has been successfully loaded, it immediately searches for target files with matching extension names and performs its encryption routine. Any file extensions can be targeted, including but not limited to the following list:
*.ycbcra *.cdr6 *.flvv *.mpeg *.ms11 *.sqlitedb *.cdr5 *.aiff *.qcow2 *.sldm *.sqlite3 *.cdr4 *.sas7bdat *.vmdk *.sldx
*.sqlite *.cdr3 *.indd *.wallet *.ppsm *.s3db *.bank *.design *.litesql *.ppsx *.psafe3 *.backupdb *.blend *.litemod *.ppam
*.plus_muhd *.backup *.xlam *.forge *.docb *.moneywell *.back *.pspimage *.d3dbsp *.potx *.kpdx *.agdl *.flac *.asset
*.potm *.kdbx *.accdt *.save *.tar*.bz2 *.pptx *.incpas *.accdr *.safe *.djvu *.pptm *.ibank *.accde *.pages *.jpeg *.xltx
*.grey *.vmxf *.laccdb *.tiff *.xltm *.gray *.vmsd *.html *.class *.xlsx *.erbsql *.vhdx *.config *.java *.xlsm *.ddrw *.vbox
*.aspx *.SQLITEDB *.xlsb *.ddoc *.qcow *.accdb *.SQLITE3 *.dotm *.db_journal *.nvram *.7zip *.onetoc2 *.dotx *.craw
*.m2ts *.mapimail *.lay6 *.docm *.cdrw *.groups *.contact *.ms11 (Security copy) *.docxIndicators of Compromise
Locky ransomware encrypts targeted files found in the following:
• Local directories
• Unmapped network shares
Encrypted targeted files are renamed using the following arrangement:
[generated_unique_id]-[calculated_encryption_of_filepath].[Locky_ext_name]
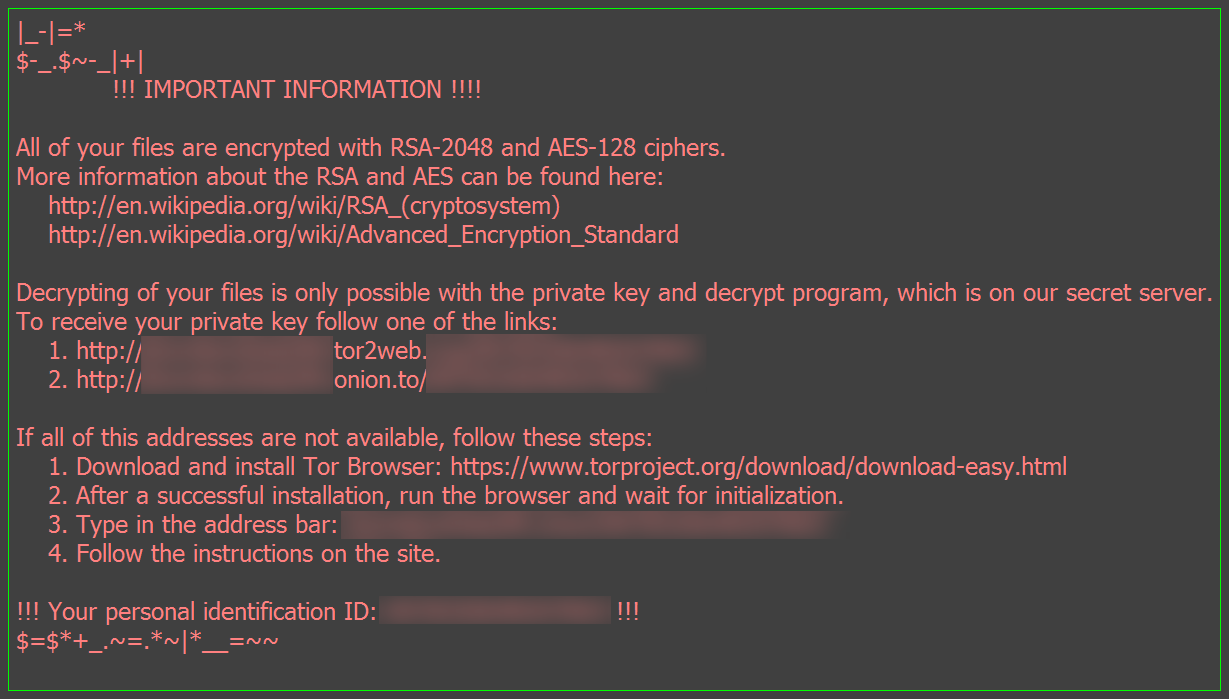
Ransom notes are dropped on every affected location to inform the user about the infection.
• [AFFECTED_LOCATION]\_{NUMBER}_HOWDO_text.html
• %DESKTOP%\_HOWDO_text.html
• %DESKTOP%\_HOWDO_text.bmp
The ransom note contains details about the infection and procedure on how to decrypt the affected files by paying the asked ransom. Locky then tries to connect to its C&C servers by establishing stable network communications through list of automatically generated domain names until a suitable reply was received.
Just as previous Locky variants, the new campaign does not have yet any known solution to recover the encrypted files. It also disables and deletes the Shadow Volume Copies in the system which makes file recovery impossible. Aside from using new extension name, it also changes the way it renames the encrypted data and refines its algorithm to catch more files. Luckily, however, no sensitive information or personal data is exfiltrated to the C&C server(s) throughout the course of the infection.
Conclusion
It has only been eight months since the first Locky ransomware emerged in the wild and it is already considered to be one of the largest ransomware threats today. Its ever-evolving sophisticated infection techniques and distribution mechanisms ensure that it will not go away again for quite some time. Locky’s latest iteration has made it clear again that constant vigilance and improved security measures are the most promising defenses against modern ransomware. Even though it only appears to be a minor update from its“.zepto” variant, Locky continuously broadens its infection and AV evasion capability. The AV industry on the other hand is continuously striving to catch up with recent malware development.
Information for fellow researchers
Script component:
69f2e30b1e7014872ef15a150fd280f2e00eeb0f2b660b4b0dcc2c2d9cc00560
Downloaded Locky DLL:
f5b5e92a59df1bed8414859e49480145aa2d40776c93a14ad981f4ea13f0f03e