The researchers at the G DATA SecurityLabs discovered a set of files which is associated with this new type of ransomware. Ransomware families such as Locky, CryptoWall or TeslaCrypt usually encrypt individual files. Petya targets the entire hard drive instead of individual files or file types.
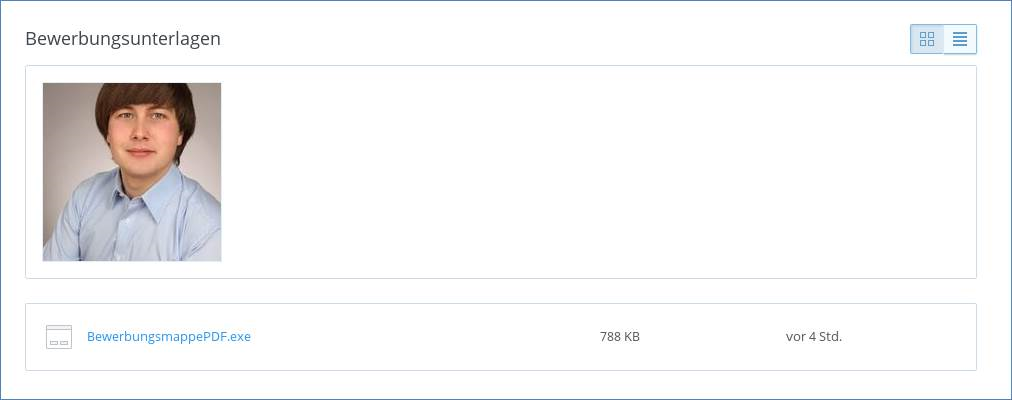
This malware campaign is obviously aiming at companies. In an email application which is sent to the HR department, a Dropbox download link is referenced where allegedly a ‘job application portfolio’ can be downloaded.
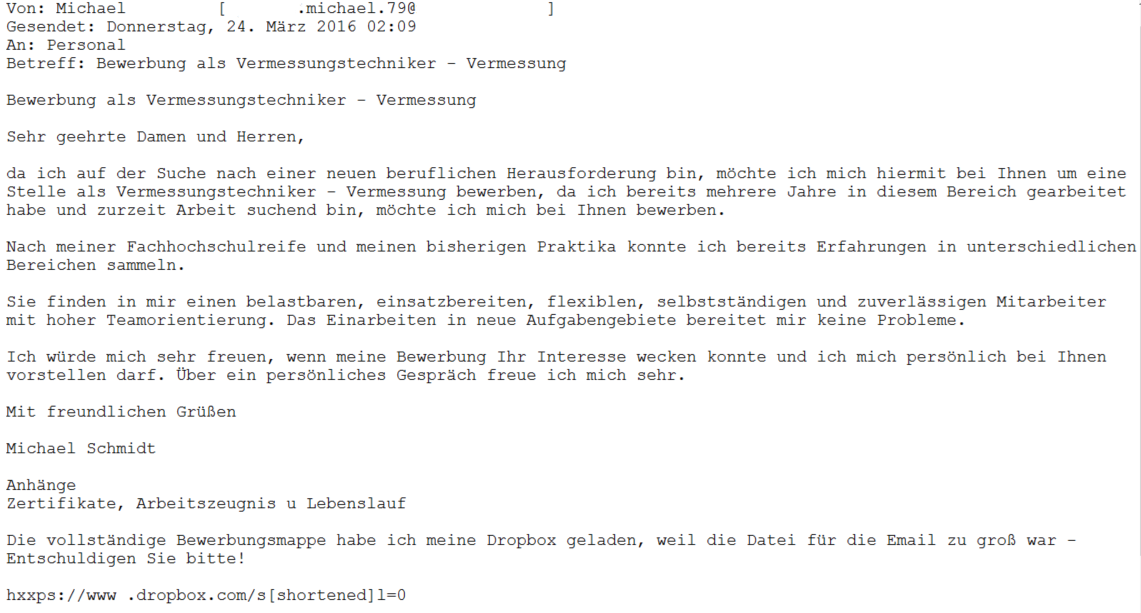
When following the link, an EXE file is downloaded. The German file name translates to ‚application_portfolio-packed.exe’.
When running the exe file, the PC crashes with a bluescreen and reboots. Prior to the reboot, the Master Boot Record (MBR) of the system is manipulated in a way which allows Petya to control the boot process. When the system restarts it displays the following:

This dialog claims to run a system check, but in fact this is the point where files on the PC are made inaccessible to the user. As of this writing we assume that the files are not encrypted but that only the file access is blocked but the files itself are not encrypted.
You finally notice that you made a mistake when Petya shows its true colors after the supposed system check is completed.

After pressing a key, further instructions are displayed.
To cover its tracks, the attackers behind Petya makes use of TOR.

On the website it is further claimed that the hard drive was encrypted using a „military grade encryption algorithm“. Further information shows how to obtain a decryption key and how to pay for it. After seven days the price for the decryption key doubles.
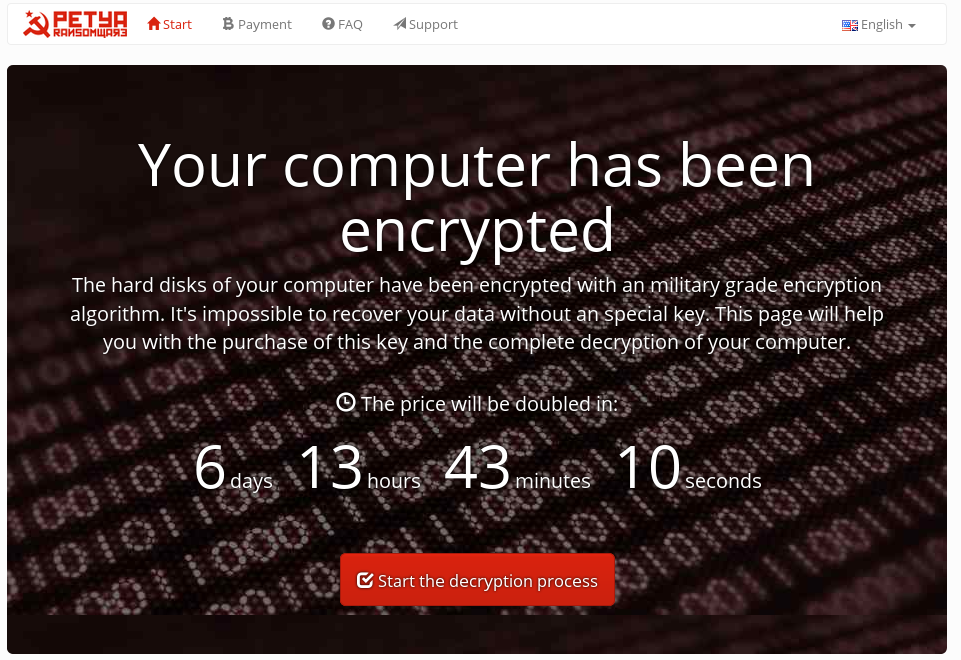
Petya in action:
As of this writing we assume that only the file access is blocked but the files themselves are not encrypted. Experts at the G DATA SecurityLabs are still analyzing this new type of ransomware.
G DATA Customers are protected.
Petya is detected as ‚Win32.Trojan-Ransom.Petya.A‘; the associated URLs have already been blocked. More information will be made available pending the completion of the analysis.
How to stay safe:
- Use a comprehensive security solution like G DATA Software security solutions
- Prevention: a working backup is vitally important. You can create backups with G DATA Total Security.
- Potential victims in an HR department should pay particular attention to the file type offered at Dropbox links. In this case, the file offered for downloading is an executable file instead of one or more documents, as one would rather expect when receiving an application. The point at which the supposed applicant expects the victim to download and open a file is the last point in time when an infection can be prevented.
- Should an infection have taken place already, disconnect the PC from the network. Don’t give up the data. As outlined earlier, it is still unclear whether or not the files on the hard drive can be recovered. We will post new information about this as it becomes available; a thorough analysis is still in progress.
- The ransom should not be paid
Update 31.03.2016 4p.m
Read our technial review of Petya ransome
Update April 1st, 2016, 12:00 pm:
A new Petya wave has been rolling for the past four hours. The malicious file is again stored in a Dropbox. An analysis is already underway.